Steemit Crypto Academy | Hash and Cryptography | Homework task for @pelon53
Hello All Steemians !!!
On this occasion, I will try to take a class at Steemit Crypto Academy. I am interested in joining this class because there are many new lessons that I will get here. I will do homework task from professor @pelon53. Lesson discussion about Hash and Cryptography. Lets try...
1. Explain what does the resistance to collision mean? And what does resistance to preimage mean?
In blockchain technology, Hash is very useful in terms of security which ensures data and privacy. Hash which is a unique algorithm makes the obtained information difficult to hack or find out. Each input will be processed with an algorithm that cannot be parsed, researched, or solved and produces a very safe output. This is a kind of manipulation in terms of hiding data or transaction information that enters the blockchain system.
Hash have the characteristics of being immutable, non-repeatable, and of a fixed length, making them very secure and efficient. The implementation and involvement of the hash function in the transaction process makes the input and output data highly controlled in the blockchain system. Until now the most widely used and best quality hashes are Secure Hash Algorithms (SHA) which include SHA-0 and SHA-1, SHA-2 and SHA-3, SHA-256.
a. Resistance to Collision
Hash functions is intended to eliminate or make it impossible for collisions between related inputs and outputs to occur. It is expected that it will not happen that every different input will produce the same output. In this case the hash has collision-resistant characteristics that make it very reliable and has an important influence in terms of maintaining the security of data to be found or hacked.
The hash will process the input into output using an algorithm to achieve the maximum in the work process and operations so that system errors do not occur. This is evidenced by the input of different lengths will produce outputs of a fixed length. This is because the input is infinite and the output is finite. This all aims to make it collision resistant in every data processing process in the blockchain system.
b. Resistance to Preimage
Hash functions are also intended to make data difficult to parse, research, or solve by looking at the output to get the input. It is expected that the determination of the input will not occur based on the output obtained. This is intended to prevent and discourage bad people from committing crimes that will harm. In this case the hash has the characteristic of resistance to preimage which makes it difficult to find a connection between the input and output.
Actions that intend to determine input data from output are abuse of rights and can harm others. Therefore, a hash function that is resistant to preimage is very suitable and useful for maintaining the security of the blockchain system from outside influences. This unique algorithm is the main factor that has an important role because determining the combination probability takes a long time and is almost impossible to complete.
c. Resistance to second Preimage
Hash functions also protects and maintains the data information of two or more different input data based on the same output. This is an advanced level of security that is set to be implemented to prevent any eventuality that might occur. This is technically nearly impossible because hash functions are also collision-resistant. But when it happens, the similarity of outputs can be exploited by bad people to determine different inputs so this function is valid and working properly.
2. Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking
a. Tronscan
Visit the web https://tronscan.org/#/. Select the last block to see all information.
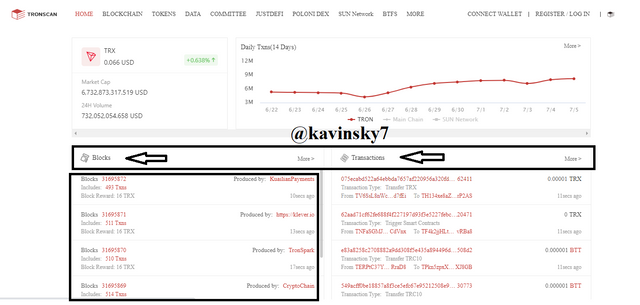.png)
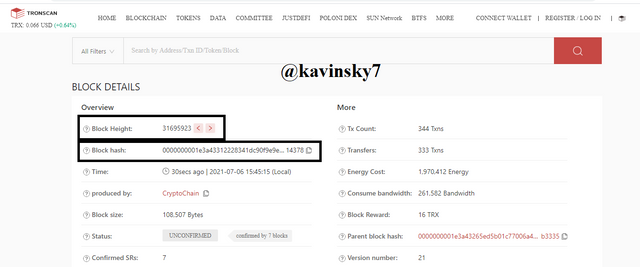
Tronscan Homepage In the black box I marked. Block Height: 31695923 and Block Hash: 0000000001e3a43312228341dc90f9e9e...14378.
Tronscan Block Return to previous page. Select the last transaction to see all information.
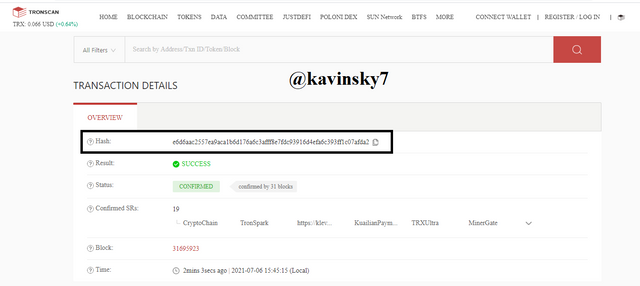
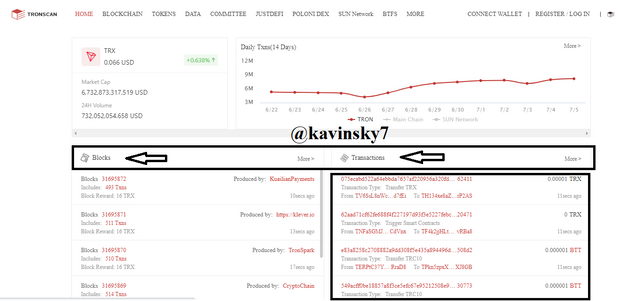.png)
Tronscan Homepage In the black box I marked. Hash transaction : e6d6aac2557ea9aca1b6d176a6c3afff8e7fdc93916d4efa6c393ff1c07afda2.
Tronscan Transaction
b. Etherscan
Visit the web https://etherscan.io/. Select the last block to see all information.
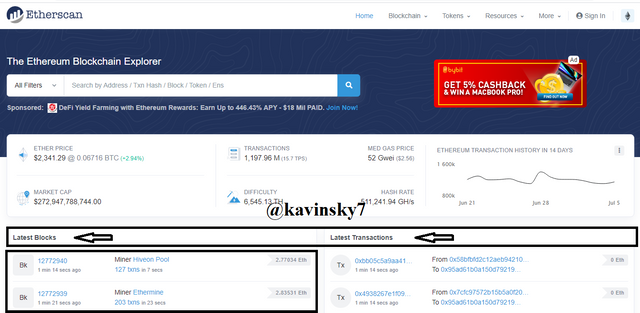.png)
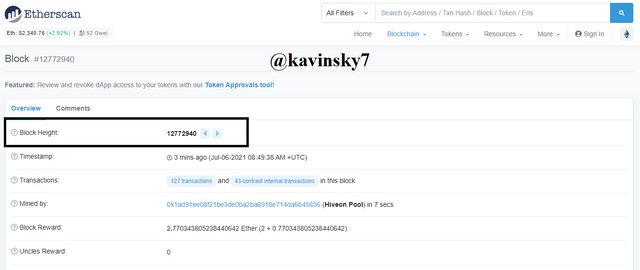
Etherscan Homepage In the black box I marked. Block Height: 12772940.
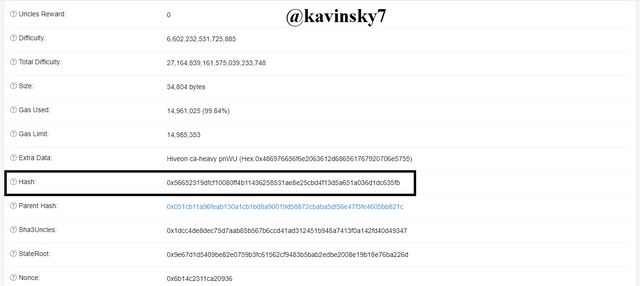
Etherscan Block See more information below. In the black box I marked. Block Hash: 0x56652319dfcf10080ff4b11436258531ae8e25cbd4f13d5a651a036d1dc635fb.
Etherscan Block Return to previous page. Select the last transaction to see all information.
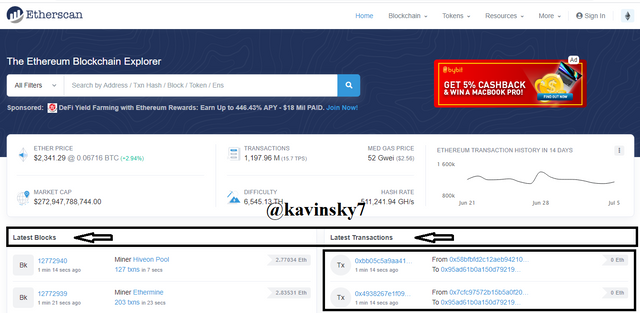.png)
Etherscan Homepage In the black box I marked. Hash transaction : 0xbb05c5a9aa41dde9dd0e07c5a0fc208832b383497b6fdbf16492a601211c4d6.
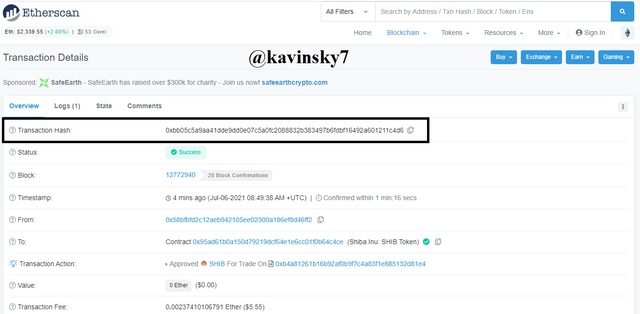
Etherscan Transaction
3. Generate the hash using SHA-256, from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain
Visit the web https://passwordsgenerator.net/sha256-hash-generator/. Type "CryptoAcademy" as the first example. Hash : D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9.
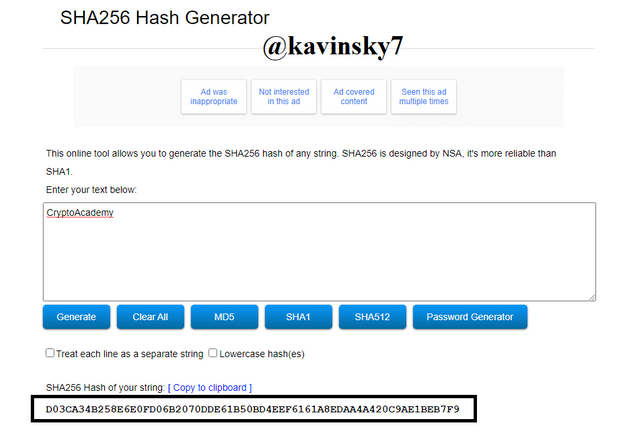
SHA-256 Hash Generator Repeat and type "cryptoacademy" as the second example. Hash: 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5.
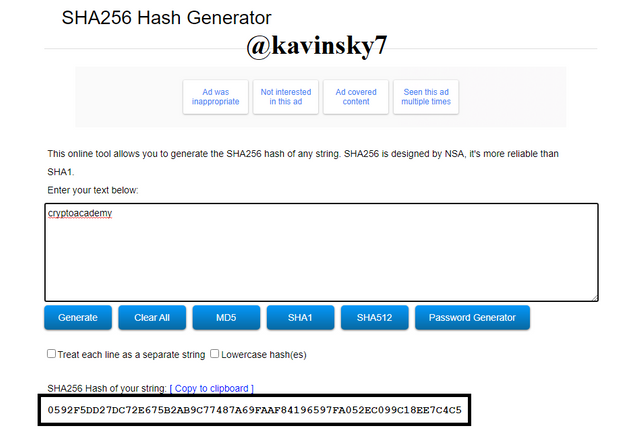
SHA-256 Hash Generator
The two examples above confirm and provide evidence that hashes are immutable, non-repeatable, fixed-length algorithms. Each input that has the slightest difference will make the output different. This is evidenced by the example of the same word but has a difference in the application of capital letters to the letters "C" (crypto) and "A" (academy). Whatever differences exist in the input will affect the output. This is a simple example that has a big meaning. Therefore hashes are very feasible and suitable for use in blockchain systems in terms of security because of excellent characteristics.
4. Explain the difference between hash and cryptography
Hash
- A tool that produces algorithms that are unique, immutable, non-repeatable, and of fixed length.
- Work with the process of verifying input data, processing by providing algorithms, and producing safe output.
- Functions for resistance to collision and preimage by relying on an algorithm that cannot be parsed, researched, and solved.
- Makes data invisible, unknown, unreadable, unpredictable, and unhackable.
- No password required.
Cryptography
- The method used to provide a high level of data security and privacy.
- Functions in managing and hiding information about all security-related blockchain systems.
- Prevent the involvement of bad people or other parties in all transaction processes that occur.
- Allows encryption and decryption process.
- Requires a password.
Based on the main function of hashing and cryptography, it is the science and method applied to the blockchain system in keeping data and important things safe that other people don't know. This is an effort to prevent abuse and hacking. So here hashes are the tools used and the science implemented to make them hard to beat or break by relying on algorithms. This method is one of the methods contained in cryptography in terms of maintaining the security of blockchain systems involving data and user privacy.
Conclusion
In the world of cryptocurrency, security is a major factor and an important point to consider. User contributions are still very much needed to make cryptocurrencies continue to grow. Therefore, the security of the blockchain system is very concerned and becomes an influencing factor.
The application of hash and cryptography is very appropriate and feasible to use because it has good characteristics and ways to increase user trust and convenience. Hash functions and cryptography both benefit users in terms of data protection, privacy, anonymity and other important matters. These are all created and developed to prevent bad guys from doing abuse and hacking.


Excelente trabajo, muy didáctico la explicación, claro hay que estudiarlo poco a poco, para entenderlo mejor, saludos desde Venezuela
👆 En realidad no es a eliminar ni hacer imposible las colisiones, sino que las probabilidades sean mínimas. Difíciles que ocurran, pero siempre pueden ocurrir.
Buen trabajo, continúe mejorando, felicitaciones.
Recomendaciones:
Debe explicar los conceptos entendiendo bien lo que explicas.Calificación: 9.5