Crypto Academy / Season 3 / Week 2 - Homework Post for Crypto Professor @pelon53
Hi Steemians, this is my homework post for Professor @pelon53 on Hash and Cryptography.
Explain what does the resistance to collision mean? And what does resistance to preimage mean?
Before I begin, I need to lay this foundation on Hashing.
Hashing is a process of converting an input of any length into a fixed sized string of text using a mathematical function.
This means that any input, no matter how long, can be converted into a fixed numbers and letters through an algorithm.
The message to be hashed is called an Input, the algorithm used to do so is called Hash Function and, the output is called Hash Value.
There are many formulas to be used to hash a message (example; SH-512, SH-1, CRC35, MD2, Tiger, Adler35 etc)
But a cryptographic hash function needs to have some of the following qualities to be considered useful.
1. Unique Hash Value.
Each has value or output has to be unique. This means it will be practically impossible to have same hash value, having entered different inputs.
And therefore, the same message should always produce the same hash value.
2. Hashing Speed.
This is also an important factor. The hash function should be able to produce a hash value faster.
3. Secure Hash.
The hash function needs to be secure. It is extremely difficult if not impossible to determine the input base on the hash value, while a slightest change to an input to generate a highly different hash value.
Collision Resistance.
This is one of the major product/properties of cryptographic hash functions. Hash Function has made it very difficult for hash values of different inputs to collide.
In otherwords, two inputs A and B where "A" is not same with B but, "H" is same with another "H".
However, the harder it is to find, the more cryptographically secure the hash function becomes.
Preimage Resistance.
This is also a product/property of hash function which is hard to invert. That is, an element in the range of hash function, should be computationally infeasible to locate inputs that maps the said element.
Here, it is mathematically/computationally impossible to revert to the original text. It's a one way function.
Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking.
Verification of the hash of the last Block and the Transaction on tronscan.
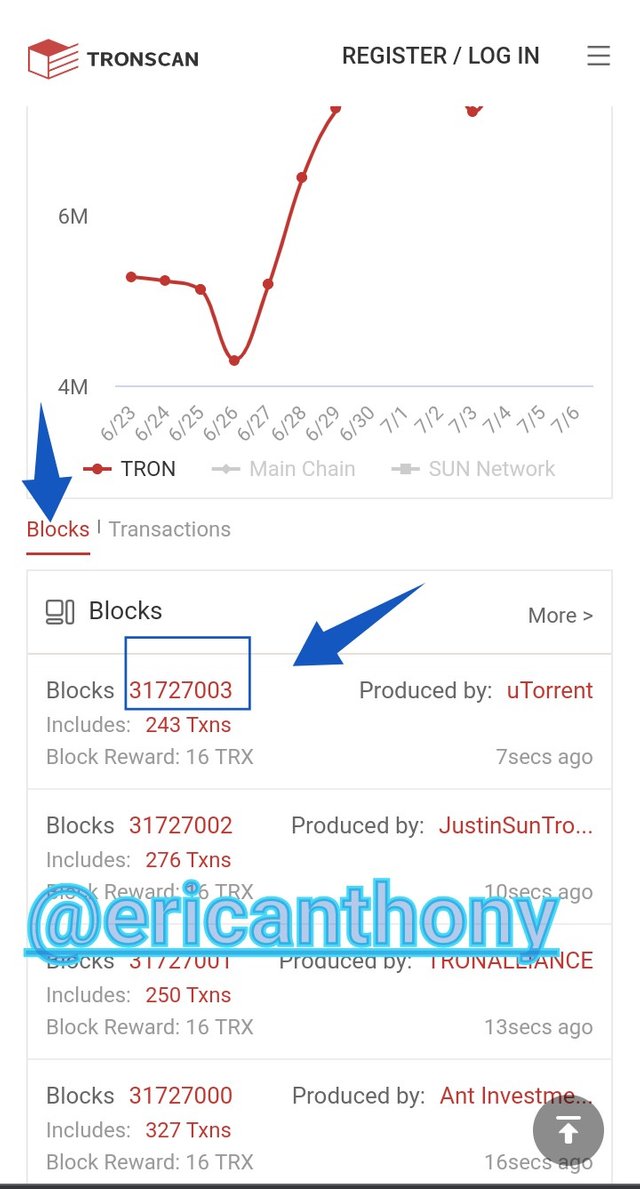
Go-to Tronscan, scroll down and click on the last block.
The last block was 31727003
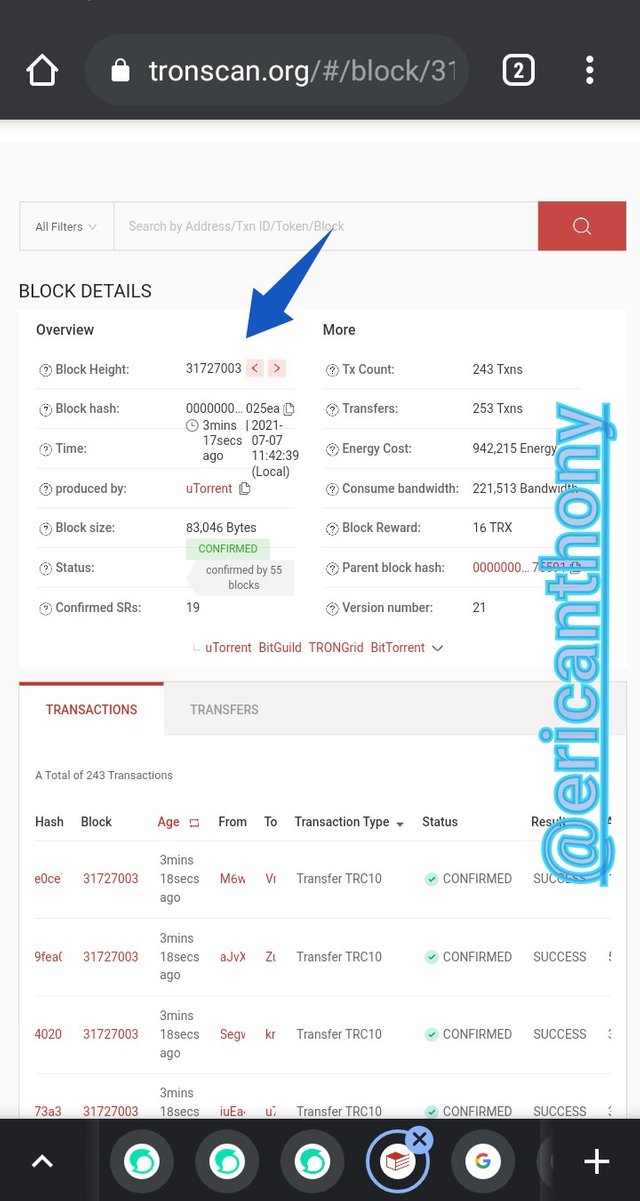 source
source
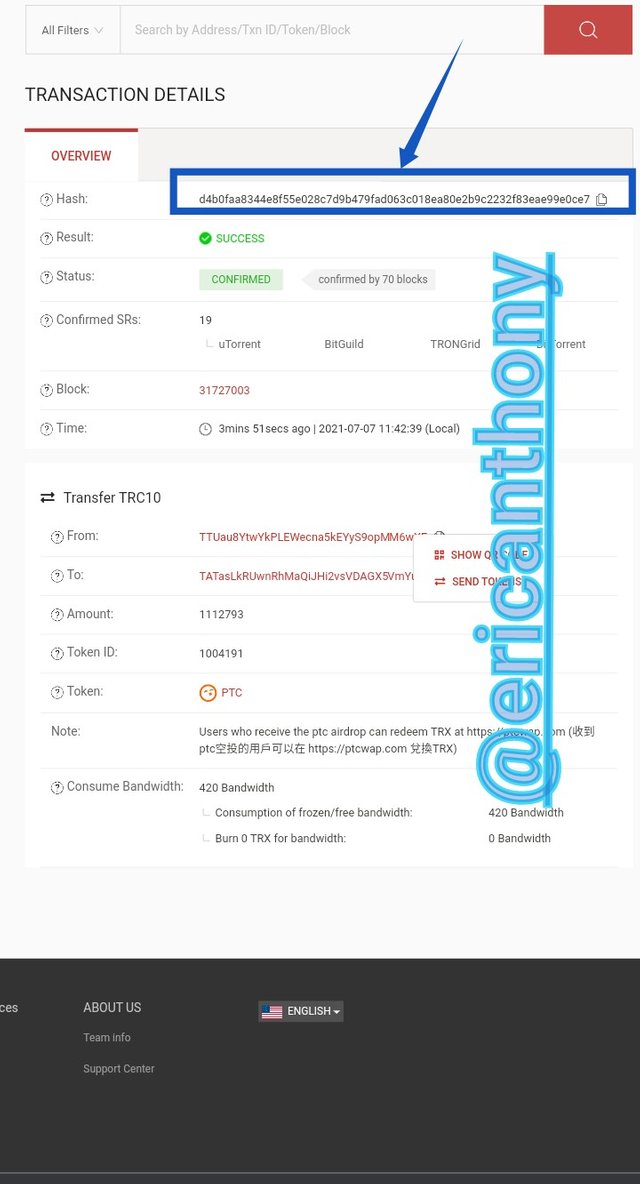
Scroll down again and click on the block under Transaction Details to view the hash(d4b0faa8344e8f55e028c7d9b479fad063c018ea80e2b9c2232f83eae99e0ce7) of the block on the transaction details.
Verification of the hash of the last Block and the Transaction on etherscan.
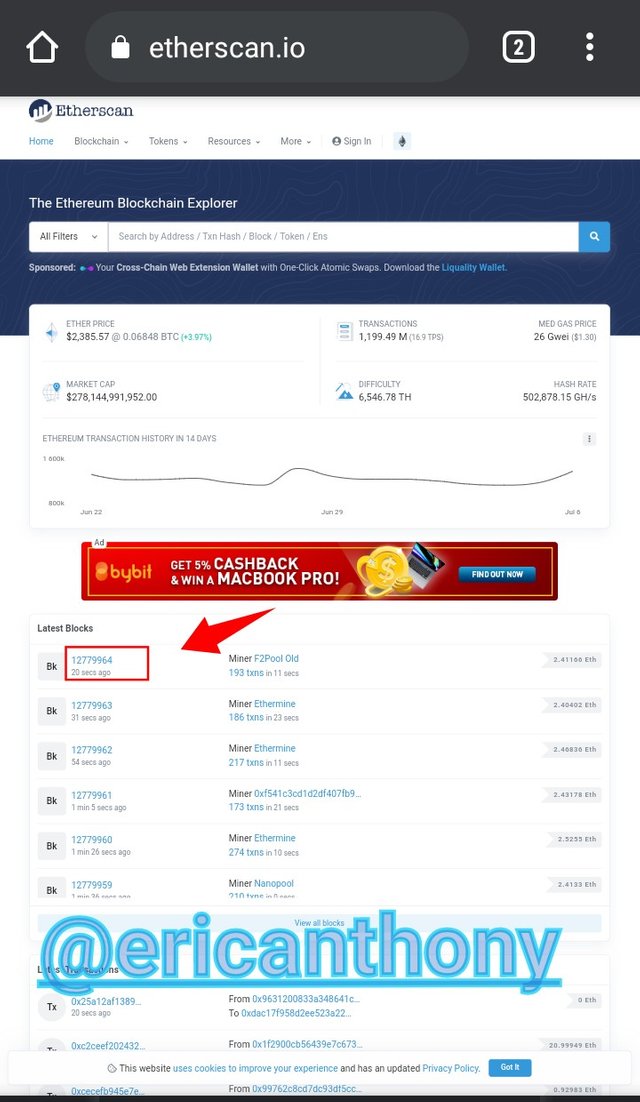
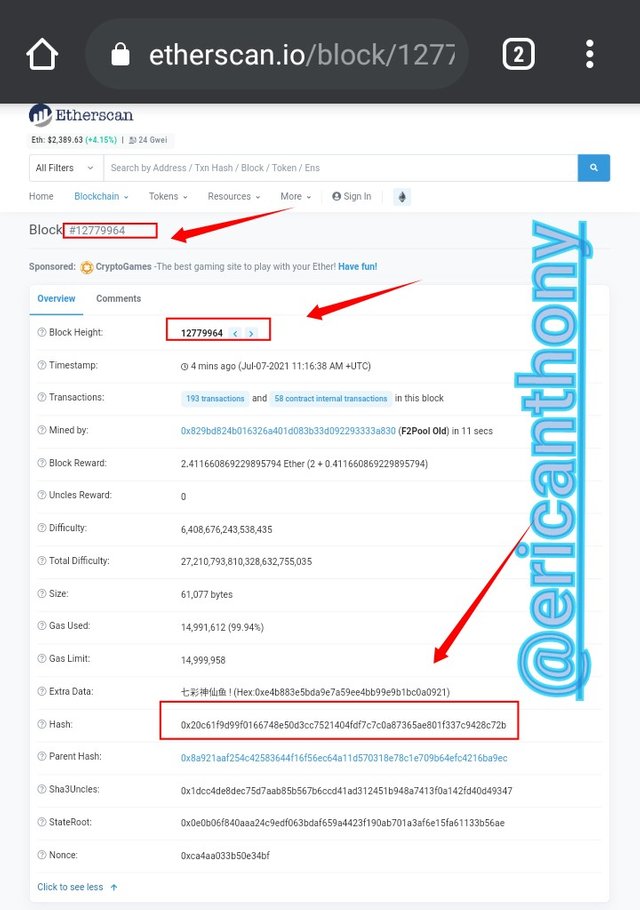
Go-to Etherscan, scroll down and click on the very latest block. Which was 12779964.
Click on the block to display the block details, of which the hash value is 0x20c61f9d99f0166748e50d3cc7521404fdf7c7c0a87365ae801f337c9428c72b
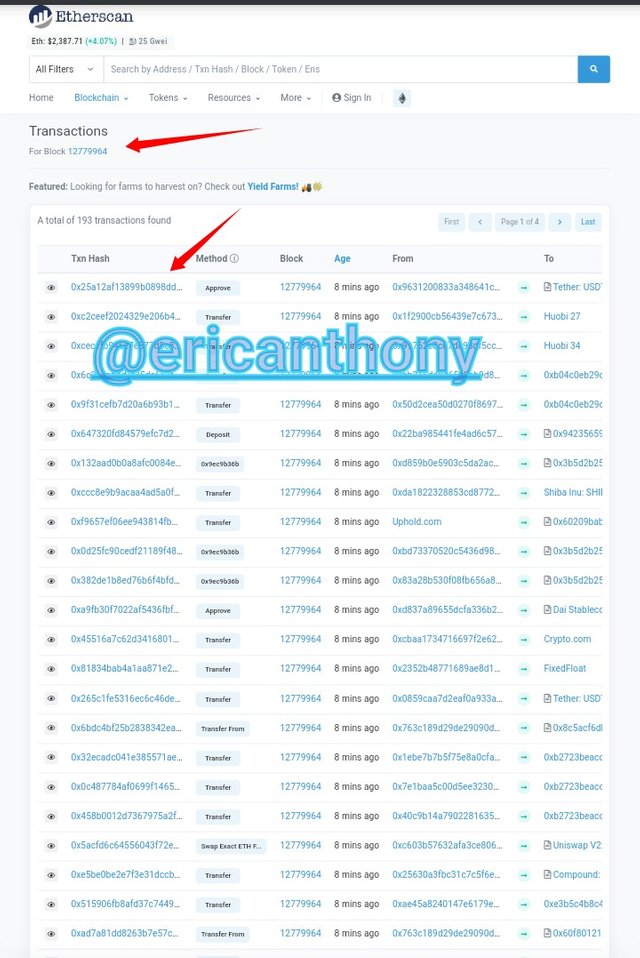
The block details on display having clicked on Transactions.
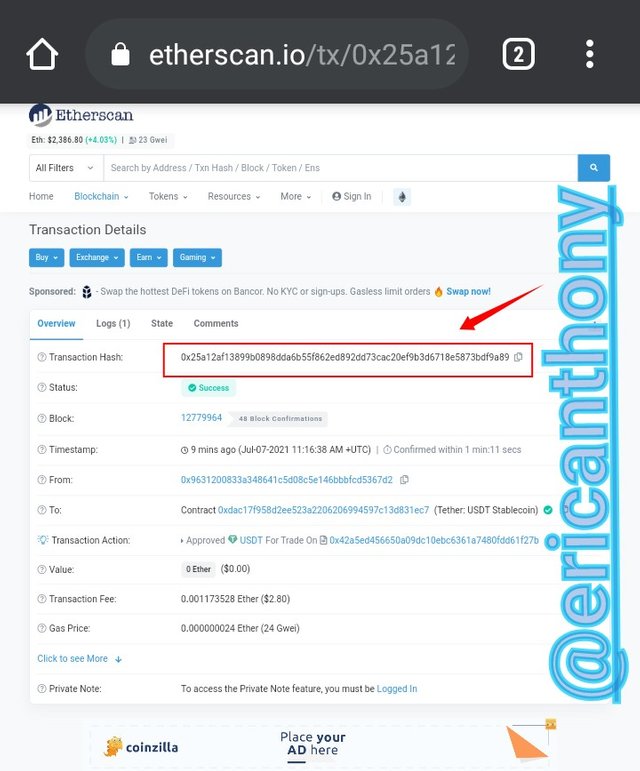
Click on the first transaction hash to view it's details. Transaction Hash 0x25a12af13899b0898dda6b55f862ed892dd73cac20ef9b3d6718e5873bdf9a89
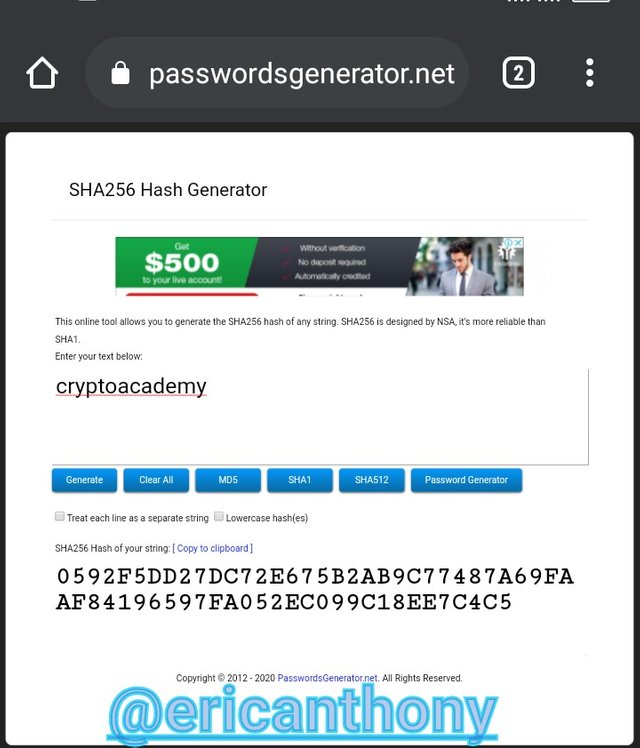
Generate the hash using SHA-256 , from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.
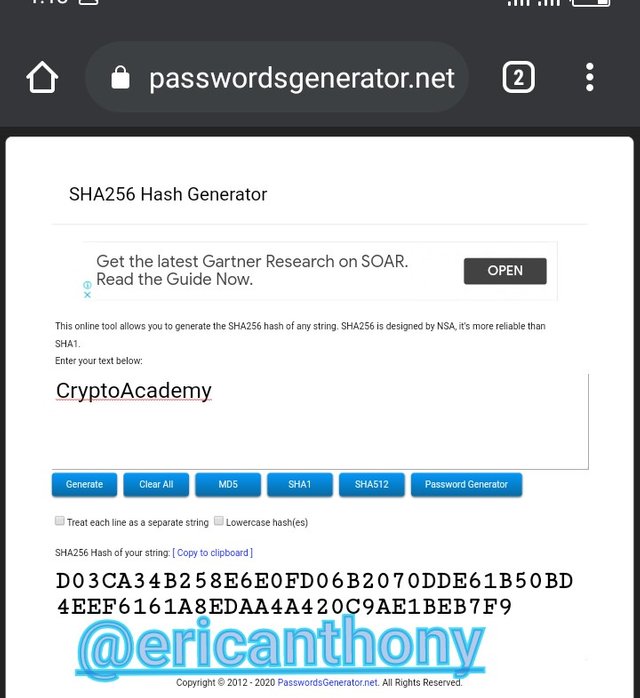
Using SHA256 hash generator.
CryptoAcademy generated:
D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9
While cryptoacademy generated a different hash: 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5.
The differences in the hash value generated is as a result of the working mechanism of the Hash Function.
Since there are differences in the letters, though they may mean the same and also has same number of letters, hash function will still generate a different hash value because, SHA-256 will make sure that the two different words don't collid and it will be very difficult if not impossible for collision to occur.
This has also brought to light that in Hash Function "A" is not same as "a".
In your own words explain the difference between hash and cryptography.
Hash Function.
Hash values are determined by the data/input being hashed.
It uses all the entry/input data.
It uniformly distribute all the data across the entire hash values.
It generates different hash values for similar inputs
Cryptography.
Information can be accessed by only the person it is intended.
Information cannot be modified between the sender and the receiver.
The sender of the information cannot deny his/her intention to send the information in future.
It confirms the identity of the sender and receiver.
Summery
Hashing is very useful in many ways. The cryptographic hash functions is very useful in IT.
It is used in the message authentication code and also very useful in file identification, data indexing in the hash tables, duplicate data dictation and security purposes. The list goes on.
.png)
Hi @steemcurator02, just want to remind you that my assignment has not been curated. Thanks.
https://steemit.com/hive-108451/@ericanthony/crypto-academy-season-3-week-2-homework-post-for-crypto-professor-pelon53#comments