CRYPTO ACADEMY SEASON 3 WEEK 8 | HOMEWORK POST FOR @stream4u - LETS OPEN THE CRYPTOGRAPHY by @eloksjoseph
INTRODUCTION
Hi guys , welcome to the last week of steemit Crypto Academy Season 8. Today I'll be exploring the cryptography.


Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms (Few names of the Blockchain Platforms)?
.jpeg)
Source
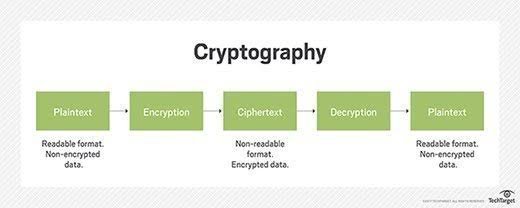
Cryptography is a secure form of communicating between people. It involves sending an encoded message that is only viewable by the people authorized. It is an efficient way of sending information in a safe way .
Blockchain cryptography is a type of private type of technology used in Blockchain. It is a method of encrypting data that doesn't allow unauthorized users view a specific form of data. Blockchain cryptography is adopted in Blockchain technology in securing data,it can be called encryption of data. To be able to decrypt data, you'll need a key. Only those with this key can decrypt the data.
Some Blockchain platforms include;
Binance smart chain
Ethereum chain
EOS blockchain
Tron blockchain
Steem blockchain

Explain the Public Key CryptoGraphy.
We already understand that cryptography is a form of sending encrypted messages from the sender and the receiver would decrypt the message to be able to read it. The key responsible for converting the message into an encrypted form is the public key. This public key can be made known t everyone.
It works hand in hand with the private key. While the public key encrypts the message, the private key converts it back to readable form. Public addresses are conned out using public keys. The public address enables us to send and receive tokens.

Explain the Private Key CryptoGraphy
The private key unlike the public key should be kept private. This key is used in the decryption of the messaged sent to the receiver. Only the sender and receiver would have this key.
When the message is send and encrypted using the public key, the private key is used to decrypt the message into the firm readable by the receiver. Private keys are also used in securing wallets. These private keys keep the wallets safe and once shared, the wallet us under risk. The private key is also used to validate transactions.

Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
When we do real life transactions,we often require some kind of authorization, whether verbal or written. The same applies in cryptography. There is a form of authorization that is required for each transaction. This is the digital signature.
The digital signature is gotten from the private key . When a transaction is initiated, a signature is formed and then the end product is sent to a verifier before the transaction can be completed.
SIGNING A TRANSACTION
To validate or complete a transaction, it must be signed and verified. Both the public key and the private key. For each transaction, you need to sign it for approval. Then you'll send the approved transaction to the other person to verify it.
From this,we can pick out that each transaction needs two things; signing and verifying. The private key would be used to generate a signature, the transaction would be signed and sent to the verifier who would verify the transaction before it is completed.
Explain what is Symmetric and Asymmetric cryptography
SYMMETRIC CRYPTOGRAPHY
.png)
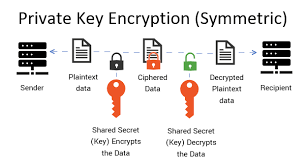
When something is said to be symmetrical, it means it is singular or it consists of only one thing. That said,if we link it to cryptography, we can say that symmetric cryptography is the type of cryptography that involves the use of just one key for encryption and decryption. That is, in
symmetric cryptography,one key is used to both decode and encode a message.
In the symmetric cryptography, the single is often shard between the sender and receiver of the transaction. It is best kept private and within both sender and receiver because if the key is exposed to the public, the transactions privacy would be endangered and the entire essence of cryptography tarnished as it is no longer private.
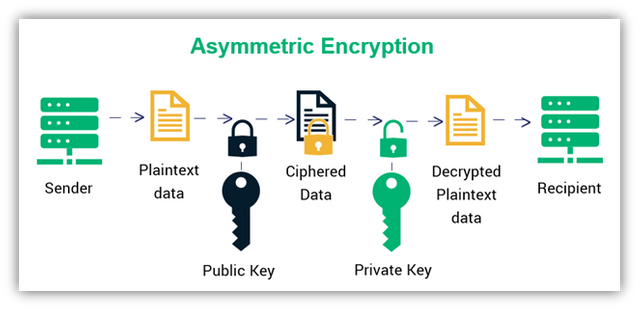
ASYMMETRIC CRYPTOGRAPHY
On the other hand, asymmetric cryptography uses more than one key . That is, both the public and private keys. The public key is used to encrypt the transactions made and the private key is used to decrypt the transaction.
Unlike the symmetric cryptography where both sender and receiver holds the key, here, the sender holds the public key and the private key is held by the receiver.

How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
Blockchain wallets are like our real life wallets,just safer. We use the blockchain wallets or digital wallets to store our digital currencies. Digital wallets also allows the owner to send and receive digital assets .
Blockchain wallets uses Blockchain cryptography in the sense that it has keys for security. The keys that every wallet has is called the private and public key. The private key should be kept in secret because if it is hacked or exposed, the person can have access to all your account.
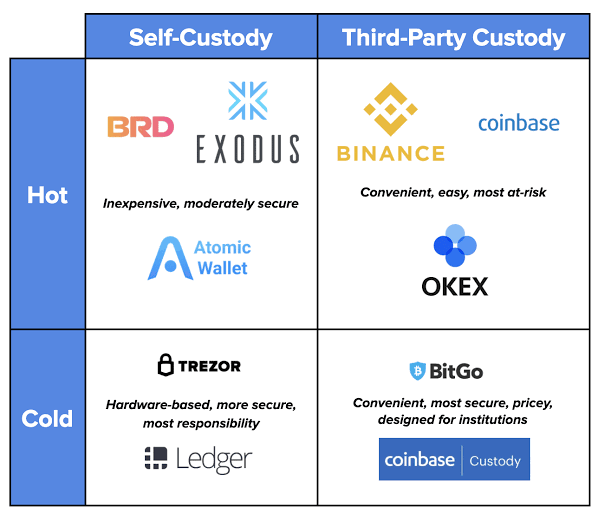
There are 2 types of crypto wallets;
COLD WALLETS
These wallets are offline wallets. That is , they're not connected to the internet. It is impossible to hack as it is offline and long term coin holders often prefer using these type of wallets . It is also convenient to carry about as sometimes it's size is about that of a USB.
To access your wallet, all you need is to connect this wallet to your computer and you can easily access your coins. One major disadvantage is that it is small and it can easily get missing. Some cold wallets include;
- Ledger
- Trezor
- Cold card, etc.
.jpeg)
A COLD WALLET
HOT WALLETS
These are online wallets. They involve connection to the internet. This type of wallet is prone to hacking as it is connected to the internet. Most long term holders don't use this type of wallet.
In this type of wallet, it is easy to send a receive tokens using your public address and private address. Some hot wallets include;
- Trust wallet
- Atomic wallet
- Blockchain wallet, etc.

What is the Merkle trees and What its importance in blockchain?
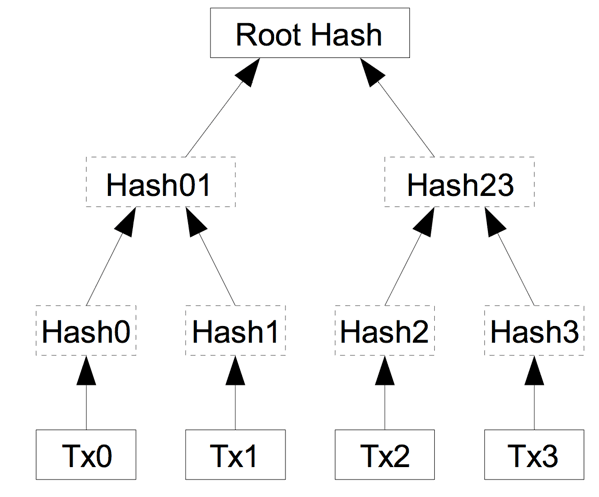
DIAGRAM OF A MERKLE TREE
The Merkle tree was invented by a computer scientist called Ralp Merkle in the 70s. The Merkle tree is a way of storing data in a block chain. As the name implies, the data is stored in form of a tree. Just as normal trees are made of leaves and branches, the hash tree or Merkle tree comprises if hashes and blocks.
The hash tree consists of 3 main parts head( root hash), branch ( parent node) and leaves (transaction hashes ). The leaves join together to form the parent node ,which in turn comes together with other parent nodes to form the root hash.
Some importance of the Merkle tree include;
- Easier validation of blocks.
- It reduces data storage as it is organized.
- Records transactions in blocks.
- Reduced time in verifying transactions.

Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
In this section, I'll be exploring the site. Without further Ado;
- KEYS
From our underlying knowledge, we already know what private and public keys are. They often contain both numbers and alphabets. Let's generate keys using the demo links above.
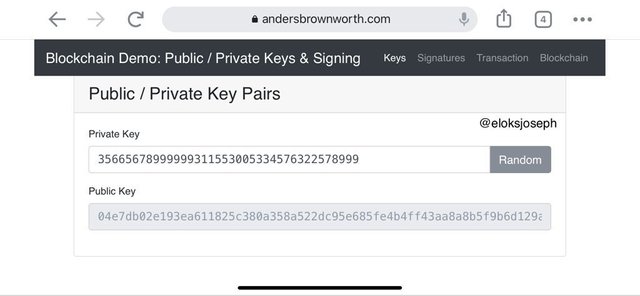
From the screenshot above , we can see a random private key and a random public key.
To show that every public key has its own public key unique to it alone, I tried changing the last 5 digits and we can see an obvious change in the public key.
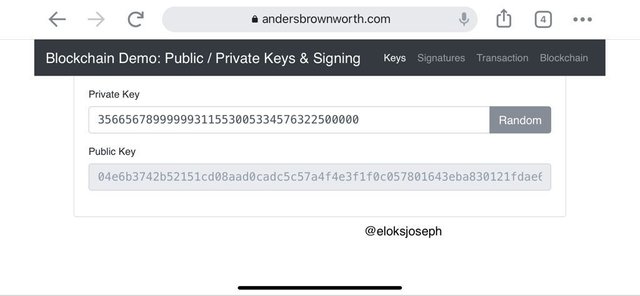
This is an example of of asymmetric cryptography as it has a private key and a corresponding public key. If we pick another random private key, the public key is seen to change.
- SIGNATURE
Signatures are used for verifying the transactions made on a blockchain. Let's type a message and check the private key used in signing the message.
I'll be input the words " what a world"
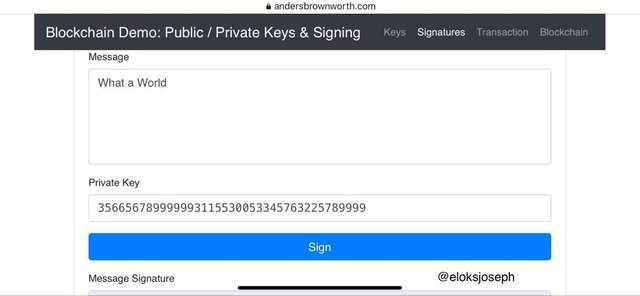
With a random private key, I'll click sign and you'll see the message signature .
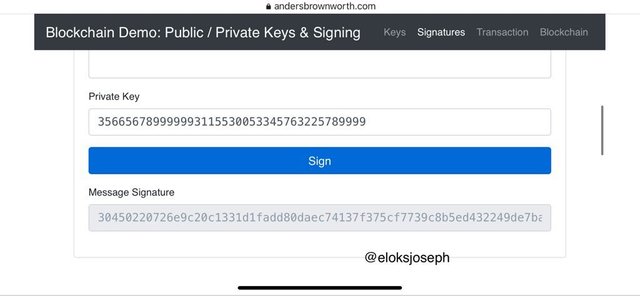
Click to the verify tab to verify the message.
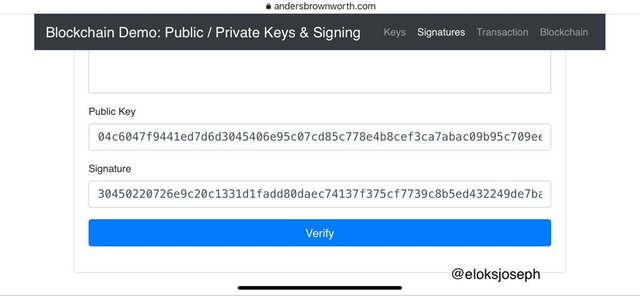
The message has now the been verified.
On the other hand,if any changes are made to the message,it won't be verified. See an example. Note the red background:
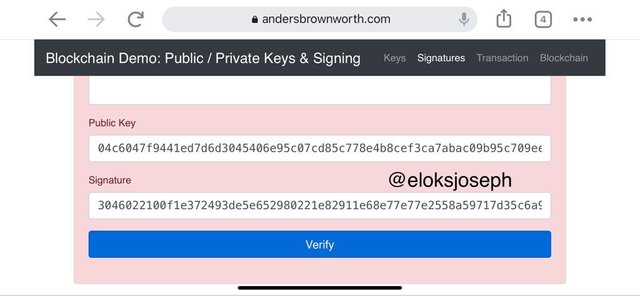
Signing messages helps prevent unauthorized modification if messages and it also helps maintain authenticity of the message. It is a way of securing transaction between both parties both sender and receiver.
- TRANSACTION
To validate transactions, we make use of the public and private keys. Let's perform a demo transaction. I'll be sending $100 to a demo user.
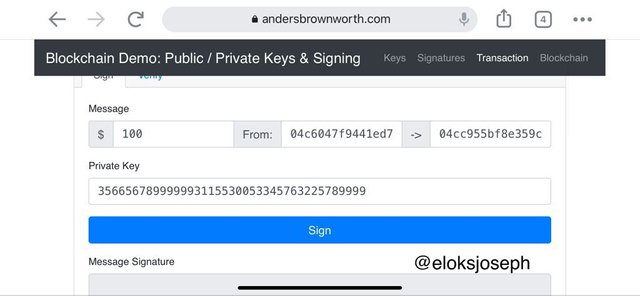
Sign the message so we can get the message signature.
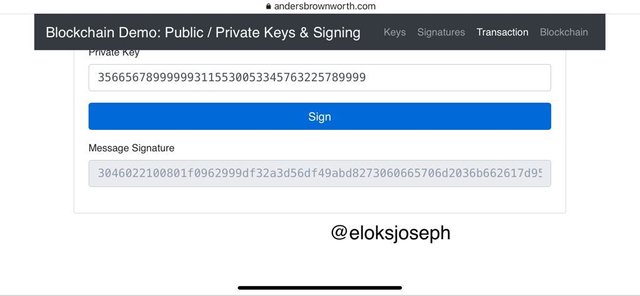
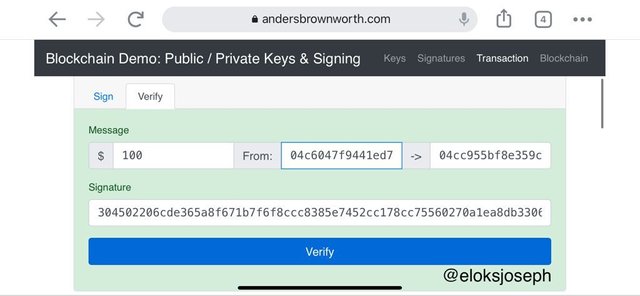
Next is to move to verify tab to verify the transaction.
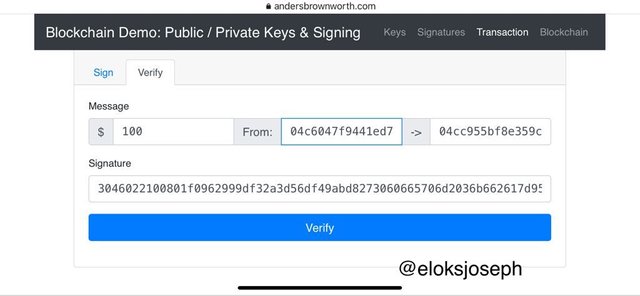
Now the transaction has been verified.
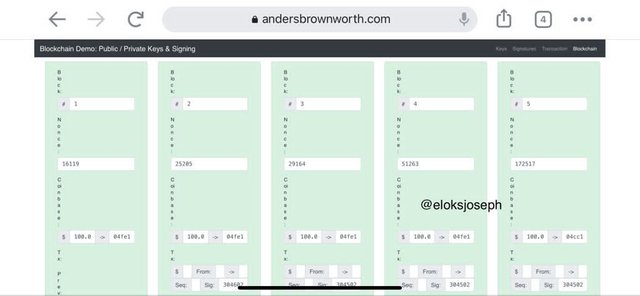
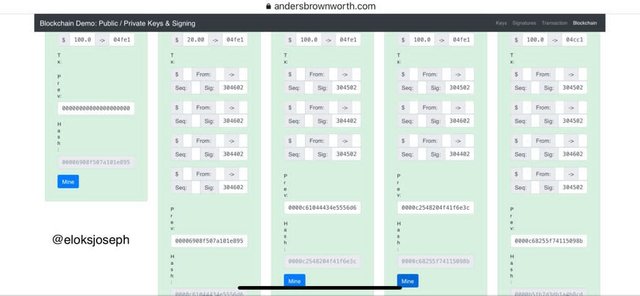
- BLOCKCHAIN
This is where validated transactions are stored. It has every information of things happening.
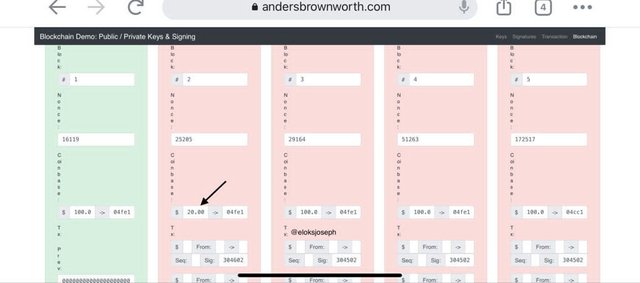
Let's say we try to change the information on the 2nd block, the interface changes . This shows that the blocks are in a chain so if you change the information,it affects the others.
Now let's try remining the second block and the corresponding blocks.
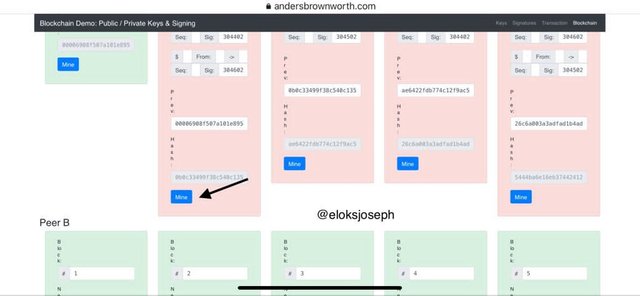
As you can see the interface has changed again.

CONCLUSION
Blockchain cryptography is one of the reasons many people engage in Blockchain transactions as it's technology is very secure and very impossible to hack.
This level of security is important as our digital currencies and assets are stored with this technology.
Thank you professor @stream4u for the lecture.
.png)