Steemit Crypto Academy S5 - The Genesis Block - Homework Post for Task 3
(03)
a) What is a Cryptocurrency?
b) What is Cryptography and how does it make cryptocurrencies secure?
c) Explore the Steem Genesis Block and Sign in as proof of completion.

a) What is a Cryptocurrency?
- Basic Introduction of Cryptocurrency.
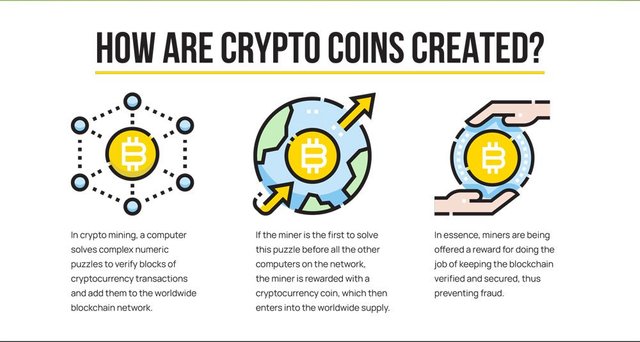
Cryptocurrencies were born as a substitute for fiat money, which was centralized and controlled by state-owned banks. Thus, a crypto asset is a digital currency operating under Cryptography. That is a very secure method that cannot be copied or modified again and again. This is happening thanks to the decentralized blockchain in which they operate, and there is no one to control it. All of these crypto-assets transactions are secure and, from their appearance, do not operate under government oversight, private institutions, or banks that allow their consolidation. It gives its owner the ability to easily transact from anywhere in the world under complete freedom without any hindrance.
- History of Cryptocurrency.
Its historical editing began in 1983 with a long process, and he began with David Chaum, an American who expanded a cryptographic system called eCash. Then in 1995 DigiCash was founded. Therefore, in 1996, the United States National Security Agency created a collective site for a detailed investigation of the cryptocurrency system.
According to this in 1998 the engineer Wei Dai makes the description of the ideas of cryptocurrencies, this idea of Wei was based on the foundation of generating a digital currency that was in such a case based on cryptography and that it controlled him; however, it is until 2009 when the first cryptocurrency is born and inserted into global markets if the new digital asset would receive the name Bitcoin by its creator Satoshi Nakamoto after that moment that broke paradigms in the various markets, countless cryptocurrencies emerged, some booming, and others with full similarity to Bitcoin.
This Bitcoin is arguably the world's first cryptocurrency, and today a large number of cryptocurrencies have joined the network following in the footsteps of Bitcoin. That cryptocurrency is what we commonly call altcoins such as Etherium, Binance Coin, Cardano, and other major cryptocurrencies.
- How These Cryptocurrencies are Created.
Mainly, all of these Cryptocurrencies are created on a blockchain whether it can be an own blockchain or depend on another blockchain. As an example, Etherium coin has its own Blockchain that is known as Etherium blockchain. Then, SHIB Inu Token is created on Etherum blockchain that means SHIB Inu doesn't have their own blockchain yet.
In this way, Cryptocurrencies follow their own specific method to secure every transaction. That can be defined as Cryptography which we briefly describe next.

b)What is Cryptography and how does it make cryptocurrencies secure?
- What is Cryptography
Cryptography can be described as the basic method of providing complete security to the communication that makes up the computer world. Certainly, this happens thanks to the algorithms or systems that use it to maintain such functionality. In this case, in addition to implementing, designing, and implementing its basic requirements, it uses a unique methodology to protect cryptographic systems as well as to protect information and secure communications. That is the encryption and decryption method. It simply converts a message so that it cannot be recognized by an intermediary before sending it. The recipient must then convert the message to a readable medium.
- how does it make cryptocurrencies secure?
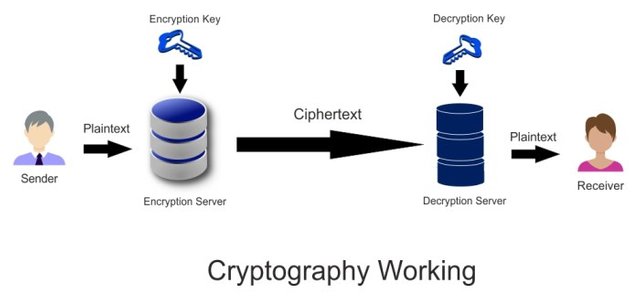
From the outside, this is a very simple method. I will describe this process simply using a diagram that I took from the Internet.
There are 4 main parts for this process including the sender, Public key, ciphertext, Active key, and finally the receiver.
Sender means the person who readies to send relevant data. At the same time, the Public key is the receiver's address and it can be defined as the address to which we send data or crypto. Then, the ciphertext is the data that is converted to unreadable for an external party.
If I explain the process of this method, firstly the sender should use the receiver's public to generate encrypted code for this data before transmitting it within the network. After that, it can be defined as the ciphertext and it will be transmitted to the receiver. Here the most interesting thing is that the receiver must use his private key to decrypt these data. Therefore, if an external party or a hacker breaks the mid path and Steals our data, he can't read these data without the receiver's private key. That's why this will be the safest method in the world for transmitting data within public networks.

c) Explore the Steem Genesis Block and Sign in as proof of completion.
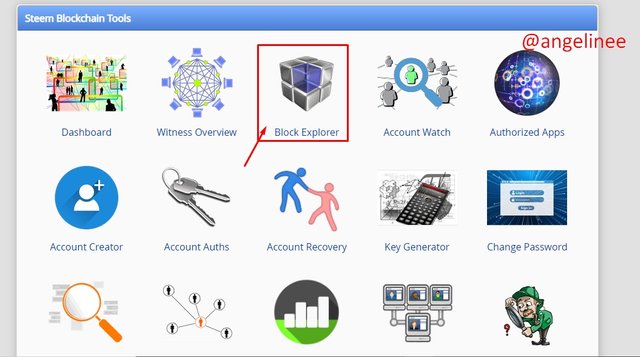
As the first step, I will access to https://steemworld.org website. Here I need to find the "Block Explorer" section for opening Steem Genesis Block.
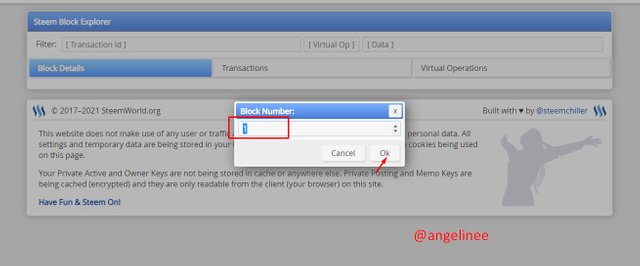
So, now I will select number 1 and click ok to open the first block.
Here I can get all the information related to Steem Genesis Block as follows.
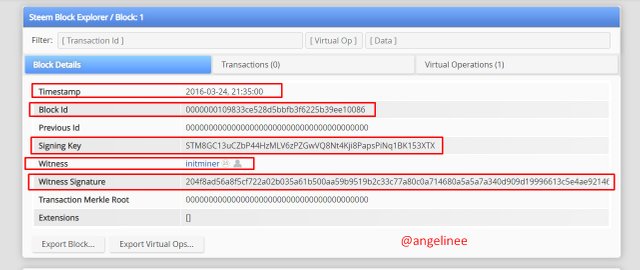
Finally, I will sign in as proof of completion by clicking on "sign in".
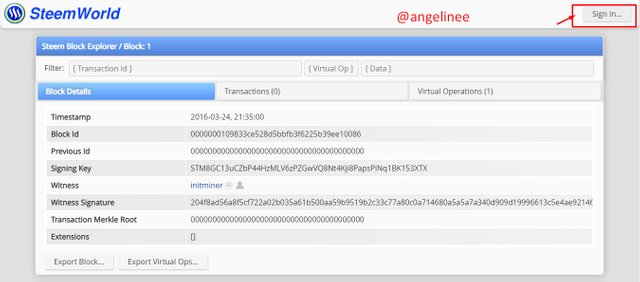
Here I will include my steemit account user name and private posting key for signing.
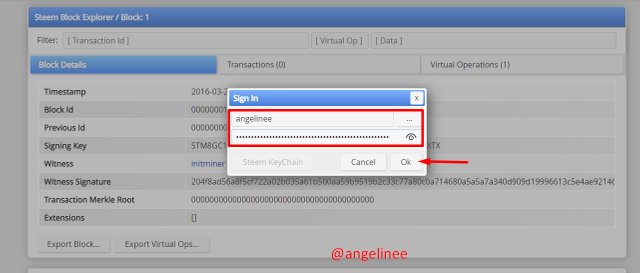
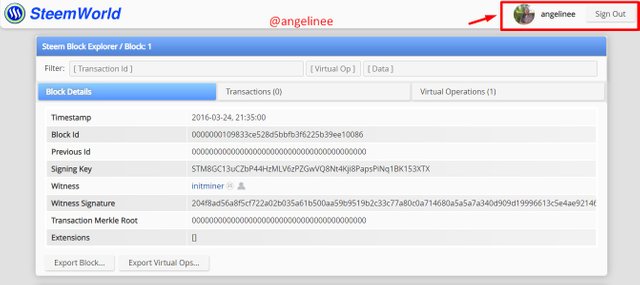
I have now successfully signed as proof of completion to this steemworld platform.

We can simply define these Cryptocurrencies are the most popular digital currency in the world. It has taken a huge amount of market capitulation among all the market money. The most important part is its security as compared to other digital currencies. Taking all these factors into account, in a few more decades only this cryptocurrency will be able to be used as a currency
.png)