Crypto Academy Season 3 Week 8: Homework Post for @stream4u: Let's Open The Blockchain; Cryptography
Introduction
Hey everyone, it's always an exciting experience doin homework for the Crypto Academy Professors especially for this season, Season 3, and this is our last week this season. We are learning from the respected professor @stream4u about the world of Cryptography. It's about security and how the Blockchain is kept safe and able to monitor different transactions. Kindly, let me dig deep into the homework.

Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms (Few names of the Blockchain Platforms)?
The term Cryptography originated from the words "kryptos" which means 'hidden' and "graphein" which means 'to write'. The two words used together can therefore point to hidden writing or personal information.
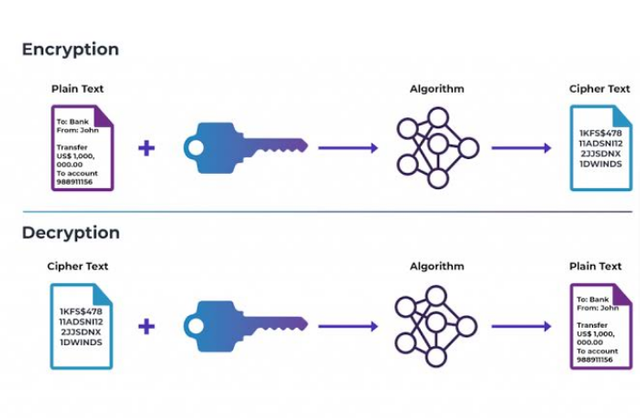
Cryptography is a technology on the blockchain that uses encryption which is the transforming of data into codes to prevent unauthorized access on the blockchain by sealing all transactions in the network. The developers of cryptocurrencies built strong cryptography through advanced mathematics and engineering computer principles, that is impossible to break meaning that they cannot be counterfeited or duplicated. If a transaction is executed, or if there is an engagement on the blockchain, there cannot be an override. It is used to prevent third parties from accessing the data/ messages. To read the message, one must decrypt it with a private key that is only accessed by the authorized receiver.
Blockchain Cryptography
A Blockchain is a distributed ledger of data and this data is secured using Cryptographic protocols that are almost impossible to break. All the nodes have a private key that allows them secure their data and if there is a breach or change in a block, the hash is altered making the digital signature invalid and the owner will get a red alert.
The Cryptographic protocols are designed in a way that for a hacker to break them, they would have to hold over 51% of computing power on the Blockchain which is hugely unlikely due to the nature of Decentralization of the Blockchain.
Blockchain Projects
Due to the expenses and time consuming efforts in creating a Blockchain, many crypto companies can now use the same Blockchain technology.
There are four types of Blockchain. Namely; Public, Private, Hybrid Blockchain and Consortium Blockchain. And as many tokens and coins crop up today, other Blockchain have been put in place, the first having been the Bitcoin Blockchain by Natoshi Nakamoto.
Blockchain Platforms
Some of the major platforms which are widely used on the blockchain include the following.
Ethereum
EOS
IBM Blockchain
Fantom
These and more platforms have been developed to overcome some limitations associated with central authorities in trading crypto.

Explain the Public Key CryptoGraphy.
Public key cryptography is a cryptographic code that has an address as a hashed version of the public key that is used to deposit funds. The public key is generated by the private key but the private key cannot be generated by the public key.The public key which is openly shared on the Blockchain network unlike the private key which is a secretive key. A digital signature can be verified using a public key that was created using the user's private key.
In trading transaction both receiver and sender exchange their public keys with each other in order to decrypt messages between each other. The sender creates a digital signature using his private key and transfers the public key to the receiver. The receiver goes ahead to use the sender's public key created by the digital signature of the sender using his private key.

Explain the Private Key CryptoGraphy.
The Private key is solely meant for the user alone and cannot be shared. It holds the keys to the wallet's sensitive data or secrets. All monetary transactions cannot be executed without this key and only the person who has these alpha numeric characters that form the private key can claim ownership of the wallet.
With the private key cryptography, when you're in the process of trying to access your funds, the private key is the only authorization needed to conceed to wallet access as it decrypts the protocol to allow access to funds. In P2P, the private key is used to create the digital signature that generates the public key to the receiving side.

Explain the Digital Signatures CryptoGraphy and what is Signing Of Transaction/Message?
As we all know, everybody needs to have a signature to verify their authorization on documents. If one doesn't have one, one usually uses their thumb to stamp on documents as an authorization. This signature acts as a binding concent. Similarly, digital signatures bind a user who sends their public key to another user as concent to the transaction. It is verified by the receiver using this public key.
A transaction is digitally signed through creating the hash value of the data as this makes it very secure and trustless meaning, there can be no worry for breach of agreement between the users.
It's Importance
Trustless Network
The digital signature makes it automatically acceptable to not need to trust anyone with whom you transact, as it's an assurance of commitment that cannot be breached. The message this is considered authentic.Large data signing
Using digital signatures can cater for all the large, and eliminate computatively expensive and time wasting signing by just using the hash value.Alterations override
It is not possible to modify the data since in case the data is tampered with, the hash value will change, and the reviving end cannot therefore verify it. There is no room for trickery.Binding
It's the private key of the sender that generates the digital signature that signs the documentation. Therefore, it's highly binding as there is clear indication on who signed. Therefore this creates transparency.
Singing Of Transaction
A digital signature can be created following these steps;
To begin with, a unique hash is created using a hash function by the sender after which he digitally signs the message by feeding the hash value and signature into the signature algorithm.
The digital signature is attached to the data and sent to the receiving user who also in this case is the one to verify it.
The receiver uses the public key to verify the signature by entering it into the verification algorithm and he receives data to generate a hash value which is compared with the output value received after verification. This comparison shows the validity of the signature.

Explain what is Symmetric and Asymmetric cryptography?
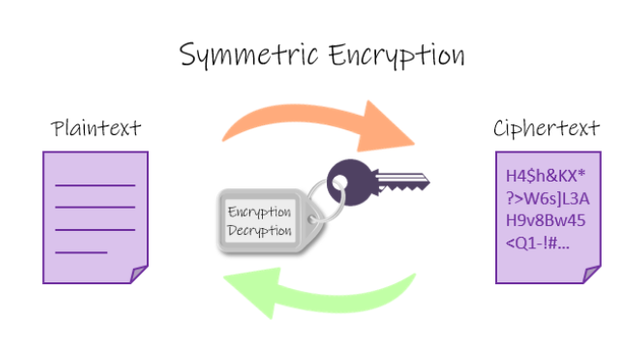
Symmetric Cryptography
Symmetric literally means 'the same, regardless of position or size', therefore this type of Cryptography is where a single key or the same key is used to encrypt and decrypt data. There is no regard for wether it's public or private, as long as the same key is used both to encrypt and decrypt the data.
Data is Encrypted that is to say, converted from plain text to cipher text using a secret key by the sender and this same key can be used by the receiver to decrypt the data. It is a trustless process where the secret key is known both by the sender and receiver.
It is interesting to note however, that the symmetric keys are usually 128 or 256 bits long, whereby a 128-bit long key has got 34x10^37 possible combinations. This is literally unhackable by all means possible!
Advantages
It does not require alot of computational resources or power as the algorithms produce small files and therefore have no need for alot of storage space.
It allows large data amounts to be easily encrypted or decrypted between two parties that have full trust in each other.
Disadvantage
Scalability becomes limited after a certain space as large groups need larger number of keys. This is usually captured as n(n-1)/2, and n stands for number of people.
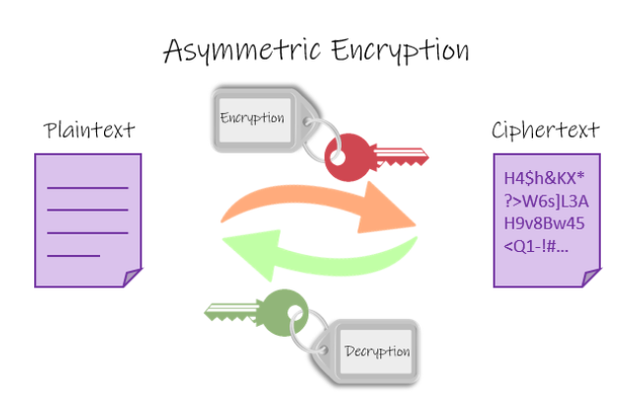
Asymmetric Cryptography
Asymmetric is the opposite of symmetric. It literally means 'different' as symmetric means 'same'. So in this case, this kind of Cryptography is where different keys are used i.e private key and public key although they are both interlinked to each other for instance the a user can use the public key of the receiver to encrypt a message which he sends to the receiver, the receiver has to use his private key to decrypt the message. Only he has the authority to use it and no one else. All messages encrypted with a public key can be decrypted by the private key that corresponds to it.
Advantage
Asymmetric Cryptography is helpful where there are large files to handle, as only a few keys are needed to encrypt or decrypt transactions. For a group of 50, only 50 keys are required.
Disadvantage
The obvoius disadvantage is that it is slower as it needs private key that is unique to one user.

How do Blockchain Wallets in Cryptography work? Explain the available types of Crypto Wallets.
Blockchain wallet cryptography
Crypto wallets are a kind of software that stores private and public keys and may be accessed only by their respective keys, Private/secret key's the one way to prove ownership of digital assets. The Public key of the crypto wallet is employed to receive the funds. Accounts are often identified on the blockchain using the general public key of the wallet whilst the private key of the wallet is merely to sign the transaction and to prove the ownership of the wallet.
Cryptocurrency doesn't get storage in any location and only the transactions it records exist on the blockchain. Unlike traditional ‘pocket’ wallets, the crypto wallet doesn't store any currency.
To add to the above, two blockchain/crypto wallet addresses can never have the same alphanumeric characters or to explain better, to be the same. It works the same way as the real world bank accounts that cannot have the same account number. Similarly crypto wallet address is required to transfer the funds.
When sending funds to an account in the bank, one must have the account number. When the receiver gets money, they must input their PIN as a password in order to withdraw it from the account. If anybody gets ahold of the PIN, the account can be hacked and compromised. All the funds will be lost to the user with the PIN. If you change it in time, when the hacker enters the PIN, the transaction will be refuted and a message sent to the account holder to show an attempt to breach security.
With wallet Cryptography, in case our our crypto wallets are often in danger if our private/secret key's stolen.
As seen from the example above, the two systems are similar but the difference is that with the bank account, the identity of the account owner is verified. In case funds are compromised, it is easier to track and recover them unlike in the case of a blockchain wallet where the identity of the owner isn't verified per se. It would be almost impossible to recover the stolen funds in this system of payment.
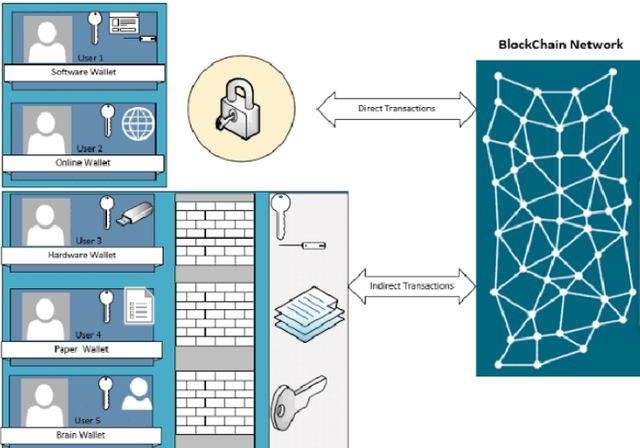
Types of crypto wallets
There are various sorts of crypto wallets that come under three main categories and these include the following;
Software wallets
These are a kind of mobile application that are comparatively smaller and faster than the desktop wallets that can be used anywhere. These can be further divided into;
Desktop wallets
These wallets are downloaded onto a personal computer and may be accessed only thereon particular device. Such wallets are good as they're secure. However their reliability depends on virus attack or the PC falling into the wrong hands.Online wallets
Online wallets are wallets that use the internet to be able to be accessed. They are cloud wallets and can be accessed anywhere. They store private keys online and but remember that anything that's on the cloud storage or internet is lable to be hacked.
Paper wallets
Here, funds are transferred on the paper wallet by moving the funds from the software wallet to the general public address printed on the paper wallet. During the process, funds from paper wallets to software wallets are often swapped by using keys printed on a paper wallet. It has the very best level of security as it is the print copy of all the keys on the paper. It are often done either manually entering keys or by QR code scanning.
Hardware wallets
These wallets store keys offline in hardware devices like USB but transactions are can only and only be performed online. Trezor can be an example of a hardware wallet. The advantage of hardware wallets is that they are often compatible with different web interfaces and may store various currencies. Transaction via hardware wallet is as easy as a web wallet but safer because it stores assets in offline mode, safe from any hacker. One only needs to connect the device to any internet-enabled computer or device in order to use this wallet. You enter a PIN and send currency.

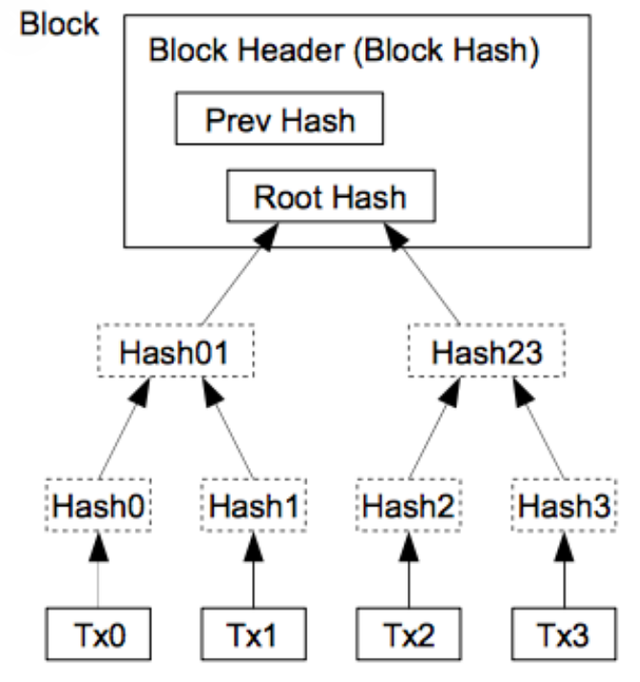
What is the Merkle trees and What it's importance in blockchain?
A Merkle tree may be defined as an arrangement that's utilized in computing applications such as in bitcoin and other cryptocurrencies, to encode blockchain data more efficiently and securely. They're also mentioned as "Binary Hash Trees."
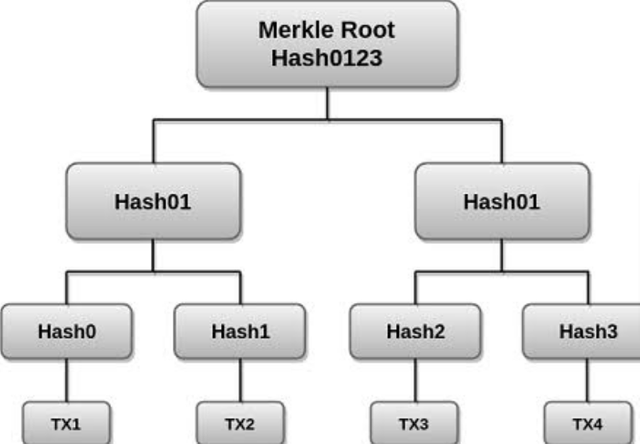
Source
It's a hash-based arrangement that's a generalization of the hash list with a tree structure during which each leaf node may be a hash of a block of knowledge, and every non-leaf node may be a hash of its products. Merkle trees literally have a branch factor of 2, meaning that each and every node has up to 2 products as seen below.
A hash tree or Merkle tree in Cryptography may be a tree in which every leaf node is labelled as having the cryptographic hash of a knowledge block.
Importance in blockchain
The Merkle tree is important in these ways;
• It is used as a summary of all transactions on a particular block on the Blockchain.
• The Merkle tree serves to allow secure and efficient verification of content in a large data body. It's in this way used to verify parts of the blocks thereby checking transactions using hashes from other branches of the Merkle Tree. In other words, Merkle tree is used to check the data integrity on Blockchain.
• Miners also use it to calculate hashes as they receive transactions from their peers. The work of miners on the Blockchain is of the utmost importance thus, the Merkle tree is important to this cause.
• Another important point to note is that the Merkle tree, encodes the blockchain data in an efficiently and securely. It quickly verifies blockchain data, as well as enabling fast movement of large amounts of data from one node to another on the peer-to-peer blockchain network.
• They significantly reduce the amount of memory needed to verify data as they need only small amounts of information to be reliably transfered across networks.

Practical + Theory, do some practical research and study on Blockchain Demo: Public / Private Keys & Signing. Explain the functionality of Key, Signature, Transaction, Blockchain.
Key
As we already discussed about the private key and public key, we saw that in a Symmetric Cryptography, one needs both of these keys. These are randomly generated codes generated got from numbers and alphabets. Every private key has a unique public key, and non can be the same.
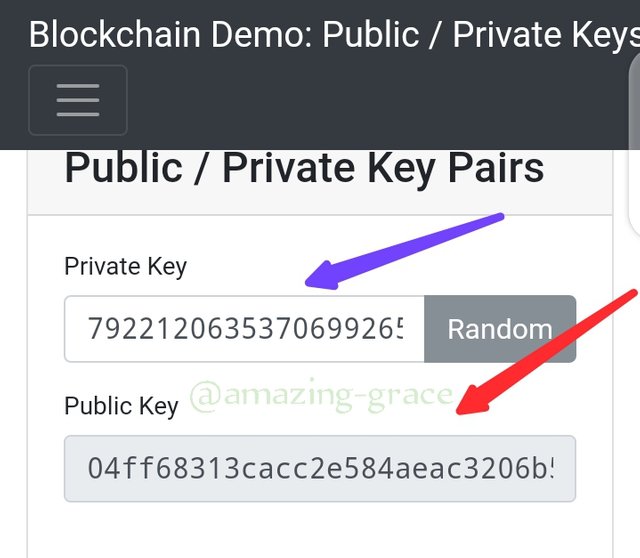
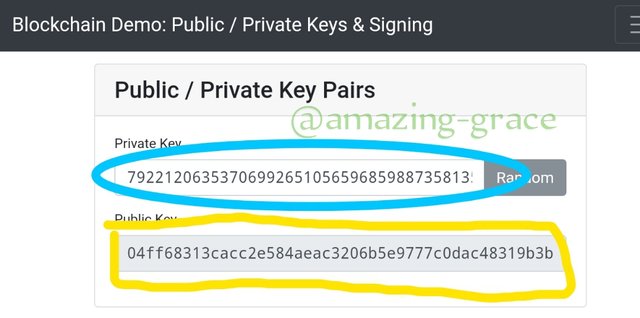
As sseen in the above image as illustration, the private key is;
7922120635370699265105659685988735813....
This key, generated a unique public key that's relative to only and the Public key is;
04ff68313cacc2e584aeac3206b5e9777c0dac48319b3b....
We can try to change the private key and see what happen. But I bet you that changing the private key automatically changes the public key. I will put 5 at the beginning instead of 5.
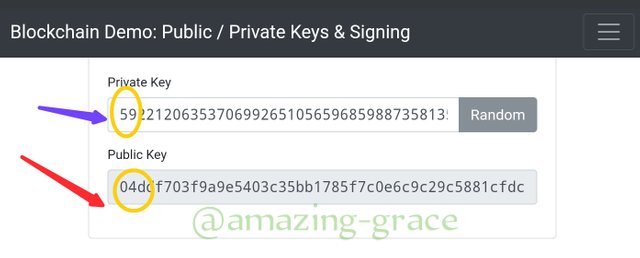
Private key :
5922120635370699265105659685988735813....
Public key
04dcf703f9a9e5403c35bb1785f7c0ec9c5881cfdc....
Changing the first digit from 7 to 5 completely changes the public key, yet I changed only one number. This means that that however small or big the change, the output must change. This verifies that each private key has a specific and unique public key. Now we can give the private key as one or three numbers to see if it changes the public key. I will use 100.
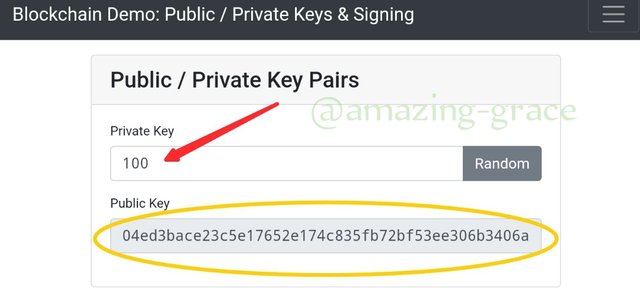
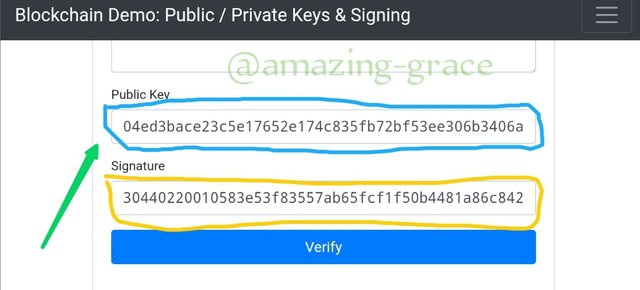
As seen above, the Private key is : 100
The public key is;
04ed3bace23c5e1765e174c835fb72bf53ee306b346a...
This last illustration also cements with clarity the fact that each private key has one unique public key generated.
Signature
Signatures show ownership and authenticity and it is generated with private key and hash of transaction. It is done to a transaction using a private key, which in turn is verified by miners before adding the block using owner's public key.
To sign, We go to website where we to select signature option from top right corner.
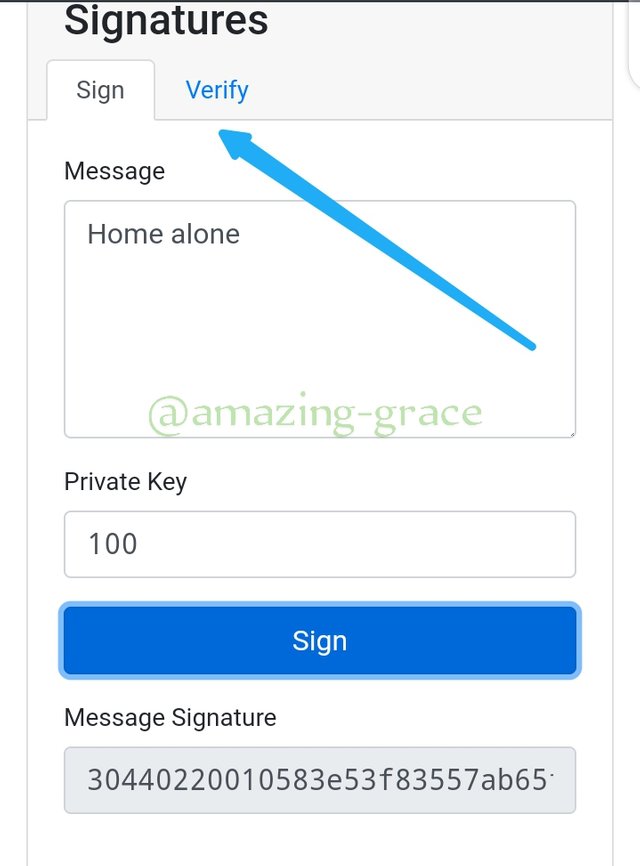
We provide a message in message box, and I will use Home alone.
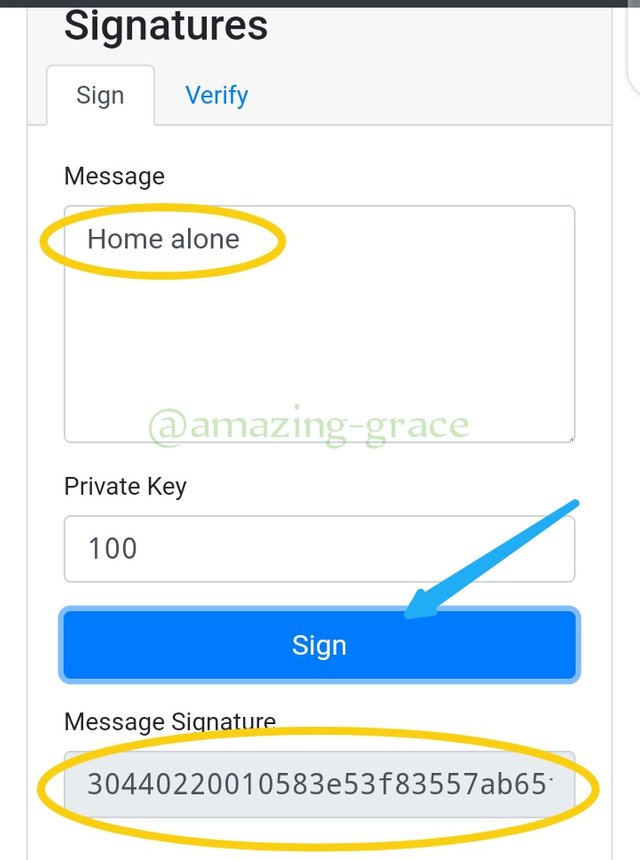
Next, enter a private key. I will use 100 still as the Private key. Click on sign button to digitaly sign on message.

As seen above, the signature for private key 100, message: Home alone, is 30440226010483e53f83557ab65fcfif50b4481986c842..
And now we go to Verification.
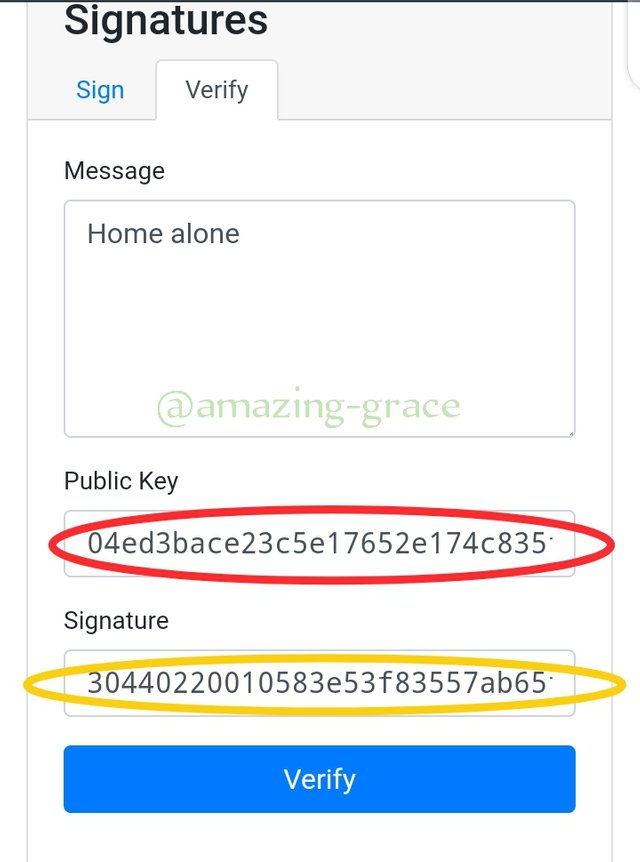
To verify this sign we click on verify option in same transaction tab and the verification is done right before adding a new block.
Remember the public key linked with the private key that is already shared with miner is 04ed3bace23c5e1765e174c835fb72bf53ee306b346a...
So we just head to the Verify option which will automatically turn into green if the transaction is successfully verified, but since I am using my phone now it can't change to green.
Transaction
Transactions are added to a block after Signing the message with private key and Verifying it with our public key. Therefore I am going to show how $ 20 is realized. So as to get the message signature.
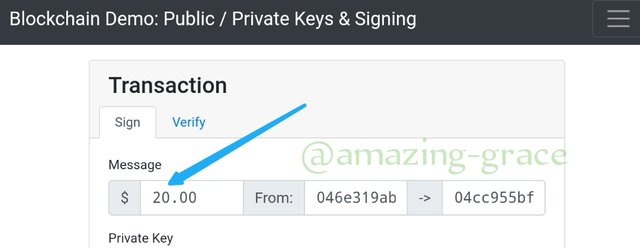
As seen above, the From address is beginning with 046e319ab...and because my phone screen is small, I may not show the rest of the other numbers. The To address begins with 04cc955bf..
Next click Sign button,
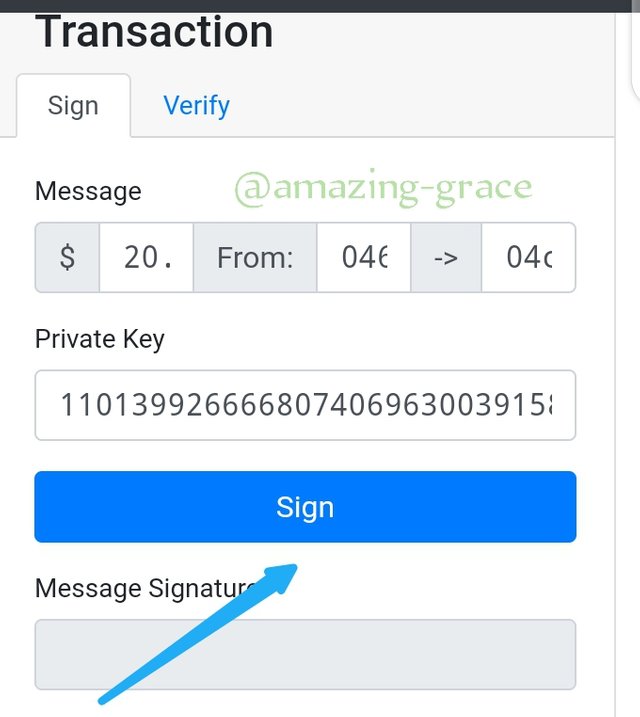
The message signature is;
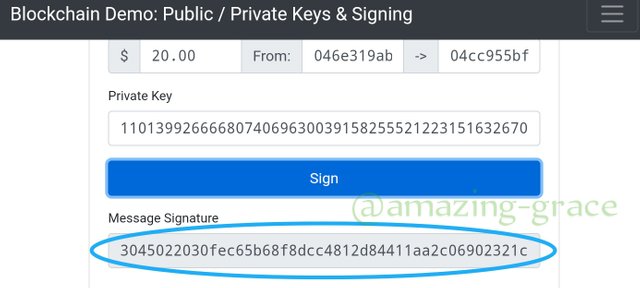
Sign; 304503330fec65b68f8dcc4812d84411aa2c06902321c...
After this step, we need to verify this transaction, so we go to the verify option.
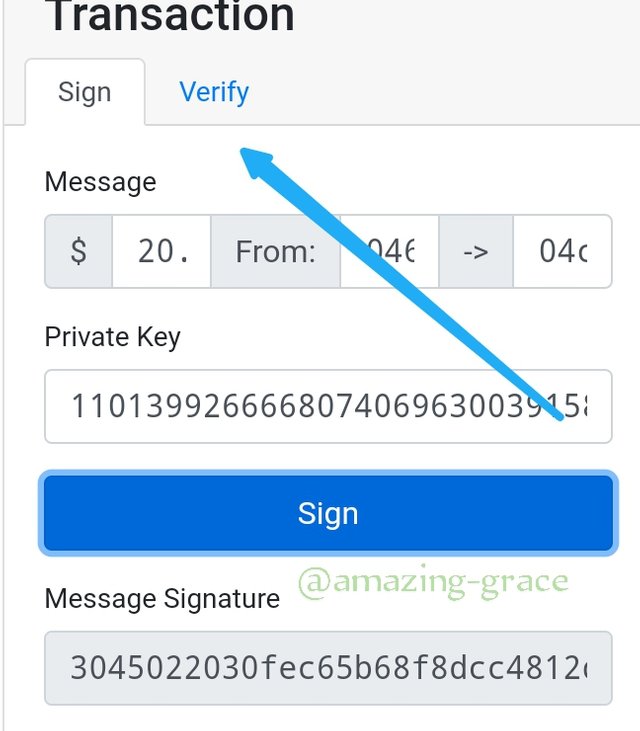
Click Verify.
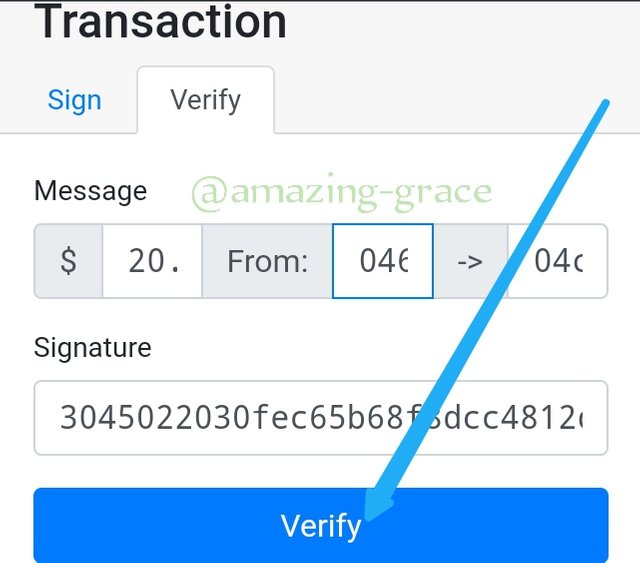
Here, we see that the block turns to a green colour showing that the block has been verified successfully.
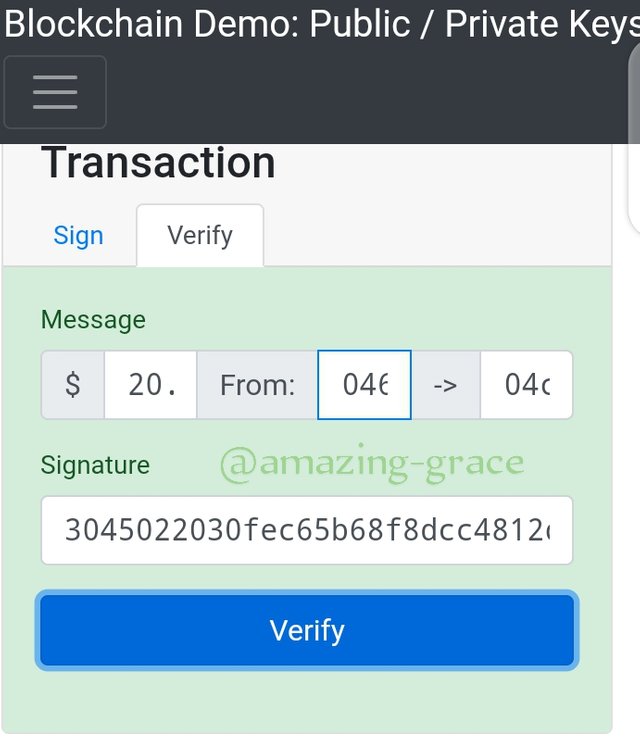
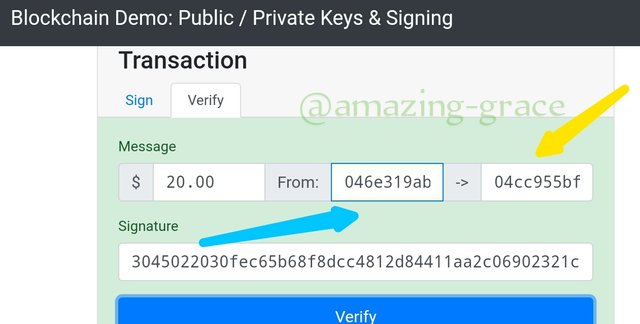
Blockchain
We head to the Blockchain section on the same site. It's the last option below. It shows us how transactions are stored in blocks wth hash created with Cryptography. So Click on block to see blocks
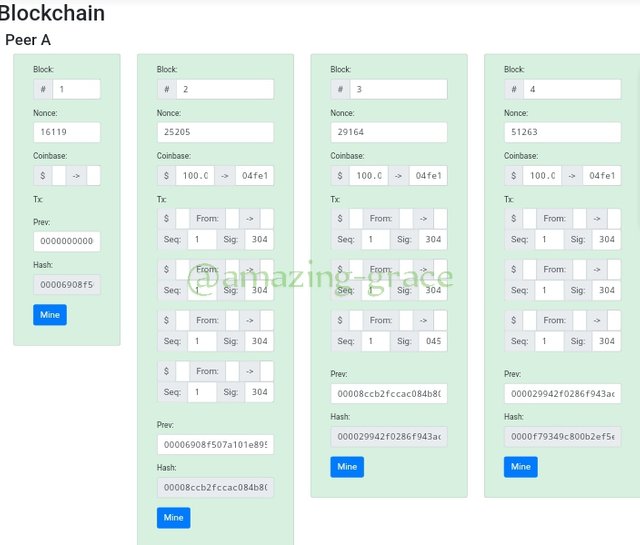
We are able to see all the verified blocks added here. Every block has the hash, block, nonce, and more other details. Changing any of the block details will cause the block not be verified.
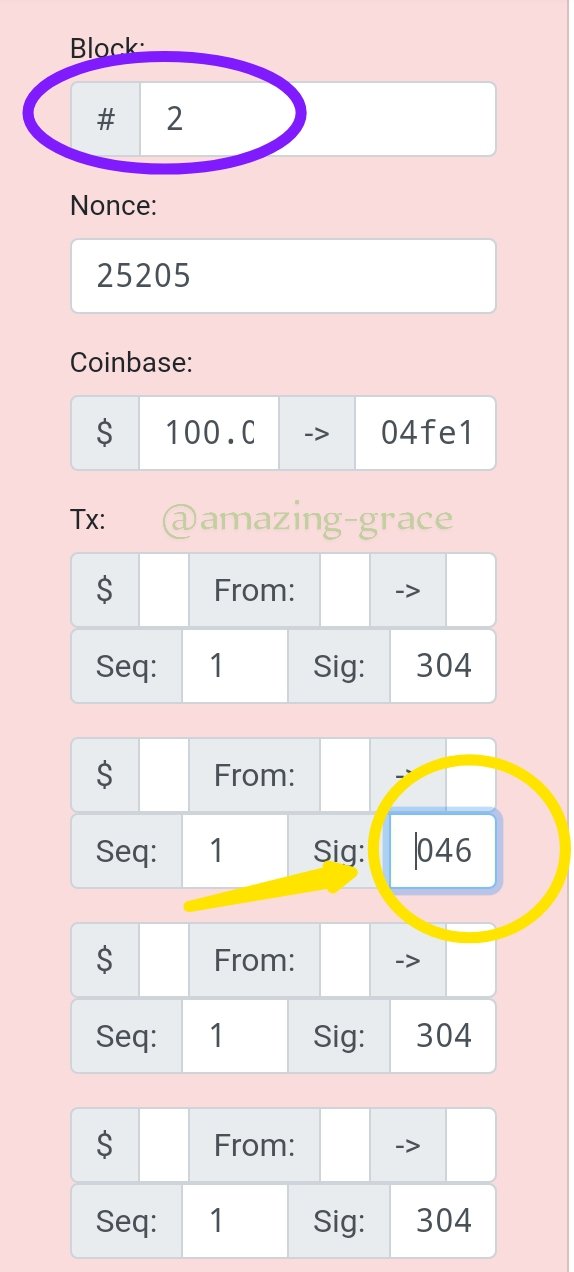
I changed the Tx second line on the block from 304 to 046 and the block changed color to pink. Showing its not verified.
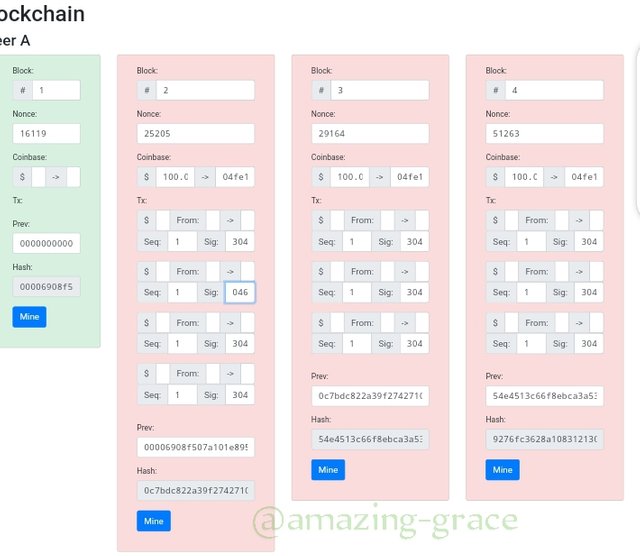
As seen above, block two , three and consequentIy all blocks filling herewith change to colour showing invalidity. To make them valid again, we have to mine the block, so Click mine.
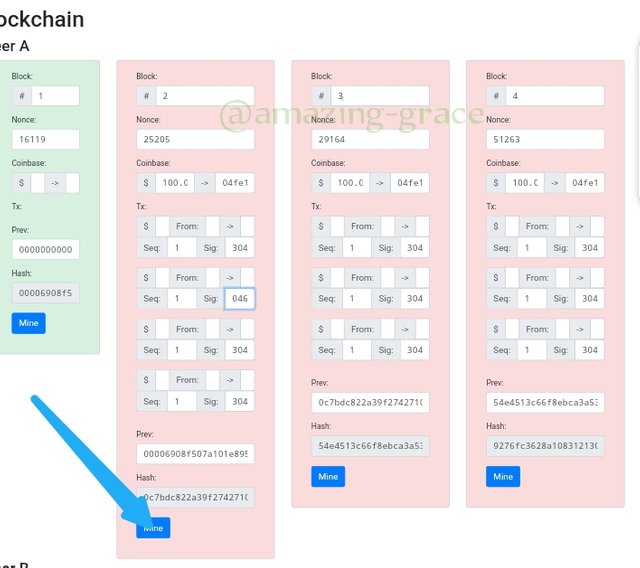
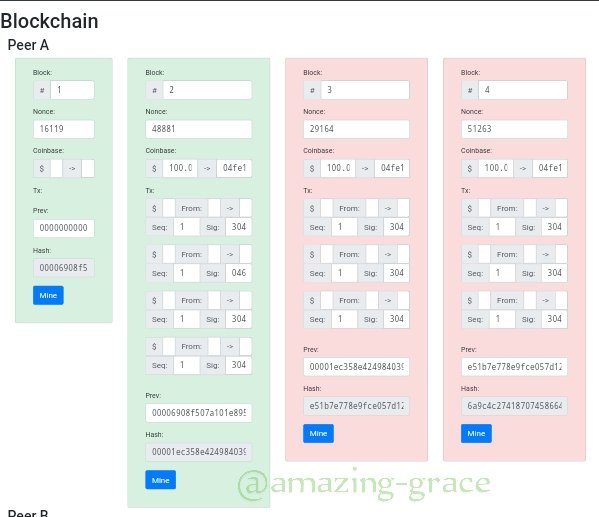
Now, block 2 has been mined. Do the same for others.

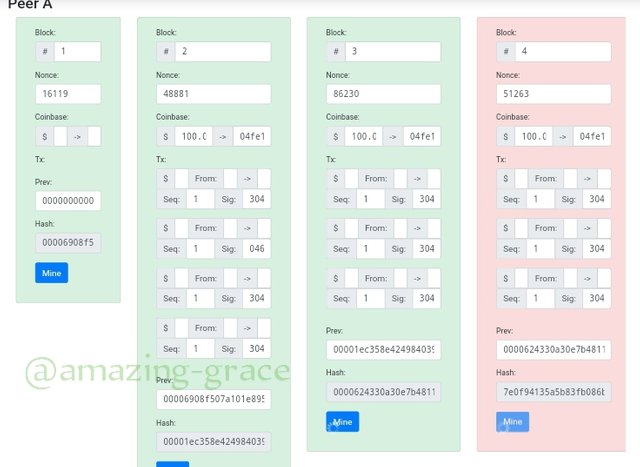
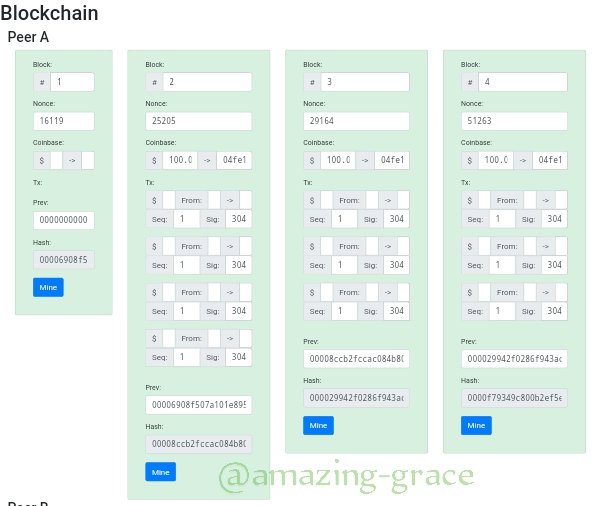
We clearly see that;
• The invalid blocks had different nonce with the validated blocks.
• Every block has got the hash of the previous block in it.
• Every invalid block makes the proceeding blocks invalid.
Conclusion
To conclude the above lesson, it's important to know the uses of both public and private keys and how the two are related in cryptography.
Without Cryptography perhaps, the Blockchain would be compromised and the hope for a decentralized Exchange system would be lost. It is the core protector of the crypto world and these computerized codes are the next best thing to Blockchain discovery.
The Merkle tree is equally vital in making transactions easier and faster, thanks to Mr Merkle after whom it was named because he discovered it's mechanism and today, it's use cannot be undermined.
I submit my homework post, thank you.