Hal Martin's OPSEC audited using public DBs

In a story published in POLITICO last month, Kim Zetter reported that the NSA caught Harold Martin III after he sent cryptic Twitter DMs to Kaspersky researchers who forwarded the information along to the NSA.
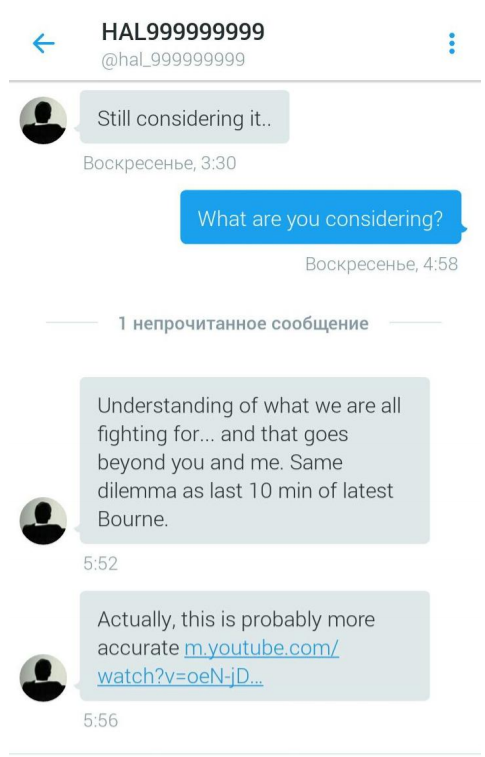
The case unfolded after someone who U.S. prosecutors believe was Martin used an anonymous Twitter account with the name “HAL999999999” to send five cryptic, private messages to two researchers at the Moscow-based security firm. The messages, which POLITICO has obtained, are brief, and the communication ended altogether as abruptly as it began. After each researcher responded to the confusing messages, HAL999999999 blocked their Twitter accounts, preventing them from sending further communication, according to sources.
... the [Twitter] profile picture showed a silhouette illustration of a man sitting in a chair, his back to the viewer, and a CD-ROM with the word TAO2 on it, using the acronym of the NSA's Tailored Access Operations. [emphasis added]
...
The timing was remarkable — the two messages arrived just 30 minutes before an anonymous group known as Shadow Brokers began dumping classified NSA tools online and announced an auction to sell more of the agency’s stolen code for the price of $1 million Bitcoin.
In response to the POLITICO article, Emptywheel wrote a post expressing skepticism that Hal Martin would send nonsensical DMs to Kaspersky for no good reason. Emptywheel suggests that the movie references (to Inception and the latest Bourne movie) made in some of the DMs are reminiscent of @TheShadowBrokers and proposes that Martin's Twitter account may have been hacked.
But, especially given the allusions to the two movies, I wonder whether these DMs actually came from Martin at all. There’s good reason to wonder whether they actually come from Shadow Brokers directly.
Certainly, that’d be technically doable, even though court filings suggest Martin had far better operational security than your average target. It would take another 16 months before Twitter offered Authenticator 2 factor authorization.
Additionally, Emptywheel and Zetter bring up that Martin had sexual proclivities which may be relevant to the story:
As Zetter also lays out, Martin had a BDSM profile that might have elicited attention from hostile entities looking for such chum.
A Google search on the Twitter handle found someone using the same Hal999999999 username on a personal ad seeking female sex partners. The anonymous ad, on a site for people interested in bondage and sado-masochism, included a real picture of Martin and identified him as a 6-foot-4-inch 50-year-old male living in Annapolis, Md. A different search led them to a LinkedIn profile for Hal Martin, described as a researcher in Annapolis Junction and “technical advisor and investigator on offensive cyber issues.” The LinkedIn profile didn’t mention the NSA, but said Martin worked as a consultant or contractor “for various cyber related initiatives” across the Defense Department and intelligence community.
I sought to investigate whether it is plausible that Martin's Twitter account was pwned. I was able to find 2 of Martin's e-mail addresses and by checking publicly available leaked databases (DBs), was able to determine that Martin re-used the same password for LinkedIn, MySpace, and Adobe (on two separate accounts). Therefore, it is reasonable to believe that Martin reused the same password for unimportant accounts such as his Twitter. I was also able to corroborate Zetter's finding that Martin had an account registered at Adult Friend Finder.
Martin's primary e-mail address is something like [email protected] [e-mail address altered to preserve whatever is left of Martin's privacy]. An e-mail address: [email protected], appears in a dump of ~5M Gmail passwords that appeared in a Russian hacking forum in 2014. (You can verify by entering into HIBP). The password associated with [email protected] is the same as the password used by Martin. (The DB is BitcoinSecurity1.txt MD5: 1c8917336e21dd998a03df0fb687d4d3). Google reported that less than 2% of the user:pass combos would have been able to access Gmail accounts, and I believe the password did not meet Google's PW requirements in recent memory.
Interestingly, the [email protected] e-mail address also appears in the Fling.com DB leak(fling.com_40M_users.sql MD5: 23160960ebf7efe64262383ddcea4a84). The last IP address used to log in to the account resolves to near where Martin lives and the birth date looks correct. The registration date is from 2010. However, the username is Teamtao99958 and the password is completely different from those previously used by Martin. It is 'lunch71' followed by 3 more digits. Surprisingly, the rather unique-looking password appears 30 times in the Fling DB on seemingly unrelated accounts.
There were ~10,000 passwords in the Fling DB that began with 'lunch71' followed by 3 digits and many more beginning with 'lunch' followed by 5 digits. Interestingly, I found several 'lunch71###' passwords in the BitcoinSecurity1.txt dump. Most of them were also exclusively in the Fling DB. One appeared in the possibly fabricated Badoo leak. It seems possible that BitcoinSecurity1.txt was partially sourced from the Fling/Badoo DBs. It is worth noting that the Fling and Badoo DBs originated from actors Tessa88 and Peace_of_Mind, who InfoArmor has linked to Yevgeniy Nikulin [Proxy 1/Group E] -- a hacker who reportedly is "of great interest in a U.S. probe of election meddling".
I was able to find no solid explanation for the 'lunch#####' passwords but would be interested to read other people's explanations.
Fling has confirmed the authenticity of the DB and Troy Hunt reported that it looks legit.
As Motherboard reported a few weeks ago, SS7 vulnerabilities are being exploited to bypass SMS 2FA, even by criminal hackers.
To conclude, if Martin reused his Adobe/LinkedIn/MySpace password on Twitter then it is plausible that an attacker could have accessed his account, even if he used Twitter's SMS 2FA. Additionally, his easily discoverable sexual interests may have made him a target, the [email protected] account may have drawn attention as well (if it actually belonged to Martin) and the 'lunch#####' accounts are weird.
To save time, I'll just copy and paste Emptywheel's disclaimer that this could all be absolutely nothing:
Mind you, there’s nothing in the public record — not Martin’s letter asking for fully rendered versions of his social media so he could prove the context, and not Richard Bennett’s opinion ruling the warrants based off Kaspersky’s tip were reasonable, even if the premise behind them proved wrong — that suggests Martin is contesting that he sent those DMs. That said, virtually the entire case is sealed, so we wouldn’t know (and the government really wouldn’t want us to know if it were the case).
Comments, questions, corrections? Leave a comment or DM here or on Twitter.
Congratulations @wh1sks! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
Click here to view your Board
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!
Do not miss the last post from @steemitboard:
Hello @wh1sks! This is a friendly reminder that you have 3000 Partiko Points unclaimed in your Partiko account!
Partiko is a fast and beautiful mobile app for Steem, and it’s the most popular Steem mobile app out there! Download Partiko using the link below and login using SteemConnect to claim your 3000 Partiko points! You can easily convert them into Steem token!
https://partiko.app/referral/partiko
Congratulations @wh1sks! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Do not miss the last post from @steemitboard:
Vote for @Steemitboard as a witness to get one more award and increased upvotes!