A little introduction to Network Packets 3(ARP)
MAC-Address:
What is a MAC-Address? The MAC-Address is a hardware-address that is unique to every network interface card (NIC) and consists of 6 bytes that look like this:
A1:23:BB:32:F8:01
The manufacturers of NIC assign the MAC-Address to their cards which is stored in its firmware. The first three bytes of a Mac-Address are manufacturer specific. It acts as unique identifier in a network for each network node(for example your computer).
ARP:
The Address Resolution Protocol(ARP) is a networking protocol which is used to discover MAC-Addresses and their assigned IP-Address in your Local Area Network(LAN). It consists of an ARP-Request and an ARP-Response as you can see below. In the OSI-Model it is a layer two protocol. If you don't know the OSI-Model yet, you can look it up here:
https://de.wikipedia.org/wiki/OSI-Modell#Die_sieben_Schichten
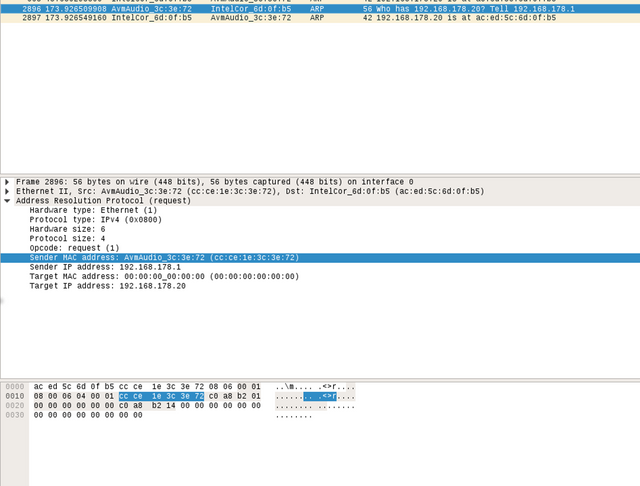
Above you can see a so called ARP-Request in which your computer asks „who has this IP-Address?“. It does that via a packet it sends out. The Packet consists of several fields off of which the highlighted field is the senders Mac-Address for example. Two fields below that you can see the field Target Mac which is filled with Nullbytes which means this packet is a request for the Mac-Address of the IP-Address 192.168.178.20.
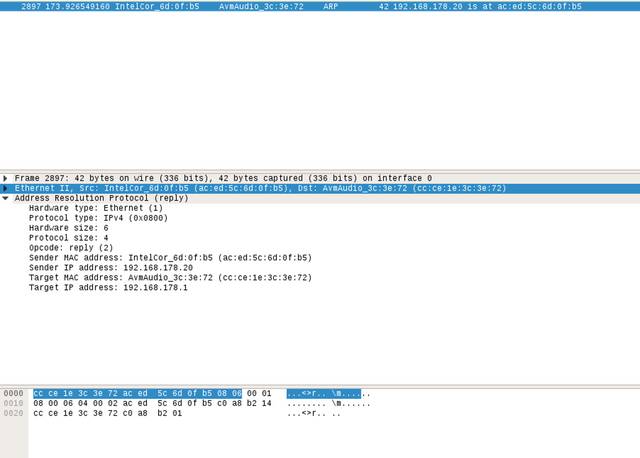
Here you can see the reply for the request from above. Essentially the device with the IP-Address 192.168.178.20 tells that it has the MAC-Address ac:ed:5c:6d:0f:b5.
The answer is then stored in the ARP-Cache of your computer which acts a little like a phonebook so to speak.
Thats the point where it gets interesting. There are in general no checks when the reply comes in if there was even a request. So what happens when you send an Arp-Response with the wrong Mac-Address to your target? We‘ll cover that in the next part where its less theory and more hands-on.
How to look at the ARP-Table in your computer:
In Windows you can open the cmd or powershell and type:
arp -a
In Linux you can view the cached ARP-Responses via your terminal if you type:
sudo cat /proc/net/arp
or
sudo ip neighbour
So that's it for today. Next time we'll be looking at how we can manipulate the "routing" so we can capture packets that are not intended for us.
Have a nice weekend!