@Very few people know about hacking. Ethical hacking is the best technology ....?
🔥A security hacker is someone who seeks to breach defenses and exploits the weaknesses in a computer system or network. Hackers may be motivated by a multitude of reasons, such as profit, protest, information gathering, [1] challenge, recreation, [2] or to evaluate system weaknesses to assist in formulating defenses against potential hackers The subculture that has evolved around hackers is often referred to as the underground computer. [3]
There is a longstanding controversy about the term's true meaning. In this controversy, the term hacker is reclaimed by computer programmers who argue that computers are broken into computers, whether computers or computers are broken into a advanced understanding of computers and computer networks, [4] and that cracker is the more appropriate term criminal (black hats) or computer security expert (white hats). [5] [6] A 2014 article concludes that "... the black-hat meaning still prevails among the general public". [7] [tone].jpeg)
The most notable hacker-oriented print publications are Phrack, Hakin9 and 2600: The Hacker Quarterly. While the information contained in magazines and ezines was often outdated by the time they were published, they increased their contributors' reputations by documenting their successes. [43]
1.points: - Hackers in fiction
See also: List of fictional hackers
Hackers often show an interest in fictional cyberpunk and cyberculture literature and movies. The adoption of fictional pseudonyms, [45] symbols, values and metaphors from these works is very common. [46]
✒Books ....
The cyberpunk novels of William Gibson-especially the Sprawl trilogy-are very popular with hackers. [47]
Helba from the .hack manga and anime series
Merlin of Amber, The protagonist of the second series in The Chronicles of Amber by Roger Zelazny, is a young immortal hacker-mage prince who has the ability to traverse shadow dimensions.
Lisbeth Salander in The Girl with the Dragon Tattoo by Stieg Larsson
Alice from Heaven's Memo Pad
Ender's Game by Orson Scott Card
Evil Genius by Catherine Jinks
Hackers (anthology) by Jack Dann and Gardner Dozois
Little Brother by Cory Doctorow
Neuromancer by William Gibson
Snow Crash By Neal Stephenson.
✒Films .......
➿Antitrust
✴Blackhat
✴Cypher
✴Eagle Eye
✴Enemy of the State
✴Firewall
✴Girl With The Dragon Tattoo
Hackers
✴Live Free or Die Hard
✴The Matrix series
The Net
✴The Net 2.0
✴Pirates of Silicon Valley
✴Skyfall
✴Sneakers
✴Swordfish
✴Take Down
✴Tron
✴Tron: Legacy
✴Untraceable
✴WarGames
✴Weird Science
✴The Fifth Estate
✴Who Am I - No System Is ✴Safe (film)
Non-fiction books
✴The Art of Deception by ✴Kevin Mitnick
✴The Art of Intrusion by Kevin Mitnick
✴The Cuckoo's Egg by Clifford Stoll
✴Ghost in the Wires: My Adventures as the World's Most Wanted Hacker by Kevin Mitnick
The Hacker Crackdown by ✴Bruce Sterling
✴The Hacker's Handbook by ✴Hugo Cornwall (Peter Sommer)
✴Hacking: The Art of Exploitation Second Edition by Jon Erickson
Out of the Inner Circle by Bill ✴Landreth and Howard Rheingold
✴Underground by Suelette Dreyfus.✔
#bruce sterling, author of the crackdown.?
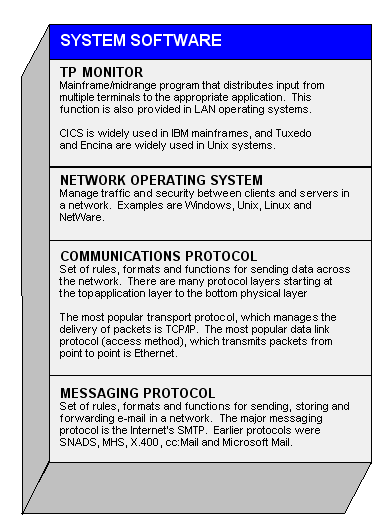
In information technology, an application is a technology, system, or product.
The term application is a short form of application program. An @ (application program) is a program designed to perform a specific function directly for the user or, in some cases, for another application (program). Examples of applications include word processors, database programs, web browsers, development tools, drawing, paint, image editing programs, and communication programs. Applications use the services of the computer's @ (operating system) and other supporting applications. The formal request and means of communicating with other programs is called an application program interface (API).
.png)
Continue Reading About application.
✒SearchCRM.com has information about the customer relationship management applications.
✒SearchVB.com, a portal for Visual Basic developers, includes a collection of links about applications.
✒SearchWin2000.com has a collection of internet links related to applications.
✒Search400.com has hundreds of links related to AS / 400 applications.
the most important speech Gyzz.???
Hello armaan0786
You are welcomed by the service of FreeResteem.
We want to bring more people to your post.
If you like our service then put a upvote under this comment.
Thank you for remain with Steemit.