SECURITY alert: GRCpool users -> change your passwords -> attack to bruteforce pwds
Find updates on the situation here:
- "attack has slowed down but is still active"
---
From Facebook:
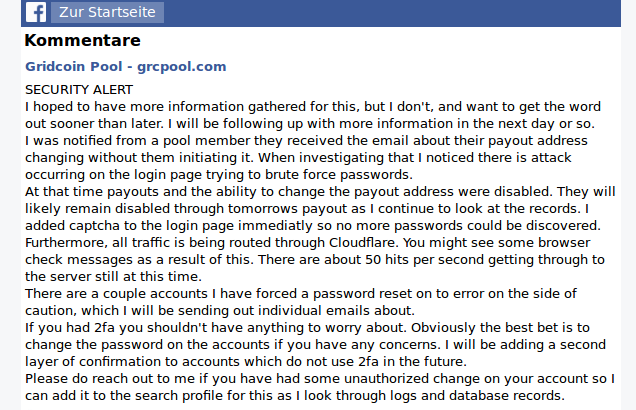
"SECURITY ALERT
I hoped to have more information gathered for this, but I don't, and want to get the word out sooner than later. I will be following up with more information in the next day or so. I was notified from a pool member they received the email about their payout address changing without them initiating it.
When investigating that I noticed there is attack occurring on the login page trying to brute force passwords.
At that time payouts and the ability to change the payout address were disabled. They will likely remain disabled through tomorrows payout as I continue to look at the records.
I added captcha to the login page immediatly so no more passwords could be discovered. Furthermore, all traffic is being routed through Cloudflare. You might see some browser check messages as a result of this.
There are about 50 hits per second getting through to the server still at this time. There are a couple accounts I have forced a password reset on to error on the side of caution, which I will be sending out individual emails about.
If you had 2fa you shouldn't have anything to worry about. Obviously the best bet is to change the password on the accounts if you have any concerns. I will be adding a second layer of confirmation to accounts which do not use 2fa in the future.
Please do reach out to me if you have had some unauthorized change on your account so I can add it to the search profile for this as I look through logs and database records."
Read updates here, or check out @bgb and above Facebook and twitter
find updates on the situation here:
Thank you for the heads-up.