OMG…I’ve been Hacked
A few days ago I got hacked for the first time ever. I have a cryptocurrency account on the Exrates.me exchange which got hacked. The thieves stole all my crypto from that account. As some of you may know I’ve been an advocate for the Equaliser project. Currently Equaliser coin (EQL) is trading on the Exrates exchange. This is a great project and I wanted to make sure that I was a part of this amazing project, buy supporting the community and the Equaliser coin.

It’s a terrible feeling logging on and seeing something wrong. There was an immediate feeling like something inside had dropped down to the bottom of my stomach as a feeling of dread shot through my body. It’s a bit like that split second before you almost have an accident like falling off a bike or just before a car crash. That feeling of knowing…but it’s all too late to do anything about.
I’ve heard and read stories of people being hacked before and the infamous Mt Gox ‘hack’ a few years ago in 2014 that saw around 850,000 bitcoins belonging to customers and the company go missing.
The hackers stole $670 USD worth of cryptocurrency from my account. That may not sound that much to some, but for a father of 4 kids in a family with a mortgage in Sydney that was all the funds I could spare.
What the thieves stole
I had bought around 410,000 of the Equaliser cryptocurrency coin EQL. I also had further EQL buy orders to buy with BTC and ETH. I wanted to make sure I bought 500,000 EQL before I withdrew it all. So the thieves stole close to 0.1 Bitcoin (BTC) from me, about $670 USD (at time of writing). Initially it wasn’t just the crypto they stole from me but my dreams of being a major part of the Equaliser community with a big stake in it. Luckily I had previously bought and withdrawn some amount of EQL to my Agama wallet a month or two prior which is still safe, thankfully.
Leaving such a large amount of crypto on the Exrates exchange was one of my main mistakes. There was no reason why I should have left that much coin on the exchange, but rather should have been withdrawing the EQL as soon as I purchased it.
I had seen accounts from other people and tweets claiming that Exrates stole their crypto and warning others not to use that exchange. Checkout the @Exrates_Me twitter site and look at the list of peoples’ problems with Exrates. My initial reaction to these ‘stories’ were to scoff and I just thought that they probably did a few bad trades and just want to blame someone for it. But in hindsight alarm bells should have been going off in my head. These accounts of other investors claiming Exrates stole their coins shows at best a poor track record in maintaining a secure website, and at worst given the continued hacks and funny business going on, may show a darker shadier side to those at Exrates. I’ll let you draw your own conclusions from that.
I didn’t withdraw earlier because I’ve never been hacked before and thought it could never happen to me.
There’s 2 parts to the Hack:
- Getting in to the Exrates Exchange site
- Withdrawing cryptocurrency out of the exchange.
The first part is the hardest, how to get authenticated and into the Exrates exchange site. The way I believe this was done, and most likely will happen again unless Exrates does something to fix it is by way of Cross Site Scripting (XSS). XSS is in the top 10 hacking methods as defined by OWASP.
For those of you that don’t know, OWASP (Open Web Application Security Project) is an organization that provides unbiased and practical, cost-effective information about computer and Internet applications. The OWASP information is used by companies around the world to help strengthen their systems against attacks and hacking.
I’ve worked as a software developer for around the last 30 years in Australia. I currently work for an Australian Approved Deposit-taking Institution (ADI) and each year all staff are trained in the OWASP top 10 attacks. Cross site scripting (XSS) has been in the OWASP top 10 for the last decade or more, meaning it’s one of the most common attacks, and one of the attacks that most companies are trained against. Australian ADIs and banks are regulated and are required to make sure all staff are trained in the OWASP top 10 each year. The problem is using untrusted, foreign exchanges and institutions that are not regulated and are not compelled to follow any sort of stringent security measures. Most countries around the world regulate their banks to implement modern internet security methods. However, cryptocurrency exchanges to my knowledge have no such pressure to implement the same sort of security and security testing. I think the smaller crypto exchanges in general are rushed to market and requirements like adequate security testing and PEN testing (Penetration testing) are the first things cut out to meet deadlines.

XSS to gain access and impersonate me
I believe XSS was used to gain access to my account.
XSS allows attackers to execute scripts in the victim’s browser which can hijack user sessions, deface web sites, or redirect the user to malicious sites.
https://www.owasp.org/index.php/Top_10-2017_A7-Cross-Site_Scripting_%28XSS%29

Session Hijack
Every time you access an internet site you get a ‘session’ which has certain security information in it that authenticates you on that internet site. I believe that my session was hijacked and the attacker then was able to impersonate me and get authenticated into my Exrates account. From there they switched off 2FA (2 factor authentication). The Exrates website wasn’t checking that the session token came from my browser or the attackers. All it’s checking for is if it has a valid session token, which it does because the attacker was able to copy mine and start using it and impersonating me. Good programming practice is to expire session tokens regularly.
The Hackers dumped and sold all my Equaliser coin (EQL) for Bitcoin (BTC). They immediately sold all the Bitcoin for USD. They then bought Ethereum (ETH) with that USD and then withdrew that ETH to their own wallet.
The hackers wallet address they withdrew to is:
0xe540624d9D813e86e5028DDc77c77dFE4CfCb565
I can see the transaction and can also see that the thieves moved the Eth afterwards.
Part of XSS is to get the victim to unsuspectedly click onto a link that has malicious software on it that will return back to the attackers address the session information for the currently active session. That way the attacker can then pass that same session credentials (copy and paste) into a request to the Exrates website. The Exrates website if it hasn’t been software developed properly wouldn’t be checking for this type of attack and so just accepts the request and does whatever the attacker wants to do.
I suspect that it all happened when I logged on. I remember an irregularity when logging on to the Exrates site whereby it showed the ‘Click to Verify’ link twice on the same window as shown below. I suspect one of them was the real link, and the other was a malicious link that was constructed to look like the real thing (like a trojan horse). I didn’t think anything of it at the time and just clicked on it as well.
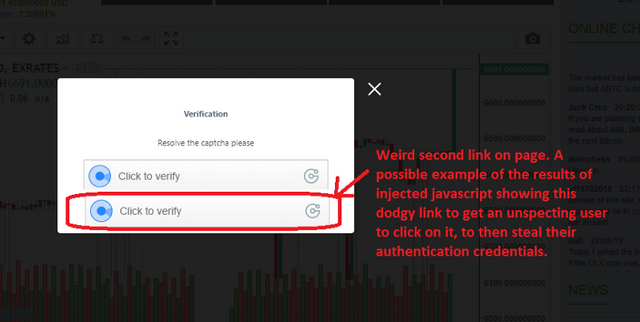
If there are “holes” and vulnerabilities in the software, an attacker will often inject javascript into a site that ‘adds’ their malicious link in the form of something that will make the user click on it without knowing that it’s going to send the victims authentication details to the attacker who can then exploit the lax security of the site and impersonate the victim. Poorly written websites often don’t ‘sanitize’ the data that users type in to fields. This allows a hacker to inject (type in malicious code) javascript into the fields that a regular user would type in to. By doing this the attacker adds extra behaviours to the window so when it renders to a valid user, it has the behaviours in it that will exploit the users session and send it to the attacker to then hijack.
According to OWASP:
Typical XSS attacks include session stealing, account takeover, MFA bypass, DOM node replacement or defacement (such as trojan login panels), attacks against the user’s browser such as malicious software downloads, key logging, and other client-side attacks.

What now?
I realised that how I reacted to this event was entirely up to me. I could be angry, upset and give up on it all. This didn’t feel right to me. I don’t want to be at the end of cause and effect. I’d rather not perpetuate the crime of the ego which loves violence, anger and negativity. I don’t want this event to determine how I live my life and how I move forward. Yes, the pain is there and the disappointment but I’d rather just recognise it for what it is and move on. I’d like to be at the same positive level I was before this happened but realise I can’t do that if I’m carrying this baggage with me.
I’m still a very positive about the Equaliser project in providing affordable, strong, energy efficient homes for those that traditionally haven’t been able to afford one. The Equaliser project will move on and find other exchanges that are interested in providing good service and have taken the time and effort to properly develop their website and continue to take an interest in maintaining a secure cryptocurrency exchange. Exrates from what I’ve noticed has a history of hacks and rumours I’ve heard of possible ‘shady’ practices. I have no confidence in Exrates and would recommend that anyone with funds there to minimise their risk and withdraw coins they aren’t actively trading ASAP.
For further information about Equaliser, click on the links below.
With love and peace,
Paul Clarke
Medium: JellySmash
Twitter: @greenbergblue
Links
For more information on Equaliser click:
https://equaliser.org/
Join us on Discord for fun and chat about Equaliser:
https://discord.gg/GFAnKGz
Short video on Equaliser:
The Equaliser Whitepaper:
https://equaliser.org/Equaliser_Whitepaper_Version_1.pdf
Donations are always appreciated, you can deposit to either of my below addresses -
Bitcoin (BTC): 35fjF5ZtPfB8crHogJBxDmsF9cMknqVHmM
Ethereum (ETH): 0x2f14f76A8BBa608c7d0C4fe27b66d3E54075Bc26
KMD/EQL: RSe7H22jKYEYKXNT4knYPmjtbFE5fiZP8d
Congratulations @jellysmash! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
Click on the badge to view your Board of Honor.
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!
Congratulations @jellysmash! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!