GOPAX Insight: Enigma
Disclaimer
GOPAX Insights or listing decisions should not be considered as endorsements or solicitations to purchase the featured assets on our platform.
Overview
Enigma is a layer-two solution for providing privacy and scalability to a blockchain. It works primarily by splitting computation among nodes, preventing any single node from being able to piece together the whole. The Enigma team is currently testing their first dapp, Catalyst, an algorithmic investment platform that uses the Enigma protocol as its back-end.
Business Landscape
Current Challenge
Current implementations of blockchains are extremely limited in the dimension of private data storage and computation. While Ethereum has recently integrated the operations necessary for performing computation privately on chain through zk-SNARKs, it is still costly to perform heavy and private computation of any kind on chain.
A centralized alternative can provide scalability and privacy, but at the cost of trust to the centralized host. Companies such as Google, Facebook, and Twitter have nearly unrestricted access to customer information, including location, health status, mood, and preferences. Users are generally unable to control and are often unaware of the extent to which their data is collected and used.
Proposed Solution
Enigma presents a new protocol for distributing, protecting, processing, and controlling access to user data. This is achieved by using a separate network of nodes that handles data storage and computation, while using Ethereum to act as an arbiter and enforcer of correct action, as well as punishing malfeasance.
Current Major Players
While there are no direct competitors to Enigma, its goals overlap with many other projects focused on scaling decentralized systems. Its use of Ethereum and other blockchains as judges of computation results is similar to those of TrueBit, Plasma, and Golem, while its handling of data storage is similar to that of Filecoin. It is likely that as the Enigma protocol develops, it will draw inspiration—if not direct cooperation—from these projects.
For their first dapp, Catalyst, it joins the ranks of other decentralized investment platforms, such as Iconomi, Melonport, and PRISM.
Technical Specification
The core layer of Enigma is a network of nodes that serve three purposes, storage, privacy, and computation. Nodes use a blockchain to provide verification that the results of a transaction are correct and to settle payment, while storing the results of the computation with restricted access to authorized users only.
Secret Sharing and Secure Multi-Party Computation
To understand how Enigma is able to accomplish privacy, it is important to understand the concept of Linear Secret Sharing Schemes (LSSS). In an LSSS, information is split into pieces and can only be reconstructed if a certain number of pieces are present. Typically, the number of pieces created exceeds the number of pieces needed to reconstruct the data. For instance, information may be split into 10 pieces, but only 3 pieces are required to fully reconstruct the information. By using an LSSS, nodes in Enigma cannot piece together the data that is being processed unless nodes decide to cooperate and share their information.
Once information has been split into a large number of pieces in accordance to an LSSS, the pieces are distributed among the nodes for processing. The Enigma interpreter arranges a random selection of nodes into an arithmetic circuit. This means that some nodes process the inputs, then send the results to a different set of nodes until the final result is calculated.
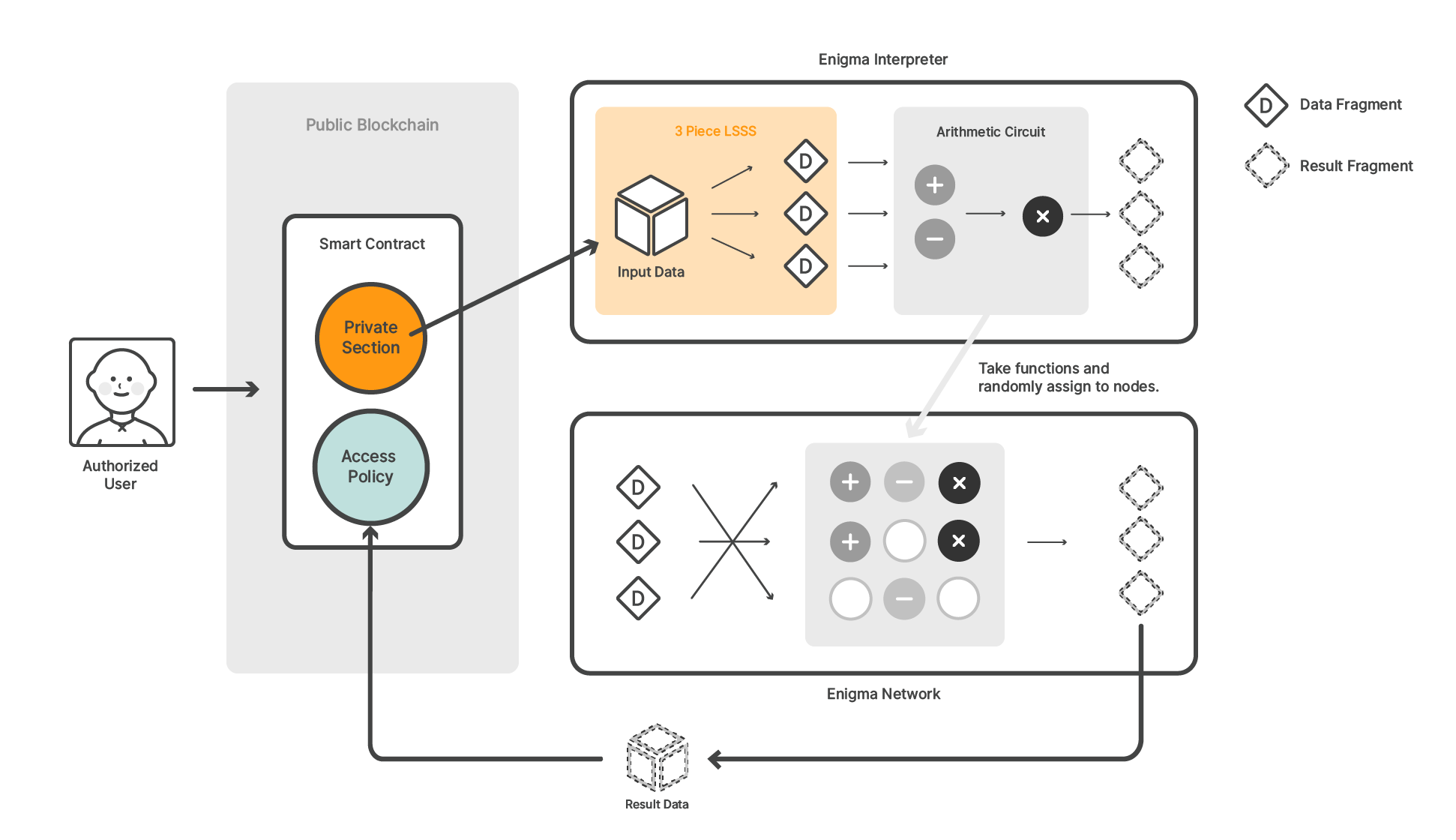
An overview of the Enigma Network.
This scheme also handles privacy, as multiplication and addition operations can be performed without the node doing the computation knowing anything about the data it is changing. Once the computation is finished, a proof of its execution and reference to the result are posted to the blockchain. If an execution proof can be shown to be false, then the node that posted the proof will lose its security deposit, and the computation will be redone by the other nodes that participated in the computation.
Shared Identities and Distributed Storage
When a request to process or store data is made to the Enigma network, the access level of the request is checked by the set of policies defined when the data was stored or computed. The policy consists of a shared identity of permitted users. Only users who participated in creating the shared identity are able to access and read the data that is stored.
Data storage is managed by a simple peer to peer protocol used by popular file sharing systems, such as BitTorrent or uTorrent. There is also a rent structure for storing data. When data is stored, the hosting node charges rent. If the account that owns the data fails to pay the rent fee, then the data will be locked and access restricted for a certain time. If the rent is still not paid, then eventually the data will be deleted.
Data retrieval is done via a retrieval transaction, and a fee is charged for requesting the data. This fee is paid to the node that is hosting the data.
Building Dapps on Enigma
Enigma provides a scripting language for navigating both the off-chain Enigma network and the on-chain Ethereum network. This scripting language allows for the creation of “private contracts”, a combination of logic that creates a smart contract, and logic that handles the private data storage and computation. The Enigma interpreter is also responsible for selecting the sets of nodes used in processing and storing data.
The first dapp being developed on Enigma is called “Catalyst”. Catalyst is an algorithmic trading platform that allows users to both create their own trading algorithms, and invest in algorithms they believe to be successful. Catalyst also allows users to supply data that might be useful for trading algorithms and receive compensation. Because Catalyst uses Enigma, it can scale to a large number of users and store trading algorithms without giving away how they work.
Roadmap and Future Plans
Once development of the Enigma network is complete and Catalyst is working as expected, the Enigma team plans on developing a decentralized exchange (DEX) built on top of the Enigma network. This DEX will expand the capabilities of Catalyst to encompass cross-chain atomic swaps using payment channels, such as the Raiden Network or Lightning Network. The exact implementation details of this DEX are yet to be described, but the Enigma team will plan on releasing future papers to detail the architecture.
In the medium term, Enigma hopes their network can be used to facilitate not just data for trading purposes, but for all kinds of monetizable data. This represents a shift from traditional “customers are the product” model of data monetization to a more direct form allowing customers to control and sell their own data through the Enigma network.
Token Market Structure
Pre-mine and Inflation
There is a total of 150M Enigma tokens in supply, with 75M being distributed in the token sale. 37.5M tokens are to be held by the Enigma team, with the other 37.5M tokens being used for community incentives, exchange listings, etc.
Initial Coin Offering: Sales Model
Enigma performed a capped queued token sale. The individual participation limit depended on whether or not the user registered prior to the sale. Whitelisted users were able to buy more tokens and have priority access compared to non-whitelisted users. The ICO price for each Enigma token was $0.60. There was a hard cap of $45M in the token sale.
Initial Coin Offering: Issues
One month prior to the ICO, the Enigma web page and Slack channel were compromised by hackers, who managed to trick community members into giving up $500,000 worth of digital assets. The ICO concluded on September 11th and proceeded without incident.
Maker Team and Experience
- Guy Zyskind - Co-founder and CEO, Research Assistant at MIT Media Lab, CTO of Athena Wisdom
- Can Kisagun - Co-founder, Co-founder & CEO at Eximchain
- Tor Bair - Head of Growth and Marketing, Data Scientist at Snap, Inc.
- Victor Grau Serrat - Senior Software Engineer, Co-Director D-Lab at MIT
- Frédéric Fortier - Senior Software Engineer, Senior Software Engineer at enChoice, Inc.
Secondary Market
Market Capitalization (USD)
Jan. 22nd, 2018
Source: https://coinmarketcap.com
| ENG Tokens | Price per Token | Circulating Supply | Volume (24h) |
|---|---|---|---|
| $332,510,579 | $4.44 | 74,836,171 | $10,132,200 |
Volume by Major Exchange
| Exchange | Volume % |
|---|---|
| Binance | 41.8 |
| Bittrex | 12.4 |
| GOPAX | 4.28 |
| UpBit | 3.19 |
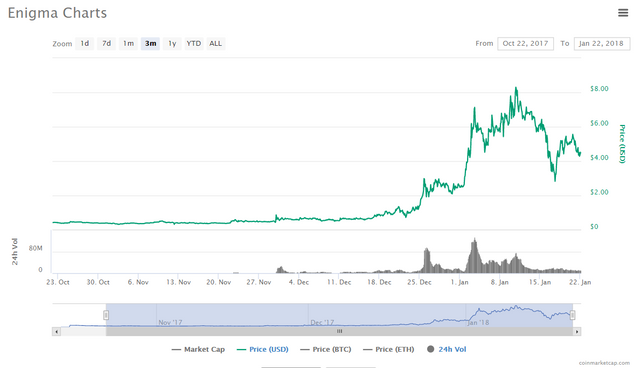
Market Price Volatility
Jan. 22nd, 2018
Source https://coinmarketcap.com
Risks and Limitations
Enigma is an ambitious project that will likely take many years to come to completion. It uses concepts being developed in many other teams, such as the privacy based mathematics of zk-SNARKs and zk-STARKs, two approaches that are very new to both the cryptographic and cryptocurrency communities. Enigma stands much to gain from working with the Filecoin, Golem, and Ethereum Foundation to develop their protocol.
A more systemic risk is that nodes will collude to undo the privacy given by an LSSS computation. While this is mitigated in requiring a security deposit for each node in the Enigma network, a rich and powerful entity (a large corporation or state actor) may be able to create enough nodes in Enigma to piece together data that is split across it. While they would not likely gain knowledge of all activity on the network, it may be possible for them to piece together an appreciable and useful amount of data in the current architecture.
Additional Resources
For more information about ENG tokens, please consult the following resources:
- Enigma White Paper - https://www.enigma.co/enigma_full.pdf
- Catalyst White Paper - https://www.enigma.co/enigma_catalyst.pdf
- Decentralizing Privacy: Using Blockchain to Protect Personal Data - https://www.enigma.co/ZNP15.pdf
- Enigma Blog - https://blog.enigma.co/
- Hackers nab $500,000 as Enigma is compromised weeks before its ICO - https://techcrunch.com/2017/08/21/hack-enigma-500000-ico/
- Enigma’s Token Sale – Full Details - https://blog.enigma.co/enigmas-token-sale-full-details-4d70c56510ba
Final Remarks
We here at GOPAX hope you found this insight useful and enlightening. We are constantly striving to improve the quality of the information presented, so please leave any feedback, including questions, corrections, or suggestions in the comments below!
Congratulations @gopax-insight! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPI think it is not going to cut it; too many doing the same thing out there. Cool name though.... I'll be selling ASAP.
Reader of this comment, you may follow me, i promise nothing; but i am one hell of a personality.
Regards to most everyone.
Coins mentioned in post:
Congratulations @gopax-insight! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOP