V for VeraCrypt - Encryption On the Fly
Protect Your Privacy with VeraCrypt On the Fly Encryption

Today, I would like to share with you a tool that helps keep your personal information and data private through encryption.
I have been using VeraCrypt - On the Fly Encryption - for about 2 years now and it is one of my favorite encryption programs.
In the past, I used TrueCrypt version 7.1 to encrypt files before it shut down operations with an ominous warning that the encryption may not be as secure as previously believed.
This post is meant to teach you the basics of using Veracrypt.
In light of what we’ve learned from the Wikileaks Vault 7 release about the CIA cyber weapons leaked online, many may reasonably assume that all of our internet activity and personal information is vulnerable and that nothing is safe.
Although I agree that the risk of losing control of our personal data is extremely high and probably unavoidable, I also believe that we should not make it a walk in the park for those seeking to remove our rights to personal privacy. At the very least, they should have to work for it.
I use VPNs (the purchased variety) / encryption software / end-to-end encrypted email / TOR and try to be as careful as I can not to give up any unnecessary personal information whenever possible.
VeraCrypt
VeraCrypt is an open-source utility used for on-the-fly encryption (OTFE).[5] It can create a virtual encrypted disk within a file or encrypt a partition[6] or (in Windows) the entire storage device with pre-boot authentication.[7]
VeraCrypt is a fork of the discontinued TrueCrypt project.[8] It was initially released on June 22, 2013 and has produced its latest release (version 1.21) on July 9, 2017.[9] Many security improvements have been implemented and issues raised by TrueCrypt code audits have been fixed (see below). VeraCrypt features optimized implementations of cryptographic hash functions and ciphers which boost performance on modern CPUs (see Performance).
EDIT: VeraCrypt is FREE and Open Sourced
VeraCrypt is a very useful piece of encryption software to help secure your data.
On the Fly Encryption refers to the ease in which you can store this light weight program on a usb/flashdrive and use it anytime anywhere. VC not only enables the user to encrypt their password protected data, but it also hides these files away from view.
There are 2 main ways to encrypt your data with VC
- Encrypted file container
- Encrypted volume within a partition / drive
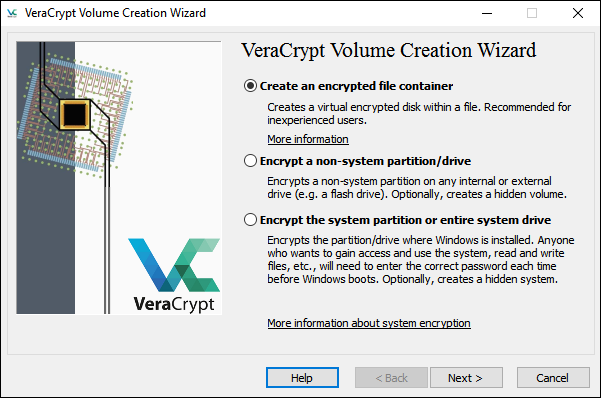
The following section will give you step-by-step instructions for creating an encrypted file container. Creating an encrypted file container allows you to create a volume capable of encrypting up to 4gb (files, folders, videos, etc).
Options 2, encrypting hard drives, is more advanced and Is not recommended for beginners. However, for the average user, simply creating an encrypted container or several encrypted containers is all you’re ever going to need.
Securing Your Data with VeraCrypt
https://www.veracrypt.fr/en/Home.html
Encrypted File Container
After installing the VeraCrypt exe. file
Open VeraCrypt Program
Vera Crypt Volume Creation Wizard

[esecurityplanet.com]
- Create Volume
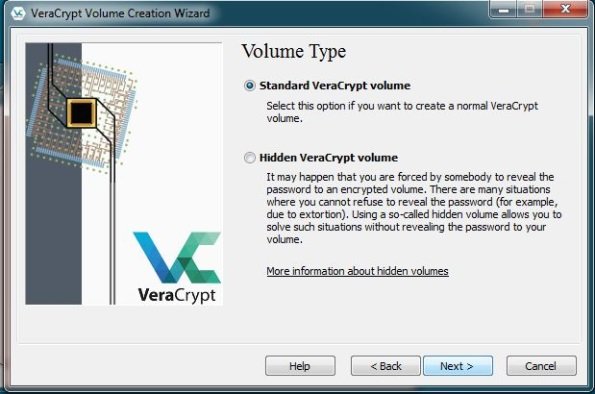
Volume Type
- Select Standard VerCrypt Volume
Volume Location
- Select File Location
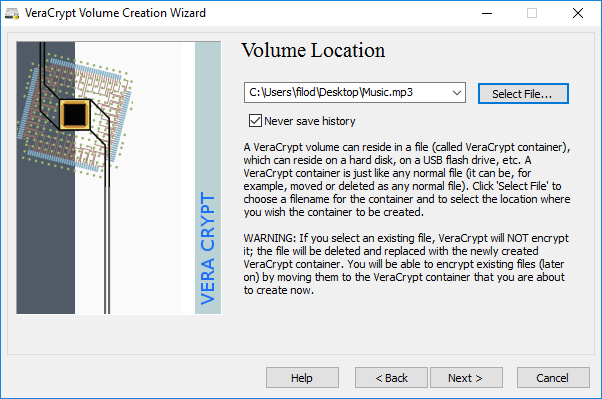
- Chose where you would like to store your encrypted file container (desktop/ documents/ etc.)
- Do not select an existing file, the file will NOT be encrypted
- Note 1: If you would like to store the encrypted file on a USB select the appropriate drive
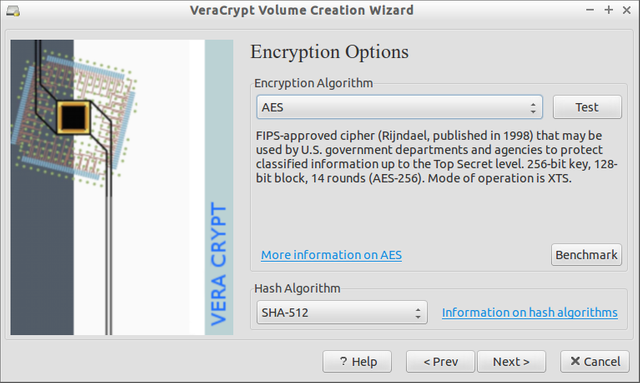
Encryption Options
You can chose between several different algorithms:
- AES
- Serpent
- Twofish
- Camellia
- more
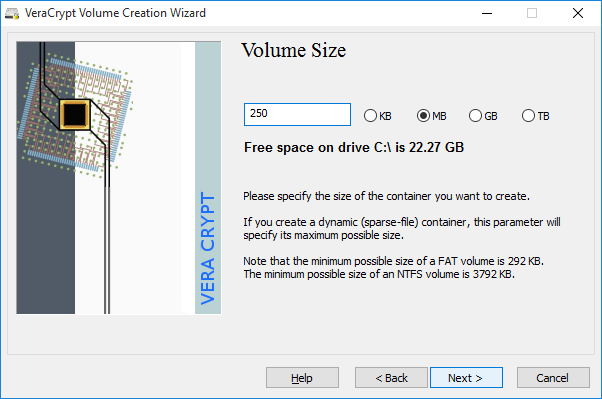
Volume size
Though you will see the amount of free space available for encryption, since we've chosen the encrypted file container option, 4gb should be the maximum size of your new volume.
- Select - 1gb - 4gb
- Select “Next”
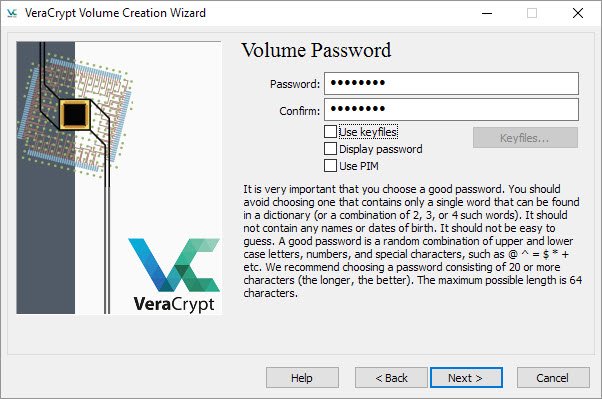
Volume Password
Be careful to select a random combination of letters, numbers and special characters.
- The maximum password length is 64 characters
- Note: I use 32 characters
- Note: Avoid sequential numbers, birthdays and words from the dictionary.
- Use both upper and lower case letters
- Try to make a password that you will remember
- Enter your password
- Confirm password
- Select “Next”
Format Options
- Select the appropriate Filesystem type (eg. FAT) or (eg. Mac users = Mac OS Extended)
Note: I recommend selecting FAT Filesystem if you intend on using this volume across platforms (Mac, windows, linux)
Note: If you’re a Mac user and only intend on using Mac OS then by all means select Mac OS
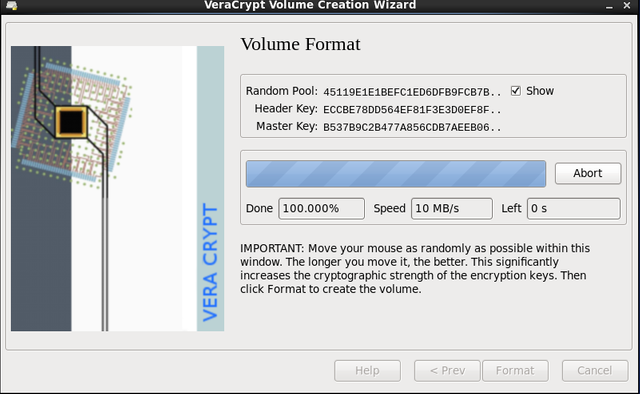
Volume Format
At this stage, move the cursor randomly around the VC Volume Creation Wizard window to increase cryptographic strength.
- Randomly move cursor
- Select “Format”
Encrypted File Container Complete!!!
Mounting a Volume (accessing your encrypted file container)
In order to access your encrypted file container and add files to it, simply follow these instructions.
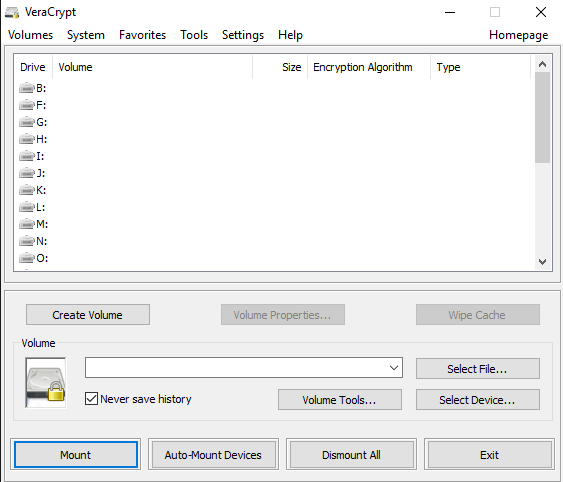
- Open VeraCrypt
- Locate your newly created file container and drag it into the “Mount” option in the VC window.
- Select a drive from the list in the window (eg. X, Y, Z,...)
- Press “Mount”
- Enter your password (may take a few moments)
- Once the volume (file container) has successfully been mounted, a new drive (volume) will appear in the file menu. (eg. If you chose drive Z, then Z will appear in the menu)
- Now simply add the files you want encrypted to the new volume/container by dragging and dropping (eg. File folder X, drag and drop into new volume [Z])
- Remember, the encrypted file container holds up to 4gb
- Once you are done adding files and folders, simply return to the VC window and enter “Dismount”. The volume will disappear from the file menu.
- These files are now protected by encryption and cannot be accessed without the password and VC program.
FAQ
- The volume (eg. drive Z) is dismounted but I can still see the original file in the file location, is it safe?
- Yes, though the file is visible it cannot be opened. To be certain try clicking on the file and/or opening it with any program. Nothing happens.
EDIT/PRO-TIP
When storing and using encrypted file containers on a USB - Also store a copy of VeraCrypt exe file on the USB as well. This way you can run the program on any computer you're using to access your encrypted files.
Conclusion
I hope you find VeraCrypt as beneficial as I do and I hope my explanations were clear. The VC Volume Creation Wizard is pretty straight forward, in any case. If you’re having any problems, please see the tutorial video below, visit the VeraCrypt website or How to Geek website for detailed instructions.
How I Use VeraCrypt - YouTube.com
I don't see myself as a hero because what I'm doing is self-interested: I don't want to live in a world where there's no privacy and therefore no room for intellectual exploration and creativity.
-Edward Snowden
Disclaimer: I am not a security or IT expert. Using Veracrypt doesn’t guarantee your information is 100% safe. It does, however, make your encrypted files more resilient to brute force attacks. Do your own research and find the best encryption options that suit your personal needs.

If you use the hidden volume type and someone changes something in the base directory of the hidden volume it could damage the encrypted files.
Also if you have ubuntu or kali encrypting your full hard disk can be easily done in the installation it is not as efficient as Veracrypt i think... But it has the ability to overwrite all data to prevent metadata leaks.
Great Post!! Upvoted....
(one other thing you shouldn't use tor anything other than recon or information gathering since your info or files or anything you send or receive could be compromised if someone owns a certain number of relays they will track you down.... Vpn's on the otherhand you are relying on the company who hosts it)
Great points thanks for taking the time to comment.
Yeah, I don't recommend encrypting or partitioning a drive in this post. Basically, I just wanted to introduce people to VC and how it can be used for encrypting relatively small amounts of data.
Good points on the VPNs, and I agree that using TOR for recon is how it is best used.
The thing with VPNs though is sometimes people live in countries where the government blocks a lot of websites, and also desire to download files or info that they are prevented from accessing. So, in this case i recommend people to pay for a VPN as they can download with P2P. Of course, you are correct that the companies are tracking our activity, so it is up to us to do our homework and find reputable VPN providers.
No problem your post is great and i had never found a person that shared the same interest that i do in technology just followed for more :)
And if you country blocks websites there is also the possibility to install securityKiss VPN for free in ubuntu since it's a community VPN of course a paid one will be more faster more encrypted and of course depending on the company more "secure" but there are some great free alternatives out there or just bridge a connection into tor altough tor isn't as much secure and is also slower but with a bridge fewer people will be able to notice you're using it.
This is the greatest timely post. I downloaded veracrypt a few weeks ago but I got stuck and confused. This post is a great step by step.
I'm resteeming so i can access it later.
Good job.
I was searching for a simple encryption solution for my personal files. Thanks for the quick tutorial
You're welcome. I use VC regularly and it gives me some peace of mind. Of course, if the NSA or CIA want to get at your data they probably can.
There is some encryption methods that they will need years to break it, encryption is the best tool to privacy for sure
Wikleaks proved the point. The CIA can hack anything. No device or product which contains software is safe.
Thanks for the tutorial @v4vapid. I don't encrypt my files yet, but I have started using a Tor browser on Android.
I guess this is a great way to lock some disk and files.
You may as well heighten your security rather than wait for the unthinkable to occur and letting information get leaked.
I've never used VeraCrypt before, to be honest I never heard of it but I'm glad you are able to share it with me @v4vapid.
I'll be sure to download my client and encrypt some certain things.
Out of all the encryption methods which one do you use? AES?
I have tried AES, Serpent, Twofish and some combinations...honestly there's no perceivable difference. Most people just stick with the default AES though.
the difference is in bruteforce some algorythms are easier to brute and the other have a tougher encryption you won't notice a change unless you try to "hack it" open
haha, yeah really.
The only people who notice are the ones trying to hack in.
Thanks for all this info. And your effort in putting this together.
I just checked it out. And saw that for all that it does it is still free! (Perhaps you should mention that also in your post.) I'm downloading it as I write this and will definitely install and try it out. Thanks @v4vapid!
Happy to hear that :)
Yes, FREE is good and it's open source as well.
If you use VPNs, I would recommend paying for one. The free versions are limited and don't have the option to safely download during use. If you download something, you are easily identified.
I have to get a VPN. Just biding my time trying to understand the whole thing better before I enter it fully. In the meantime, I'm using TOR. However, it is no good for torrenting.
Thanks. Another thing added to my list of things to do.
No worries! Also read this one in a thick highlander accent
hahhahahahahhahahahahahahahahahahhahahahahahahahahahaahahahahhaa.
I completely forgot about this. I genuinely haven't laughed so hard in ages.
Thanks pal
I was an avid Truecrypt user. Used it for many years until it stopped being developed, so I switched to its successor VeraCrypt. All my browser profiles and sensitive data are stored on encrypted container, and I use it to encrypt whole HDDs too 🔒
Encryption is awesome, that's why governments are staging PsyOps to demonize it and demanding backdoors from developers.
https://steemit.com/conspiracy/@lavater/chloe-ayling-kidnapped-by-black-death-group-hoax-another-psyop-to-regulate-bitcoin-encryption
personally I think the NSA already has the technology to crack something like Veracrypt, some say even decentralized encryption ala Bitcoin will be at risk with the NSA's Quantum Computer, though for now seems to be beyond their reach. I guess it is a cat & mouse game. Encryption hopefully will be always one step ahead of the controllers.
Veracrypt surely helps protect files from your average hacker intrusion, so surely worth using.
Thanks so much for very detail article about Veracrypt.