100 Days to Cyber Security Literacy (Day 3): Cyber Security Steemers & Password Managers
Welcome to Day 3 of “100 Days to Cyber Security Literacy.”
On Day 2, we talked about some introductory models of how to assess cyber threats and the associated terminology. We went on to discuss how to make a better password.
In my personal studies, the amount of information I am taking in is enormous. I have started learning about network concepts, and the truth is that if I write about everything I am learning each day these posts will be 10 pages of terminology. That does not make for a readable post!!!
I am going for a format where I touch on one “definition of the day,” possibly something from Cyber Security news, and then mainly focus on practical tasks that can move us forward.
First, Some Shout-Outs…
Go check out these Steemers that have Cyber Security content.
First, we have @citizen4, who is putting out some fine articles like “The VPN Illusion”. If you don’t know, a VPN (Virtual Private Network) is a service that you subscribe to. For your money, you get to connect to their servers, and then all of your internet traffic goes first to them and then to the greater internet. In other words, the only activity that your internet service provider sees is that you connect to the VPN service each time. In theory, the only folks who know about your internet activity are those in the VPN company.
BUT…
@citizen4 reminds us, first, that these companies can quite easily fold under the pressure of state actors. He also underlines, that as companies rush into the growing market for this service, the quality of the service, for example their own internal security procedures, is far from uniform. While this is a good security measure for the average user, especially against low- to mid-level attackers, it is far from being a magic bullet. Go read his article!!!
Next, we have @seymourbucks who seems to have launched a “Let’s Hack” series. He seems to know a heck of alot more than us, so we are going to watch his series closely for some practical exercises that up our own security game. At this moment, there is a number two in the series that I haven’t taken a look at yet. Thank you, @seymourbucks, and we’ll be watching!!!
One step further towards password strength…
On Day 2, we went through a simple method to create a stronger password:
Use a password generator to create a random string of numbers, letters, and characters.
Create a sentence or two as a mnemonic to memorize the password.
After 10-2000 times, the process of translating the sentences into your password will come naturally.
But is this strong enough? If you use a few sites that have sensitive personal information, then ideally, you have a different password for each. If you are reading this, you can easily imagine having a Steemit account, an Amazon account, and your personal e-mail account. Let’s assume an attacker that somehow gets the password to one account can find wherever else you have a presence, and then, use the same password to get into your other accounts.
Are you supposed to create more sentences to remember more randomly generated passwords for every site of importance that you use? Well… That is not impossible, but in our brave new world of automatization, you have another choice: a password manager (or password safe or password vault).
It is a form of software that will remember all of your passwords and plug them in where needed. Thus, we could have a strong, randomly generated password for every site we use. Furthermore, this article tells us that browser-based (Chrome, Firefox, etc) password managers can have some shoddy security practices such as storing your passwords in an unencrypted form on your computer.
BUT… At this young moment in our Cyber Security lives, I like the personal responsability of making a good password and remembering it.
Lingo of the Day
If, like me, you are following some kind of online course in Cyber Security, then, in the technical sense, you are well beyond what I write about here. I am currently exploring networking ideas and principles. A fundamental idea is…
End-to-end & point-to-point communication
How does a communication, like an e-mail, get from your computer, the sender, to another computer, the receiver?
There are protocols, fixed sets of rules, that allow information to be sent and then understood to be information at the receiving point. There might be several computers, called routers, between the information that you send and the receiver. How we get to the next computer is point-to-point communication. The protocol that gets that information through a maze of routers to the receiver is end-to-end.
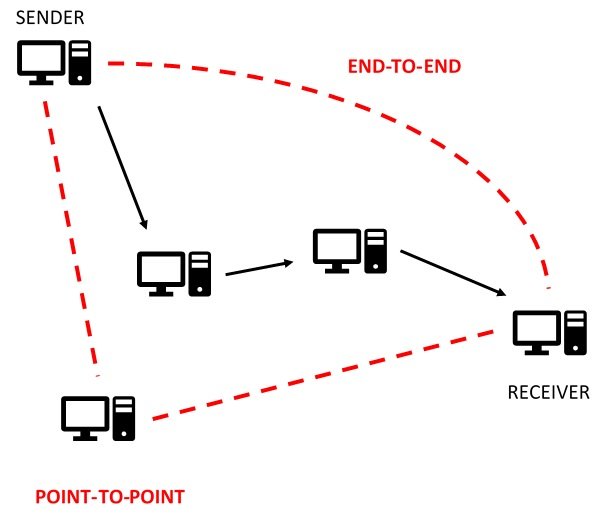
Brought to you by: MS Word!!! and licensed under ME!
It is NOT just a series of point-to-point communications. The TCP/IP protocol (a bunch of rules for doing all this stuff) can break your message into packets of information, each possibly taking another route to the receiver, and putting them all back together as a pretty, pristine e-mail. THAT is end-to-end communication
The Elephant in the Room
So… I still haven’t told you about how we will run Kali Linux easily from our, usually Windows, machines. It is super easy! I promise!
Hope to see you at Day 4!!!
That helps. Thanks
And thank you!!!
I would upvote you but my vote power is trashed right now.
I am approaching this from close to zero knowledge, so I am honing in on a format that touches on practical points that will be accessible to most folks that would follow the series (and started, like me, with little security background) but also respecting a sort of vector of development.
A good example is the article I cite by @citizen4. It begs the question, "Well then... How do we choose a VPN? A Google search doesn't seem to enighten the situation." That is a perfectly practical situation that hopefully we can treat soon.
If any questions come up for you, don't hesitate to ask. Maybe, we can find an answer together.
Best wishes!