What is SIEM? What sort of cybersecurity risks does it prevent?
TLDR readers: Security Information and Event Management is a software tool that can be used by Information security to detect event anomalies in the system. It requires setting up the right parameters and therefore an experienced CSIO or other company officer. I go through the more common use cases for SIEM including brute force attacks and compromised log source events.
SIEM stands for Security Information and Event Management. Because information security (also known by the more popularized term cybersecurity) has developed enough complexity over the years that there are now specialized SIEM positions in every major corporation. This is partly due to the amount of data generated, stored, and transferred. Big data incentivizes security threats, and if a company is ever going to secure it’s data, than SIEM is already part of its corporate structure. Sometimes, not enough resources are spent in this department as multi-billion dollar companies still fall victim to cyber breaches. Then again, the larger the data set, the more it would attract highly skilled hackers. The tools used to aid the SIEM professional have also evolved to keep up with the continued resource allocation into this field, but first let us understand what is involved in SIEM.
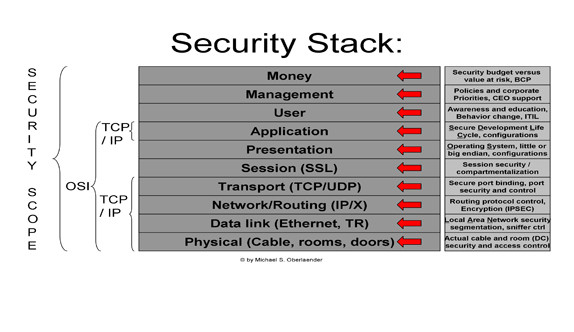
Michael Oberlaender’s book “C[I]SO-And Now What? How to Successfully Build Security by Design” provides frameworks for security architecture based on his experience as a Chief Information Security Officer. IT ‘stacks’ are ubiquitous and refer to a group of technologies that work well together to produce a desired outcome. In this case, Oberlaender defines a 10 layer Security Stack as shown above. Essentially an easy guide to troubleshoot if the desired outcome is not produced. Is it a physical problem? Is the network breached? are config settings for the presentation not compatible? Is the user’s behavior the cause of information compromise? Now that we have a general idea of all the layers where things can go wrong from the physical layer up to IT policies and procedures, we need to find a way to (1) prevent, (2) monitor, and (3) correct. The monitoring function of the SIEM professional or advanced SIEM tool is also known as ‘Event and Log Collection’ and has some build-in alerting function if compromise is detected. This monitoring function is in the form of an analytics dashboard that monitors all activity in a secure system and based on pre-specified events, it alerts the SIEM professional. The SIEM professional takes this information and prevents cyberattacks by placing safeguards. The simplest example is limiting the number of login attempts by a user. If an event is recorded, the SIEM professional then must find out how it can be prevented further in the future. As you can see this is an iterative process, and why experience is one part of the capability of a SIEM professional. So prevent, monitor, and correct seem straightforward, so does event logging software with a useful analytics dashboard. Let’s look at a few use cases:
Brute Force Attack: some hackers use a brute force trial and error method (by machine ofcourse) to decode encrypted data. Auditing a system can count the number of logs a user attempts, and depending on any safeguards can prevent the user from attempting to log-in, or can alert the system administrator of the multiple attempts made. Brute Force Attack applications can even be used to test one’s own network security. John the Ripper is one example < http://sectools.org/tool/john/>.
Authorized User, but Unauthorized use: This happens a lot in an organization, and can be safeguarded by limiting access (for example, a neurology physician cannot access the outpatient list of general surgery patients), or by monitoring. AUM or acceptable use monitoring logs a user’s activity or logging activity of a specific asset or resource (again, many medical records now record the user and the date and time of access). Actions can also be audited. If a user deletes a file, copies a file, etc. there will be a digitalprint left behind. The simplest form of AUM safeguards that the millennial generation has seen is trying to access our twitter account from work or from a public library and getting a browser page that says ‘unauthorized’.
Application Defense Check: It’s easier to set up monitoring of systems and networks than individual applications, but given the amount of big data stored in applications like SQL, or in Hadoop clusters, it becomes important to monitor and protect against unauthorized use at the application level. The most common safeguard is use of a Web Application Firewall (WAF) that monitors traffic and prevents traffic based on administrator defined specifications.
Compromised Log Source: Imagine that a hacker found access to your system or to a specific application and quickly disabled the event log monitoring of the light weight SIEM agent software installed. As a safeguard for such an event, SIEM software is configured in such a way to alert the main manager system (that collects the log feeds) when the log feeds stop arriving, thereby alerting to a potential breech or potential malfunction.
Unexpected Events Per Second (EPS): if the log sources are sending a large number of events per second, this should raise an alert, as it is one way hackers have found to move undetected. They flood the manager system with fake information so that the bandwidth is bogged down and the real-time analysis dashboard is more of an after-time analysis allowing the hacker to get away before a system alert is raised or action such as disabling the system from taking place. This flood of information to decrease bandwidth is a common tactic that we’ve seen in the Distributed Denial of Service (DDoS) attacks < http://www.digitalattackmap.com/understanding-ddos/>.
There are many more use cases, but I only aim to elucidate a concept. The tools at the disposal for SIEM and for the SIEM professional are impressive and continue to get more sophisticated. Splunk and IBM QRadar are just two tools used for Information Security of Big Data. Below are two company marketing videos to showcase their value proposition. Keep in mind that although SIEM is technically all encompassing, the acronym is usually used to describe recording current or past events, while ‘threat intelligence’ looks to the future and uses actionable intel to safeguard a company’s IT assets. Tools such as Splunk and QRadar can do both. Caution: The ads are not very appealing, but maybe they resonated with the targeted audience.
Referenced Links:
Joe Piggee Sr. What Is a SIEM? Tripwire. Accessed from https://www.tripwire.com/state-of-security/incident-detection/log-management-siem/what-is-a-siem/
Michael S. Oberlaender (2013). Book excerpt: ‘C[I]SP: And Now What?”. Accessed from < http://www.csoonline.com/article/2133110/security-awareness/book-excerpt---c-i-so--and-now-what--.html>.
Gartner IT Glossary definition link: http://www.gartner.com/it-glossary/security-information-and-event-management-siem/
InfoSec Institute (2014). Top 6 SIEM Use Cases. Accessed from < resources.infosecinstitute.com/top-6-seim-use-cases>