Secure Your Linux Server with a Firewall
A firewall is the last point of contact before anyone in the vast internet can get into your server. Getting a firewall up is crucial before deploying a server online.
UFW means Uncomplicated Firewall and is included in Ubuntu. Iptables is the standard firewall built into Linux and is more popular for the experts to do more complex rulesets. UFW allows a user to create iptables rules through a simpler interface.

Installation
UFW is included in Ubuntu. If yo haven't recently, just do a quick update:
sudo apt-get update
Check UFW status:
sudo ufw status
It should say "inactive".
Configuration
sudo ufw default allow outgoing
sudo ufw default deny incoming
For SSH, do either:
sudo ufw allow ssh or sudo ufw allow 22
Now run:
sudo ufw enable
You will get asked:
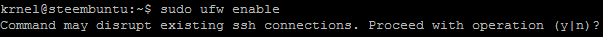
Choose "yes". I didn't lose my connection.
Finally, do:
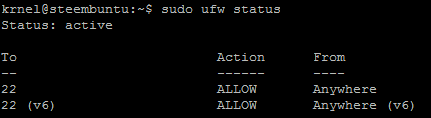
ufw status
And you will see UFW is up with SSH port 22 enabled.
Additional Options
Changes can also be made to the config file at:
sudo vi /etc/default/ufw
If you make changes to the config or through the command line, do sudo ufw disable and sudo ufw enable again. sudo ufw status will always tell you if its on or not.
To deny port traffic you can do: sudo ufw deny 111
This can apply with any port used for an application, like http, and apply to TCP or UDP segments: sudo ufw allow http/tcp and sudo ufw allow 1725/udp. Just do the ssh allow command for now. More advanced setting allow for allowing or blocking by specific IP as well.
If ever you want to remove a rule, use: sudo ufw delete allow 22 or ssh instead of 22.
If you want to see the logs in /var/logs/ufw, then enable logging with:
sudo ufw logging on
There are more parameters for the logging, please check the wiki for more info.
Summary
To get started, here it is all in one:
sudo apt-get update
sudo ufw default allow outgoing
sudo ufw default deny incoming
sudo ufw allow ssh
sudo ufw enable
And that's it for now. Firewall setup completed!
All outgoing connections from your server to the internet are open, and all incoming connections from the internet to your server are closed off, except port 22 for SSH. If you setup a webserver, port 80 needs to be opened unless you change the default port. Any other program to allow external access needs the port opened as well.
Setting this up is almost a breeze, it types itself. If you want more power, check out iptables!
Thank you for your time and attention! I appreciate the knowledge reaching more people. Take care. Peace.

 Payout Selected
Payout SelectedIf you appreciate and value the content, please consider:
Upvoting  , Sharing
, Sharing  and Reblogging
and Reblogging  below.
below.
@krnel
2016-11-30, 6:35am

Great guide. I'm just getting into gufw, which is kind of like Little Snitch in terms of graphical firewalls.
Thank you for your request to include this post in the STEEM BOOSTER list! The post is approved because you powered up minimum 100 STEEM in the last 24 h and you are not currently powering down!
top post✓✓
Hi, I am new witness, my witness name is @exnihilo-witness.
I have setup my ssh connection to my server and I have changed my ssh port from 22 to xxxxx in the /etc/ssh/sshd_config.
If I follow these commands
sudo apt-get update
sudo ufw default allow outgoing
sudo ufw default deny incoming
sudo ufw allow ssh
sudo ufw enable
I understand that I will enable ssh on port 22.
So instead, I must do
sudo ufw allow xxxxx/ssh.
My question is how my server communicate with the blockchain?
If I do that, will I miss some blocks?
Does the blockchain communicate with my server by ssh on port xxxxx?
It is not possible, how blockchain will know that I have chosen the xxxxx port?
I hope that you understand my point.
In summary, after setting my firewall, I am afraid to deny the treatment of blocks which is the aim of my server and my witness purpose...
Thank you in advance for your help.
Thank you very much. I think it's very helpful.