Top 5 Strategies to Strengthen Desktop App Development Against Cyber Threats
%20(1).png)
With the surge in cyber threats, securing desktop applications has become a critical focus for developers and businesses alike. Cybercriminals are constantly seeking vulnerabilities, making it essential to integrate robust security measures throughout your desktop app development process. Below are the top five strategies, each expanded to provide deeper insights and actionable steps for safeguarding your applications against cyber threats.
1. Prioritize Secure Coding Practices
Secure coding is the cornerstone of any well-protected application. By writing clean, secure code, you minimize potential vulnerabilities that hackers could exploit. This approach encompasses several key practices:
Input Validation: Ensure all user inputs are thoroughly validated to prevent injection attacks like SQL injection or cross-site scripting (XSS). For instance, sanitize input fields to reject any malicious code.
Avoid Hard-Coded Credentials: Use environment variables or secure vaults to store sensitive information like API keys and passwords. Hard-coded credentials are an easy target for attackers.
Adopt Code Analysis Tools:Implement static and dynamic code analysis tools to identify vulnerabilities early in the development cycle. For example, tools like SonarQube can provide detailed insights into your code’s security.
Regular Code Reviews: Establish a routine for peer code reviews to ensure compliance with security standards and best practices.
By embedding these principles into your desktop app development process, you build a strong foundation for your application’s security.
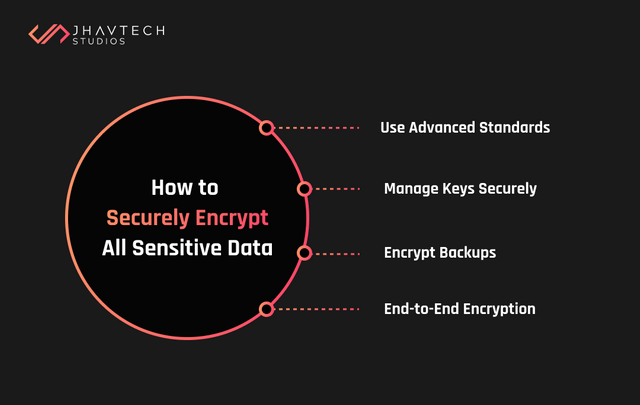
2. Encrypt All Sensitive Data
%20(1).png)
Encryption is essential for protecting sensitive data, whether it’s at rest or in transit. A lack of robust encryption exposes your application to data breaches and unauthorized access. To implement encryption effectively:
Use Advanced Standards: Employ AES-256 encryption for data storage and HTTPS protocols for secure data transmission. These standards ensure your data remains unintelligible to unauthorized entities.
Encrypt Backups: Ensure all backups are encrypted to prevent data leaks in case of a breach. For example, database backups should be stored in encrypted formats.
Manage Keys Securely: Use a dedicated key management system to handle encryption keys. Rotate keys periodically to reduce the risk of compromise.
End-to-End Encryption: If your application handles sensitive communication, ensure that all data exchanges are encrypted from sender to recipient.
Encryption acts as a protective shield, safeguarding sensitive information even if it falls into the wrong hands. This step is a vital aspect of any desktop app development project aimed at creating secure software solutions.
3. Implement Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) adds an extra layer of protection, making it significantly harder for attackers to gain unauthorized access. Incorporating MFA into your desktop app development process provides numerous benefits while also enhancing the user experience by balancing security and convenience:
Enhanced Security: Even if an attacker obtains a user’s password, MFA ensures they cannot access the account without the additional authentication factor.
Diverse Authentication Methods: Use methods such as biometric verification (e.g., fingerprints), time-based one-time passwords (TOTP), or hardware tokens for a robust MFA system.
User Awareness: Educate users about the importance of MFA and guide them through its setup process for seamless adoption.
By making MFA a standard feature, you can significantly reduce the risk of unauthorized access to your application. It also demonstrates your commitment to prioritizing security in desktop app development.
4. Conduct Regular Security Audits and Penetration Testing
Proactive security measures like audits and penetration testing help identify and mitigate vulnerabilities before attackers exploit them. Here’s how to make these practices more effective:
Automated Scanning: Use automated vulnerability scanning tools to detect potential weaknesses in your code and architecture.
Professional Penetration Testing: Hire ethical hackers to simulate real-world attack scenarios and uncover hidden vulnerabilities. Ensure these tests are conducted periodically and after significant updates.
Compliance Checks: Regularly evaluate your application against industry security standards and regulations to maintain compliance and build user trust.
Integrating security audits and penetration testing into your desktop app development lifecycle ensures continuous improvement and resilience against evolving threats. These measures create a secure environment, fortifying your application against known and emerging risks.
5. Secure API Endpoints and External Integrations
APIs often serve as a bridge between your application and external systems, making them a prime target for attackers. To secure your API endpoints, take note of the following:
Strong Authentication: Implement OAuth2, API keys, or other robust authentication mechanisms to control access.
Data Validation: Validate all incoming and outgoing data to prevent injection attacks or data corruption.
Rate Limiting and Monitoring: Set rate limits to prevent abuse and monitor API usage for unusual activity, such as a spike in requests.
Encryption: Ensure all API communications are encrypted to safeguard data in transit.
By protecting your API endpoints, you eliminate a common entry point for cyber threats and enhance the overall security of your desktop app. Strong API security is integral to building trustworthy software in desktop app development.
Final Thoughts…
Securing desktop applications is an ongoing commitment that requires attention at every stage of development. By prioritizing secure coding, encryption, MFA, regular audits, and API security, you can build robust defenses against cyber threats. Remember, desktop app development is not just about functionality—it’s also about ensuring your applications remain safe for users in an increasingly hostile cyber environment. Staying proactive, continuously updating your defenses, and adhering to best practices will ensure long-term success and security for your software.