Cyber protection in your own life

In this digital age, we all are connected to the network in some way or the other. Starting from Facebook, Instagram, YouTube today, smart TVs are taking up space from home. Many of us use different websites on our smart phones or computers, all of which are very trustworthy and difficult to understand. There is a growing debate about the use of social media. Many think that the use of additional internet is calling the value of deprivation of value. Many people think their security is wasting their security. However, there is no way to deny that the life of the network continues to be as easy as increasing the range of networks.
We all want to use the protected Internet. But I do not understand what work should be done or not. In order to maintain its privacy in the cyber world, there must be some basic technical knowledge. We will discuss some topics from him.
Phishing scams
Phishing or phishing is a type of online scam where criminals try to get your personal information from you by sending an email to a trusted company name. It is generally believable to see such emails or messages. But do not let these criminals fool you. It is usually easy to believe that falling into trouble is very easy.
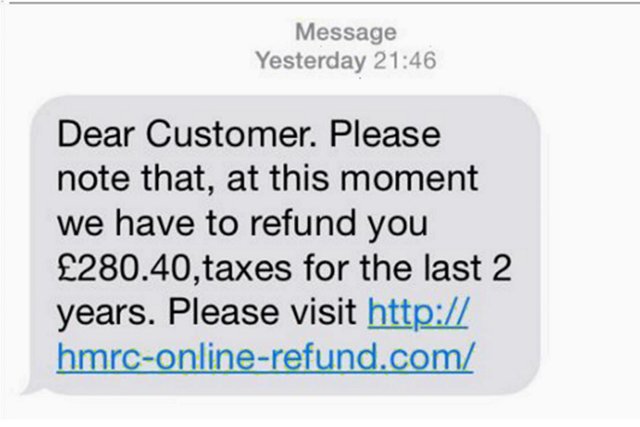
So what is the way to survive?
It is good to avoid email or message if you want your bank account number or password or any security number. The original company already has these information and they will never ask for your information via email. Do not click on any link sent via email or message. This link can take you to a website that looks like a real website and you can hack your account using your information provided there. If you want to access an account, enter the address yourself into the browser without using any of the links sent or use any bookmark you have created yourself. Copying the address sent to the message or email / message sent to the phone number is not good call.
Another method of catching phishing scams is the mouse test. You can see the actual address if your cursor is over the link sent. Read the address well. If it does not have the address you want to visit, then try to deceive you. Sometimes, the name of the company's name is made in small changes and it is used as a fake name, so that it is not understood if you do not pay too much attention. "Your account will be closed if you do not verify within 24 hours." Do not be afraid of such messages. Such messages have been spreading fraud for a long time. If you think in any way that you have given your personal information to any deceiver, then immediately tell your bank or credit card company. If the information is your social media password, then change the password as soon as possible.
Identity theft
We use the network for entertainment, shopping or social communication. But some people use the network to steal someone else's identity.
By using some methods you can survive from these thieves.
Try to trim a piece of pieces before leaving your belongings or personal information, such as a bank receipt or something like that, in case you fall into someone's hand, you are not in danger. And yes, there are people who try to steal your identity in the dirty trash you put. Risk taking does not make any sense. Remember when you are watching a smart TV, smart TV is also watching you. That is why it is called 'smart'.
Before completing the registration form online or signing up on a site, read their policies and conditions well. If you think they do not need to know these information about you, then do not sign up or try to use a made name for yourself.
Take care of phishing scams. If you do not have a transaction through email from your bank, then enter the bank's website by typing it yourself. Before placing your information, make sure that your browser has a picture icon icon. This icon indicates that your connection is safe. But if you have this icon then you can not be sure that your information is likely to be read by someone else. However, if you do not have an icon, then your connection is not safe enough. Find out your account and credit / debit card to know if your bank account is safe. If you feel that you are being victim of identity theft in any way, contact the authorities immediately, tell the police and close your related account.
Suitable password
Your password is like a lock of your house. Break the lock if it is weak, it is easy to break into your home, it is easy to break into your profile if it breaks the password. Once you are able to enter, it is not difficult to harm you. All your personal and financial information will be left to someone else.
Use a password that is so hard and easy to guess
Many people write down the mobile or books in fear of forgetting the password. This is not a good practice at all. If you have to write down, write down so that no one else can understand that this is your password. Still, it is better to try to remember the password rather than risk. Your Social Media Profile is Completely Your Personal Matter So do not give your password to anyone.
Security settings
Almost all social media channels are concerned about the security of customers. You have the chance to block someone and complain against anyone if you bother.
If someone bothers you in any way or if you are not interested in contacting him for any reason, you have the right to block him from your profile.
To use any new medium, find out these settings at the beginning. If you can not find yourself for any reason, then confirm your security issues with a close friend or Google help at the beginning. And under this setting do not just block / report, there is much more. Who can see your posts or who can not, what information on your profile does not want you to know everything - you can control everything. Take a few minutes to fix them properly. It's a good idea to not connect with strangers with anyone unnecessarily online.
Malware
Another thing that everyone should have an idea about is malicious software or malware. In some websites, we unknowingly made these malware available on our computer / phone. Malware may sometimes come from some good websites. But usually your computer is attacked by some bad websites, which have been created to spread malware.

And sometimes you may find that malware can come to your computer even after downloading a file.
But the question is where malware is the problem, where?
Many of us do not know how bad the malware might be. The least frightening possibility of deleting information from your computer. With the help of malware, it is also possible to steal other's credit cards or passwords, send spam email to others from infected computers, and even attack other computers or networks. That means you can become guilty by only invoking malware attacks without having committed any offense.
If your browser does not want you to take you to a website, then your computer or phone may be infected with malware. To avoid this situation, it is good to follow some rules.
Upgrade your operating system and all apps as well as new versions. Avoid downloading something unknown or unreliable from a website. Before entering the link sent to someone, think that he can believe what he has sent. Sometimes a spam link may be sent to you if you have a friend's ID on Facebook. Look at his behavior before entering the link and make sure that something happened has happened. And of course, use a good anti-virus and update regularly. These softwares can not be stopped by malware, it can be removed from your computer and deleted. Besides, an add blocker or malware blocker will also help a lot for your browser.
Whether on the Internet or in real life, the lack of caution can be at risk any time. If you pay a little attention to your safety, then you can survive from these dangers. Do not think after the danger, think before working and have a safe life
I realized that too! I earn mostly from whales, but I'm looking forward to the day that the nation will create hundreds of votes that are more diverse on stem communities!
I'm going to resteem your post and, hope it creates a conversation. And I will self upvote my comment, rarely do I do this but I want to be higher up on your comment section.
Learn well. be of great help!!
I'm going to resteem your post and, hope it creates a conversation. And I will self upvote my comment, rarely do I do this but I want to be higher up on your comment section