Cryptography / Information Exploration! An unknown section of sign-in communication
Hacking is an art or art. I believe with Anonymous "All information should be free." Just as we do not have the basic knowledge of higher mathematics / calculus, we can not do anything special if we do not know Hacking's basic hacking grammar.

Cryptography is a branch of computer science security, in which research is done on various ways of concealing information.
Information processing is the practice and discussion of secure communication methods in a third party's presence.
Notice the presence of modern information in various fields of mathematics, computer science and electrical engineering. There are practical applications for information on ATM cards, computer passwords, electronic commerce or e-commerce.
Example of cryptography
Answer: Suppose you have a message like "I LOVE YOU"
If you want to send someone you like, then you have reverted the message to "L OLNH BRX" by reversing the message. Or reverse "XЯᙠ HИ⅃O ⅃" who sent it, which nobody can understand.
Thus sent him to Because if someone sees the straight message, then it may be lost. Now, everyone saw the message, but no one could understand anything because the message was sent to H-j-bar or hijabjee. But the person who sent him understood exactly how the message was reversed. Occasionally someone who came to know him took the letter, but he did not understand. : P is so funny !!
Reverse / mirror the text itself, from this site, http://txtn.us/mirror-words
Let's know the definitions!
Plain Text: The data that can be read as plain, plain text. E.g., "I LOVE YOU."
Encryption: Encryption is an incomprehensible form of plain text.
Cipher Text: The cryptic text that can be found in encryption.
Decryption: Decryption is the process of bringing the cipher text back to plain text.
Cryptography Process:
Important information (Data Entitlement Information) is stored and sent in different ways (such as the Internet) from one place to another, cryptography is used in all cases, so that un-authorized someone can not understand it.
On the other hand, cryptanalysis is the science to break through synchodic communication! This is mostly unlawful.
And the sum of these two sciences is cryptology.
The key weapon of cryptography is a cryptographic algorithm or cipher, by which data is encrypted, or encrypted data is decrypted. It's basically a mathematical function. This algorithm works with a key. It's a word, number or phrase to get from this key. The same plain text will be converted to different cipher texts with different keys.
Security of encrypted data depends on two things:
(1) The power of cryptographic algorithm
(2) Key Security
Traditionally, both encryption and decryption are done through the same key.
Some movie names for enthusiasts with cryptography
"The Imitation Game"
"The Vinci Code"
You can take a look at these two movies. Interest will be increased and you can take a look at the activities of cryptography in bigger battles.
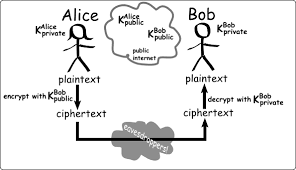
In brief, hiding information is called cryptography. It is a huge science on which the graduation certificate is given. So in my topic cryptography, I first got cryptography. Do not talk about encryption & decryption. Stay close till: P
Cipher: Using the algorithm that is used to hide information hidden or hidden data is called cipher.
Encryption: Hiding data using Algorithm. Ex - Caesar Cipher It's the first of the world
The cipher, many of them are called Shift Cipher or ROT-13 / Rotational Cipher.
With this, the letters of the English alphabet are ascending, then the data is encrypted.
Decryption: The encrypted data is followed in the same manner as the encrypted
Rescuing plain text is called decryption. To decrypt it must be correct key
(encrypt steps and methods). Statistician probability of retrieving data without Correct key
Ra has said once in a trillion times! Which is roughly near impossibility :)
Cryptographic Hash Functions: This is a criterion by which a data / plain text
To be construed as a free block / arbitrary block of data. It should be kept in mind but not encryption
But how to encrypt

Hexadecimal: hexadecimal is a Cryptographic Hash Functions.
Where only 16 characters are used while data encrypt / decrypt. These are 16 characters
Being 0-9 & A-F It's a 128 bit / 16 byte value. It is called base-16.
The most popular hexadecimal hash value is MD5.
Base-32: Base 32 is the hash value of the character. It uses A-Z and 2-7 characters.
An example is: d41d8cd98f00b204e9800998ecf8427e
Base-64: base 64 and a hash value. It uses A-Z and 0-9 and some special symbols.
Base 64 always ends with "=". Example: 1B2M2Y8AsgTpgAmY7PhCfg ==
Collisions: When 2 different hash values will have a similar encryption, then the server
This creates confusion. This confusion is called collisions. It's actually a blessing for hackers. They got it
Love is called "God mode birthday attack". If in collisions.
nice post
thanks bro