Cryptography: What is Cryptographic Hashing?
Cryptographic Hashing
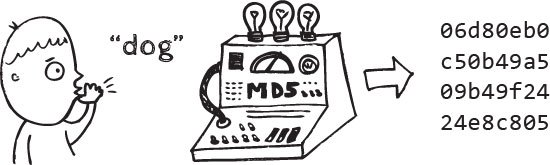
A cryptographic hashing algorithm is a mathematical function that takes any sized blocks of data and returns fixed size bitstreams and we are not going to go into the math behind hashing. No matter what size of the input the digest is a fixed length. Even though we just have the word Fox for this input, we get the same 40, digit, hexadecimal or 160-bit message, digests that we do for any of the other inputs, no matter how long they are. Even with the tiniest change just one letter between over an hour, the resulting message digest is drastically different. It is not, as you might have expected, the same for most of the characters, with just a few numbers or one block being different. This is a good thing now, even when the letters are the same, except for two of them are in a different border. We still have completely different message digests. This is a desirable attribute of a good hashing algorithm.
We start with our message in plain text, we run it through the hashing function and we get the resulting message digest or hash value you take that hash value and encrypt it with the sender’s private key. That is one half of the asymmetric key pair remember the result is the digital signature. We take that digital signature and attach it to the message and then send the two off together to the recipient, now notice that the message itself is not encrypted in this example. So that means we do not have confidentiality. Encryption could be added to the message if we wanted to, but we did not have it for this example now on the recipient, send they receive the message and the digital signature. Now the recipient needs to perform two distinct functions on these two various parts. One function is to take that message: run it through the same hash function and get a resulting hash value. The other thing they need to do is to decrypt the digital signature using the sender’s public key now remember, the sender’s public key can only decrypt things that have been encrypted with the sender’s private key, and only the sender has that key. So, if this works, we now have verified that the sender is in fact whom we think it is. That’s authenticity and the sender cannot later say “Hey, that was not me that sent that message.” That’s non-repudiation, so the recipient has two hash values. They compare those two hashes if they are the same, we know the message has not changed during transmission. That’s data integrity.
When encryption is used to protect transmissions that pass over the Internet. That is called transport encryption transport encryption adds the benefits of cryptography, vatu, otherwise insecure protocols. This is for confidentiality and to prevent man-in-the-middle attacks. So, with transport encryption, a VPN is secured with IPSec. We have talked about this in other lessons. Also in web browsers, TLS and SSL can be applied to many different situations like the unsecured HTTP will become the secured HTTPS and for data transfer and remote management. Secure shell takes the place of the internet and SFTP takes the place of FTP. Remember I said that we can use symmetric and asymmetric together with impressive results, while TLS is an example of this hybrid TLS uses asymmetric encryption for the key exchange, but then symmetric encryption is used to protect all future communications again, the best of both worlds.