Attributes of the Ultimate Cryptocurrency
Future proofing cryptocurrency!
Intro
There is always a chance for improvements, however improvements shouldn't occur at the foundation as a weak foundation will eventually collapse. If the foundation is strong then improvement at higher levels is positive. As of yet, there are no defined cryptocurrency foundation attributes. What are the attributes that defines the ultimate cryptocurrency? This is a list of the most important attributes in order of importance, any cryptocurrency must establish these attributes as a foundation in order to become relevant in the future.
1. Anonymity
Anonymity is the inability to distinguish an individual, and the inability associate an individual with an act. This is first on the list because it protects the users from identification. Many confuse anonymity with privacy. Think of a donation event where donors identities are announced but their donations are not, this is privacy. When the donors identities are not announced it is anonymity. If a cryptocurrency doesn't provide anonymity, then it provides no user protection. Anonymity is the most important attribute because user protection comes first. If a cryptocurrency provides all the following characteristics but fails to provide anonymity then it will miss a huge market of privacy oriented people.
2. Decentralization
A service is decentralized when no single authority has full control. This is second on the list because decentralization protects the service. A single centralized authority, such as a bank, has full control over the services. If not regulated, that authority may alter the services in its favor by taking advantage of the users. A centralized authority may also deny users from using services. Decentralization provides the freedom for every individual to use the service regardless. A service is decentralized when the operations are being run from multiple sources, or in case of cryptocurrency, confirmations by multiple individuals running the same service, this is how the service protects itself.
3. Privacy
Privacy is protection of information. The public is being targeted by their habits and preferences. This is mostly related to advertisements, but who knows how will it escalates in the future, controversial theories are endless. It is difficult to change some information such as your name and your address, but some things are impossible to change, such as your date of birth, your blood type or your DNA. Privacy should protect your information even from the other trading party, which may collect information about you such as purchase frequency and recurrent purchases, among other things.
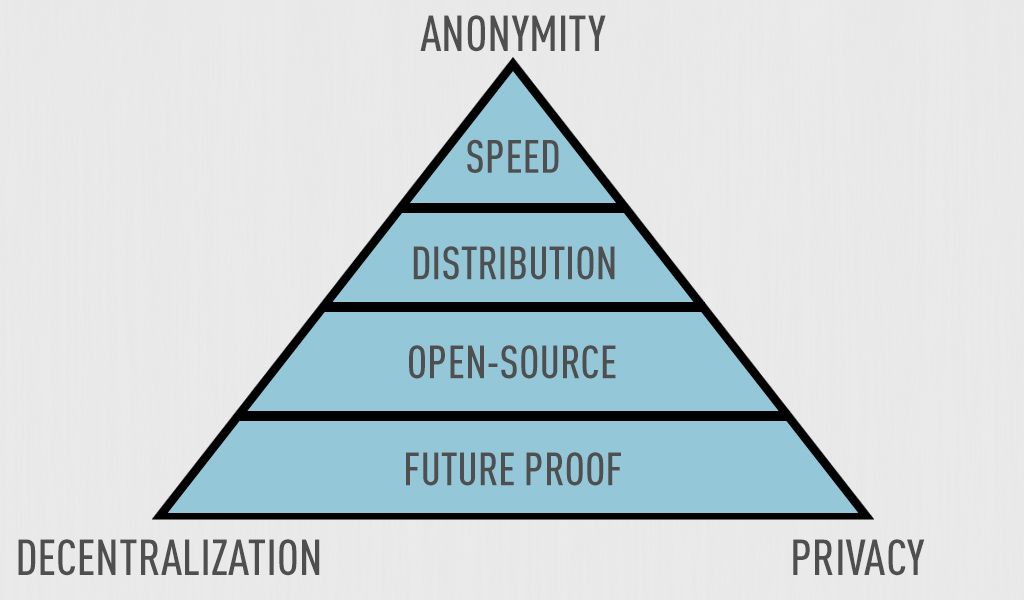
Anonymity, privacy and decentralization are the most important attributes in any cryptocurrency foundation. Protection of identity, services and data should always be a priority. There is no excuse to trade any of them for something else. Any cryptocurrency missing one of these attributes is not expected remain relevant in the future. What comes after these attributes are characteristics that make a cryptocurrency even more relevant and successful.
4. Speed/Fees
It's how fast can a trade be processed. Having speedy transactions is more appealing to the public but it shouldn't be at the expense of the previous attributes, as many traders are willing to trade speed for anonymity. Traders will definitely be looking for a cryptocurrency with fast transactions and minimum fees.
5. Open-Source
Open-source is the availability of the code to the public. This may not seem important but it actually is, especially if you want to know what kind of information is being collected from you and how is it being processed. Open-source code can be inspected by anyone, which is a blessing and a disaster. Anyone can inspect the code and depending on their intent, if a vulnerability is found within the code, it may be announced publicly, or it may be used against all the users of the service. This is why hiring an independent auditing experts is always recommended. However, not everyone is looking to do harm, some may report the vulnerability to the developers so they can fix it before it’s announced or used publicly.
On the other hand, closed-source code is much worse, as it is owned by the author and isn't available to the public. It is difficult to find what data is being collected and how is the data being processed. If unregulated, the owner may use their position of authority and alter the code to run in their favor, without the knowledge of the users. As closed-source code is audited only by the author, so the chance of finding a vulnerability is slimmer, and when a vulnerability is found, it may be too late as we are seeing many cases lately.
6. Distribution
There are three types of cryptocurrency coin distributions. Mining, Initial Coin Offering (ICO) and Airdrop. Mining usually favors whoever can get the fastest mining hardware (GPUs or ASICs). ICO is easy money for the developers and favors investors who plunge to take the risk. Worst case, it may be a scam. Most ICO developers don’t announce what percentage of coins they are holding and may be tempted to dump when the price is alluring. Airdrop is taking over the world of cryptocurrency, as it requires transparency and promise fair distribution of coins. The public can support the projects they feel will become successful and in turn receive a percentage of the airdropped coins.
7. Future Proof
Future proofing depends on the developers of the cryptocurrency. It is how far the developers are willing to go, to support and sustain their cryptocurrency. Developers should be ready to deal with any challenge, whether it is an urgent update or a hard fork. The public can sense the determination of the development team, which increases the public confidence in the project. On a side note, security isn't relevant here because there is no such thing as a secure code. What is secure today may not be secure tomorrow. Therefore, developers must be prepared to deal with any potential security issue.
Conclusion
It would be inappropriate to leave you without a recommendation. Is there a cryptocurrency that covers all these attributes? Yes, there is... DeepOnion strikes each and every one of these attributes and characteristics at the bull's eye. DeepOnion integrates Tor for anonymity with OBFS4 bridges and Meek to bypass censorship. DeepOnion transactions are private with DeepSend at a very low fee. DeepOnion has the fastest transaction time compared to other privacy cryptocurrencies, at 48 seconds per block. DeepOnion is decentralized, open-source and 80% of the coins are obtainable by the public (Airdrop, PoS, PoW). The remaining 20% is reserved for the development and promotions. Finally, DeepOnion has a very active team of developers. They achieved tremendous milestones in a very short timeframe.

DeepOnion is cryptocurrency done right, the project is shaping out to become the standard platform for future transactions. DeepVault is already implemented, VoteCentral will give the community a voice to steer the development of DeepOnion. WooCommerce and a huge campaign will follow soon. More exchanges are accepting DeepOnion, and to top it all, DeepOnion has a very active and kind community. DeepOnion is truly worthy of being called "The Ultimate Cryptocurrency".