The Crypto-Lifestyle: Encrypt files with gpg
Even after using Linux for years...
I keep finding out more great things come with it by default. This post will be a short demo on how to encrypt files with the gpg encryption utility that comes with most distributions of Linux (you don't have to install it, as it's already there). You can install gpg on Windows... but for this article I'll be focusing on using it on Linux.
gpg stands for GNU Privacy Guard
Arguing that you don't care about the right to privacy because you have nothing to hide is no different from saying you don't care about free speech because you have nothing to say. – Edward Snowden
Create the file you'll encrypt
If you already have the file, then you can skip this step. But I'd like to show it for Linux beginners. There are lots of text editors, but for this I'll be using gedit which comes with Ubuntu, Zorin OS and several other versions of Linux.
In the terminal, type gedit file-to-encrypt.txt but name the file what you'd like instead of my demo filename.

After typing this, press Enter. The gedit text editor will open. Type or paste in what you'd like to encrypt:
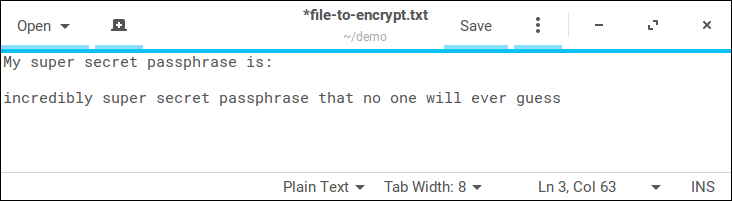
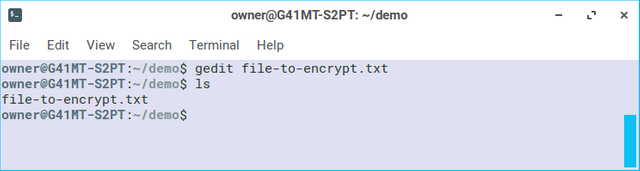
Save the file and close the gedit window. Back in the terminal, the ls command will "list" or show the files in the current folder. In this case, it's just our single text file.
Now that you know the file is there and it contains the text you want to securely save, we will use gpg to encrypt the file. Use gpg -c followed by the filename.
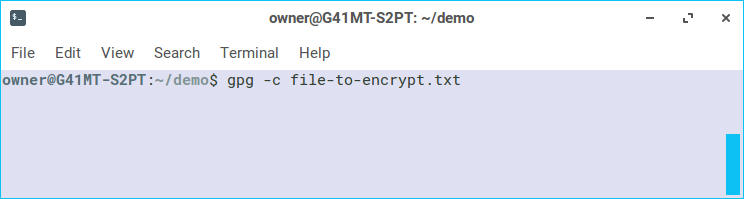
Once you press enter, gpg will guide you through creating an encryption passphrase.
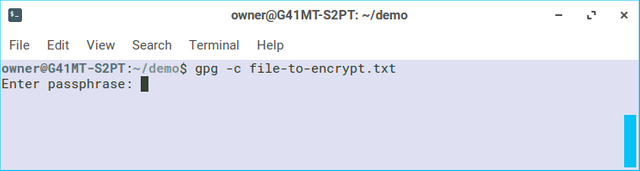
When you enter the passphrase, the terminal will not show your typing. This is for security so no one could see what it is or how long it is. After you enter it once, gpg will ask you to enter the passphrase again. After that, gpg will exit and will have created a new file with the data of the original file, but encrypted with your passphrase.
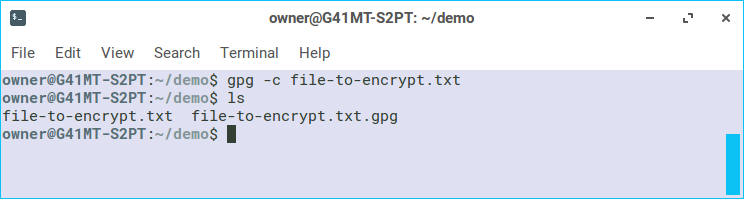
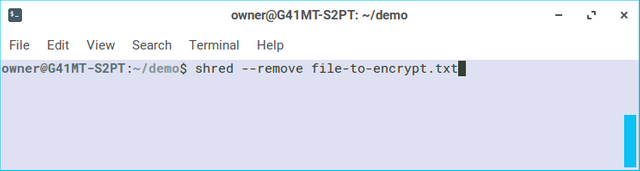
Now when we run ls there are two files. The original file and another file with the added ".gpg" extension. We can use the shred command with the --remove option to completely scramble and destroy the original file (if you'd like, this is optional as it is not necessary for all use cases).
Now only the encrypted file is left. You can just keep in on your computer. You could send it to someone in a message or email and give them the decryption passphrase in person or with another communication channel. You could put the encrypted file on a USB flash drive and store it some where safe and then later decrypt it if needed.
Decrypting the file
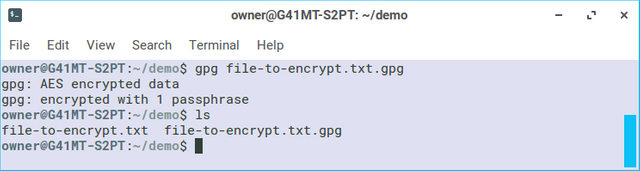
To decrypt the file, just use the gpg command without the -c option. Like this:

Once the correct passphrase has been entered, gpg will decrypt the file. You'll see that there are two files again, as gpg left the encrypted file and created a new file with the decrypted data.
To sum it up:
Until recently, I didn't know about the gpg or shred commands that were there on Linux all along. I'm glad I know about them now and I've already used them to put my Steemit keys on a USB drive. That way, if the drive ever gets in the hands of someone else they wouldn't be able to read my files.
The thing is... you have to remember your encryption passphrase. If you don't, your data is lost to you. You can't get it back. Make sure you commit your passphrase to memory or have some reliable way of storing it.
Now, go. Encrypt your data. Keep it secret. Keep it safe.
I wish steemit had favorites or bookmark or playlist. I need to put this one there....
I have to(plan to ) setup linux first. But stuff like this are good to know!!
So.....if you have concerns of someone trying hack into your stuff......encrypt a crap ton of unimportant stuff and store on same computer or USB. MIX THEM ALL AROUND your real/important file. If gov or hackers ever come making trouble, u just 10tupled their work load. And maybe after 5 dummy files they could even giveup.
Just make sure u have easy way to id the good stuff from your dummies.
I've also been thinking about how to keep track of the Steemit posts I'd like to go back to or reference. Some kind of bookmark manager or wiki may work well for this. Let me know if you find a solution that works well for you.
Thanks, I will!
I just use folders in my browser's bookmark menu. One folder for my favorite writers, a "read later" folder, and a "keep for reference folder."
Hey @matthewdavid! GPG really is great, isn't it? It's even more fun when you use a device like a Yubikey, that stores your private key directly in hardware, where it is (almost) completely safe from being hacked and stolen. In case you are interested in how to use a Yubikey, read this tutorial I wrote a few days ago. Once you have set it up, you can also use the device for SSH login, to sign git commits, and whatever else you can think of. It is also a U2F (universal 2nd factor) device.
Thanks. I have heard of Yubikey, but haven't used it yet. I'll check out your tutorial. Looks like you write quite a bit about security and encryption. Good stuff!
I'm glad you like my content. You should definitely check out Yubikeys, sooner rather than later. If you (or anyone else for that matter) have specific questions concerning security/technology related stuff, feel free to send me a memo. I will try to give you as good an explanation as I can.
In case you don't know how to send a memo (as I did for quite some time): In your Steemit wallet, open the SBD drop-down menu and select "Transfer". Enter the handle of the person you want to send a direct message, and use 0.001 SBD (the minimum allowed by the system) as amount. Fill in the text you want to send. Done. Not completely free, but almost.
Thanks for your reply. I am interested in tech and security. Also thanks for the mSBD and demo-memo message. I appreciate it.
I presented on gpg at a local tech meetup this evening. The talk went well.
What an elegant little program. I didn't know about it either. There are so many great terminal programs baked right in!
K Mandla hasn't written in years, but his blog is still up. It's full of reviews of terminal programs which he would run on old hardware. He introduced me to elinks, for example, which is a text-only web browser that runs directly in the terminal!
The K Mandla blog looked great. I also am fine with using "older" hardware, but not quite as old as he wrote about. My favorite is the ThinkPad series with Intel i5 second generation processors. I'm typing this on a ThinkPad X220 and the T420 is another favorite. I upgrade them all with SSDs and run Linux for my own use.
I use some terminal commands on a regular basis, but I have plenty more to learn.
X220 Tablet is my everyday machine! I got a sweet docking station for free at the dump.
X220 is a great laptop. We have quite a bit in common, then. We use essentially the same laptop. Do you use the tablet features very often?
I haven't until the last couple days, when I got the urge to doodle a bit with Krita. I'm not really sure why I went for the tablet model, but I will say the matte screen is a lot crisper and brighter than what I've seen of the regular X220.
Only problem is I haven't figured out how to rotate the stylus input to match the screen orientation with Linux, so I've got to hold the thing upside down when I'm drawing. Doesn't really matter if I hold the thing on my lap.
My daughter has a ThinkPad X201 tablet that wasn't working right with the pen when we installed Solus OS. We may try to install Zorin OS on it to see if the tablet and pen work better with that. If I do, I'll probably write a post about it.
Oh - let me know!
I've found a few tutorials for correcting the orientation that
involve saving scripts to particular directories...you know, the usual Linux stuff! For some reason I just haven't been able to make any of them stick.
I look forward to hearing about your results with the X201!
Really good post! It seems odd that many of us get the feeling that we are doing something nefarious if we take steps to protect our data, even though we have nothing to hide. Perhaps its all of the social programming we undergo at the hands of our government and society? Anyway, grateful for the info. And that beard, though!
Great post Matthew.
I just remembered that you can create a pair of keys (a public and a private key) that you can use for this intend. I mean, you encrypt your files with your private key, and then you share your file, and your public key to someone else (or to the world, depending on what you need/want to do), so whenever they receive (or download) the file, they need to use your public key to decode the file and doing this assure the people that received your file that it's integrity hasn't been violated.
Greets!
I haven't tried the public key thing with gpg yet. I'll keep using it and see if I learn more.