REMOTE CRYPTO KEY CUSTODY AND DIGITAL ASSET SECURITY SUITE BY GOLDILOCK

The Russians call it "kompromat": using political information against a person to damage their image or blackmail them.
"Compromising material" is what that composition of words in Russian means and that is used as a tactic against national and foreign public figures.For the intelligence agencies of the United States, a kind of "kompromat" is what is under investigation.The Central Intelligence Agency (CIA) concluded that there was an illegal inference via cyber attacks in this year's presidential election.
The origin? Russia, allegedly with a group of hackers called The Dukes.
The person in charge? Russian President Vladimir Putin, or at least that's what the US government says.
The goal? The presidential campaign of the Democratic Party and its candidate, Hillary Clinton.
The effect? A coup in the campaign of the democrats.
But there is another doubt that, in the absence of the publication of intelligence investigations, it has been known little by little as it reveals part of the plot that the Democratic Party lived this year: how the interference occurred via computer attacks supposedly orchestrated from Moscow.

The email that caused everything
"Stealing information for political or economic purposes is as old as humanity," says Ciaran Martin, the head of the National Cybersecurity Center of the United Kingdom. But the new thing is the way it is being done, and in all of this, the Internet " the opportunity for people to do it on a different scale, "warns Martin to the BBC. The Clinton campaign and the Democratic Party were subject to multiple attacks that caused the theft of information, but one was the most relevant.
Who are The Dukes, the hackers who supposedly intervened in the US elections with support from the Russian government
John Podesta was the head of the campaign for Hillary Clinton, a former adviser to President Barack Obama and part of the White House team. Last March, when the Democratic primary campaign was under way, Podesta received an email alert It was like the one received by anyone who uses the Gmail service and who says in large letters on a red background "Someone has your password."
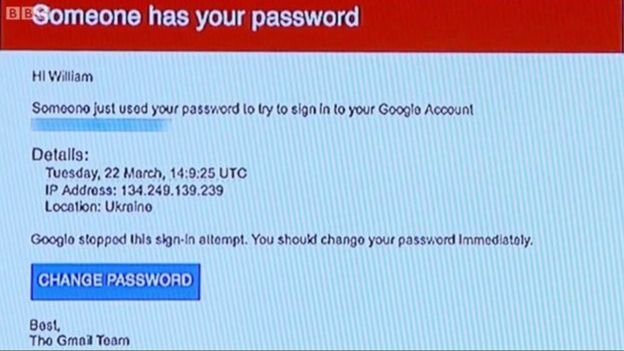
That email is the one that any user of Google mail receives when a suspicious login occurs, from an unusual location or on an unknown device.
To protect the security of the account, ask the user to change the password immediately and thus blocking any new login attempt when the key was stolen.

Case of Facebook:
Facebook Inc's CEO, Mark Zuckerberg, told the US Congress in a written testimony released on Monday that the social network did not do enough to prevent the misuse of users' personal information and apologized.

"Now it is clear that we did not do enough to prevent these tools from being used to harm," he said in testimony released by the US House of Representatives Energy and Commerce Commission.
"We did not have a broad enough vision of our responsibility and that was a big mistake, it was my mistake and I'm sorry, I started Facebook, I direct it and I'm responsible for what happens here," he added.
He also affirmed that Facebook's main investments in security "will significantly impact our profitability from now on"

From these two previous stories is a great learning, THE INFORMATION IS SO IMPORTANT THAT A COMPANY CAN PUT IN RISK YOUR FUTURE AND UP TO CHOOSE A PRESIDENT!
birth of Godiblock
Through the technology "air gap" remotely activated to store confidential information, including critical digital assets and private keys of cryptocurrencies Godiblock was born in the blockchain of NEO and thus be able to provide a functional ecosystem destined to the safeguard of important information, both wallets of cryptocurrencies as personal and business data
Godiblock revolutionizes the way data is stored on the Internet by building an ecosystem that protects cryptocurrencies and digital assets of people and institutions. Goldilock Security Suite, with an operating platform launched in the second quarter of 2018 that offers remote physical disconnection of Internet data, takes advantage of multi-factor authentication, biometrics, triggers regressive technology and cryptography to free investors from the burden of protecting purses, because our physically segregated platform takes care of that.
Godiblock also creates creates Housing or physical cameras in data centers destined to the protection of data that can be leased by institutions that need direct control over their servers.
The applications of Godiblock technology to blockchain technology are practically endless, since the custody of private keys is essential for all decentralized transactions. In traditional Internet environments, this important physical layer of data security will apply to the storage of personal credit information, bank account information, medical records and other vulnerable digital assets

THE THREE GOLDEN RULES THAT MAKE GOLDIBLOCK INFALLIBLE
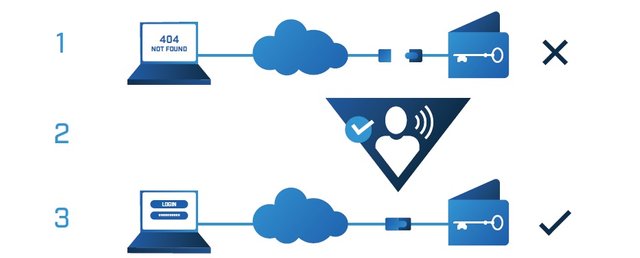
The data is stored in physical hardware that is stored in secure places and disconnected from the network, so if there is no connection there is no information that can be pirated, goldilock will not manipulate this information and it will be compatible with it. the user
the platform will have an always active communication path where the user can identify himself by means of innovative methods to validate his identity, this mechanism is free of traceable IP
The user can securely access their wallet through an encrypted connection with a URL destined for it and access the credentials, once the user finishes his operation, the data is disconnected from the network and stored again cold

Penyimpanan Data da Keamanan Aset Digital
Clinical, financial and legal records are essential for the personal and legal well-being of the client. Goldilock offers an ideal form of storage with accessibility to the letter for this type of information. Goldilock, in partnership with banks, credit agencies, insurance companies, document management operators and data storage operators, will offer solutions for these markets.
Godiblock purse for cryptocurrencies
Goldilock's central development team will develop Goldilock's purse with the initial objective of storing NEO, GAS and NEP-5 tokens and of transacting with these cryptoactives, which will make NEO the safest cryptocurrency in the market.
The Goldilock wallet will run in an authenticated web browser through SSL. Other functions will be the following:
The keys of each purse will be in a unique hardware device, segmented and encrypted disconnected from the Internet.
The wallet will be connected by means of a command without IP and a verification by PIN or voice through the telephone network (RTC) without IP.
After closing the wallet, the single hardware wallet device will be disconnected from the Internet.
Each purse will be assigned an exclusive personal URL.
Each signed transaction will require authentication in two phases.

GOLDIBLOCK CAN BE COUPLED WITH OTHER PLATFORMS: Goldilock API Services
![]()
An API represents the ability to communicate between software components. This is the set of calls to certain libraries that offer access to certain services from the processes and represents a method to achieve abstraction in the programming, generally (although not necessarily) between the levels or lower layers and the superiors of the software. One of the main purposes of an API is to provide a set of functions of general use, for example, to draw windows or icons on the screen. In this way, programmers benefit from the advantages of the API by using its functionality, avoiding the work of programming everything from the beginning. The APIs are also abstract: the software that provides a certain API is usually called the implementation of that API.
Applying the use of API Goldilock aims to create tools that help other platforms to use their technology and thus be able to count on the service they provide at the security level, a platform that offers cryptocurrency purses can use Goldilock services to safeguard their data in a fast way through the use of these APIs, so the programming of the platform is faster and more reliable

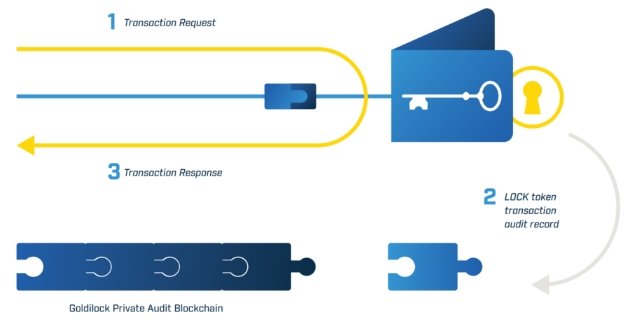
TOKEN LOCK
The LOCK token allows Goldilock to provide users with a record of their activity on the nodes, in addition to keeping the user-owned data encrypted and out of reach even of the Goldilock team. In addition, LOCK will be the accepted method for payment of subscriptions of each user in Goldilock Security Suite. The intention is to initially support NEO, GAS and the NEP-5 tokens in an effort to convert the NEO cryptocurrency into the safest available today. This step will precede the expansion of the platform with the inclusion of other popular and alternative cryptocurrencies.
Goldilock will carry out a sale of tokens in the second quarter of 2018. They have an estimated sale of 670 million tokens to the public out of a total of 1,000 million. open more details about the sale during the second quarter of 2018.
In the second quarter of 2018, they will implement a functional minimum functional product of the Goldilock purse for cryptocurrencies and users will be able to use the technology after registering and correctly purchasing the Lock token.

GOLDIBLOCK FOR ALL LIKES
Case of use:
Business:
A sports company that runs a very famous club in Europe is collecting information from the minor leagues, now, it has invested millions of euros in its signings and it has always been a success, that until the last season where there was a dispute for a player Latin America they had in their sights, is from a local club in a small town in Venezuela, the player has not played professionally in his country, but now another club is also in dispute for their services and this raises the cost of the player , after a while the information that the club's data was cheated and the thousands of dollars in research that he invested in information of his possible signings was worth nothing, on the contrary now his rivals know that players are of high potential and they dispute signings that otherwise would be of low commercial value
Companies like these need to safeguard their information in a secure way, this information is worth millions of dollars, it can even compromise the future of a club or company, so investing in the security of Goldilock is very profitable, apart from not spending on hardware and in personnel that install and trust for its management, that value would be saved, as well as the energy value, maintenance, and most importantly, with Goldilock the security is guaranteed
Personal:
Pablo born with an illness and his whole life has been visiting specialists, he has been a very strong person of spirit, lives to the fullest and values his time, already has a medical routine that includes trips abroad every 3 months for his checks and so on. keep your disease under control
Pablo is tired of always walking with big notebooks where he accumulates his exams, takes thousands of dollars in important tests for him and his treating doctors, as they see specialists from different branches and in different clinics, and Pablo has mislaid several of these folders wasting time and money in recovering exams apart from going through the same experiences again
After investigating Pablo with Goldilock, Pablo knows that he can save his data so that he will not lose any more, also when he travels, Pablo will not carry more heavy folders, only with an internet connection he will be able to count on his documents and so on. your specialists can have the data they need

THE TRUTH ABOUT THE TOPIC !!
Cold storage is the best option, but you have to find the way that the user can have data availability, time is important and nobody is to lose it, apart now the money is data with the world of cryptocurrencies and wallets digital, then we want to have our assets at any time and without having to be at risk
Achieving cold storage with an available network of user verification fast and effective Goldilock is placed at the forefront of the digital security market in this era, blockchain technology needs to safeguard information, people are investing their assets in these platforms and must have total security
Thousands of companies invest millions of dollars in infrastructure, personnel and energy for the security of their data, also at some point they are violated in a certain way, in some cases caused by the fall of important companies causing incalculable losses, with a lower investment. large companies may have a higher level of security, the real solution to the security of your data
###The information is so important that filtering data can even influence the reins that take a whole country like the United States!

For more information watch this short feature intro:

More Information & Resources:
Goldilock Website
Goldilock WhitePaper
Goldilock Tokenomics
Goldilock Telegram
Goldilock Discord
Goldilock Linkedin
Goldilock Facebook
Goldilock Twitter
Goldilock Reddit
Goldilock Github

article written by @loganjose for the writing contest of @originalworks
contest link here
goldilock2018
)


This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!