TAKE ADVANTAGE OF PROCESSING OF CPU TO MINAR MONERO YET WITH THE CLOSED BROWSER
The year 2017 was full of news about applications that mine cryptocurrencies with the processing power of CPUs without the authorization of users. In this article we will explore a new modality in which these mining malwares are still running, even if the browser has been closed.
A computer team demonstrated that the virulent mining of cryptocurrencies by means of the navigator has evolved and a modality has been developed so that the miner continues to take advantage of the processing power of others even when the user has closed all the visible windows.
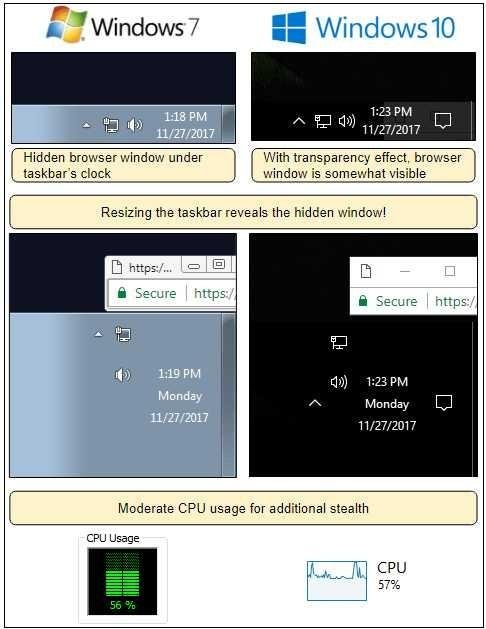
It happens that, with this mode, the browser is not completely closed and a small tab is hidden from view. When this is the case, 50% of the CPU capacity is still used by a process linked to the browser.
This service circumvents the ad blockers, since it is hidden under a modality called "pop-under" that is hidden in the lower right corner, just below the clock. Also, it has been resized to have a moderate impact on CPU processing and is more difficult to identify, as opposed to other cases in which the miner uses 70%.
This new mining malware is hidden in the lower right corner of the taskbar. Source: Malwarebytes Labs
One way to counteract this breakthrough is to close all web browser processes from the Windows Task Manager and verify that there is no irregular behavior of the browser icon in the taskbar. You can also use antivirus tools to block it.
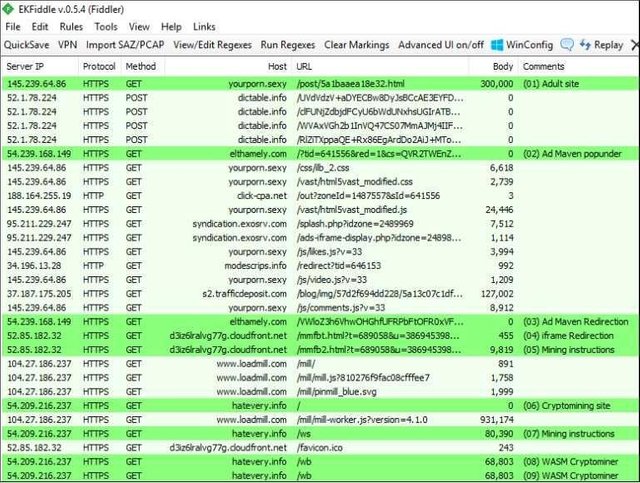
CoinHive is a Java add-on that is integrated into a web page and allows its owner to monetize it without integrating ads in it. The problem of this practice is presented to the visitors of the websites that surf the site unnoticed from the theft of processing power. This is an infection discovered by the Malwarebytes Labs team on an adult video site.
Mining malware seen in the task manager.
Once the user opens the page, a percentage of their CPU is hijacked by CoinHive and used to undermine the Monero cryptocurrency. Most of the time the user is a victim of this without knowing it, because, although CoinHive service conditions specify that customers must inform their users, most site owners pass this warning over.
The controversy surrounding CoinHive has only three months. At the beginning of October, users turned on the alarms thanks to a report in which it was indicated that some pornographic pages were using the mining tool without making any notification. Later, in the same month, the Coinhive service was hacked and thousands of websites -service customers- were put under mine for a stranger for about six hours.
After this, in the month of November, it was announced that this service can be used for a good cause, as it is to help modern slaves in Pakistan to obtain their freedom. Inherently, CoinHive can be a good tool to replace the ads and security threats they represent, as long as the user knows that a miner is running in their browser.
@OriginalWorks
The @OriginalWorks bot has determined this post by @fjgb to be original material and upvoted it!
To call @OriginalWorks, simply reply to any post with @originalworks or !originalworks in your message!
Hola amigo, muy interesante artículo. Gracias por alertarnos la verdad es que no había oído hablar de esto asta ahora. Excelente.