The advent of Cryptography (Part 1)
Hello Fellow Steemians...
This is my first article on Steemit and I hope you guys like it.
In today's day and age where crypto currency and Block-chain are booming like anything and everyone wants to get onto the Crypto Bandwagon, I thought why not explore the basics of Cryptography.
THE ADVENT OF CRYPTOGRAPHY:
The use of cryptography dates back to 1900 BC when an inscription was found to be carved around in the main chamber of the tomb of the nobleman Khnumhotep II, in Egypt. The scribe used some unusual hieroglyphic symbols here and there in place of more ordinary ones. The purpose was not to hide the message but perhaps to change its form in a way which would make it appear dignified
( )
)
WHAT IS CRYPTOGRAPHY: Cryptography is basically the science of converting a Plain-text (meaningful information) to a Cipher-text ( non-meaningful information). For example if “Computer” is converted to “#$25%67” than “computer” is Plain-text and “#$25%67” is cipher-text.
WHAT IS CRYPTO-ANALYSIS: Crypto-analysis is the reverse of Cryptography. It is the process of converting cipher-text (“#$25%67”) to Plain-text (“Computer”). There are two main methods of performing Crypto-analysis. One is Brute Force method. Brute Force is basically a non-intelligent way in which all possible combinations are tried to calculate the plain text. The other method is to find the weakness in the process of encryption and exploit it. The weakness can be in the encryption algorithm itself or can also be in the software or hardware implementation of the algorithm.
Encryption: The process of converting a plain-text into cipher text using mathematical and computational algorithms is called Encryption. It is a reversible process. Almost all of the encryption mechanisms take a plain-text message and a “ Key”. The key can be a string of numbers, alphabets, a name or anything to that sort. The key is then applied to the plain-text message using an encryption algorithm and the result is a cipher text.
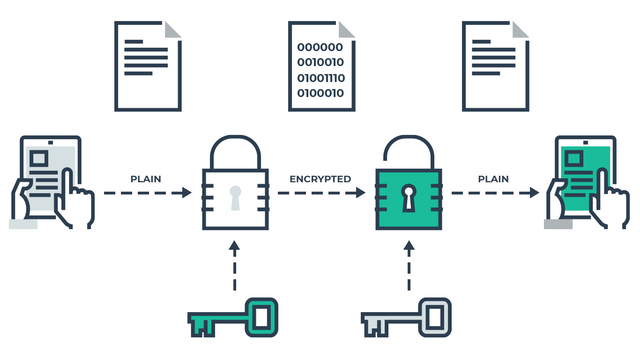
Decryption : It is the reverse of encryption where cipher text is converted to plaintext using a “Key”. The cipher text and Key are applied to the decryption algorithm and the result is a plain text.
HISTORY OF CRYPTOGRAPHY
WHY WAS THERE A NEED OF CRYPTOGRAPHY : Secrecy has always been an attribute of human nature and when a group of individuals want to conceal their conversations and movement, the need for secrecy profoundly increases. In order to achieve the goal of disseminating information in a secure way, in ancient civilization people started to use techniques that will make their message non-understandable to any third party. With time these techniques started becoming more sophisticated and developed into a complete science Known as “Cryptography”.
ANCIENT METHODS : Before 19th century and the rise of computers, Cryptography contained techniques such as manipulating the alphabets of the language in a way to conceal their meaning. These techniques fall into below two categories:
TRANSPOSITION: In this techniques letters in the message are rearranged to provide secrecy. For example “Computer” can be rearranged to form “ Retupmoc”, “Ocmputer”,”Ertupmco” etc. As there are 8 alphabets in “Computer”, there are 2^8 i.e 256 possible transpositions. If you increase the size of the message to 80 letters however, the number of permutations grow exponentially and becomes very difficult to decrypt.
One of the first cryptographic devices using transposition dates back to the fifth century and was named the Spartan Scytale. The Scytale worked as follows -- a fabric was wrapped around a staff and a message was written on the cloth. Once unwound, the cloth appreared to have a meaningless scamble of letters. The sender and the receiver would both have matching sized staffs to secure mutual communications.
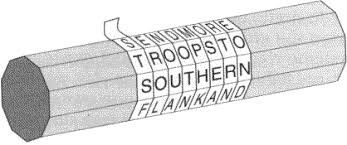
Rail Fence Transposition
Rail Fence Transposition is a simple transposition technique in which alternate letters are written together and then you start again from the beginning. A simple way to achieve this is to write down the words in two rows as explained below
.png)
SUBSTITUTION: In this technique the alphabets or letters of the plain text are replaced with letters, symbols or numbers. For example in English if we replace every alphabet with its number like A is 1 B is 2, than the plaint text “Computer” becomes 31513162120218.
More in Part 2 ......
Congratulations @dawaj! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
Click here to view your Board
If you no longer want to receive notifications, reply to this comment with the word
STOP@dawaj, a very good attempt for a first post. Perhaps you could also give an introduction of yourself in your next post.
I agree with @devann this a very good first post and astutely you have realised crypto posts here are generally well received as its an informed tech savvy crowd here. Anyway, welcome and all the best to you and your steem ventures.
Posted using Partiko Android
Hello @dawaj! This is a friendly reminder that you have 3000 Partiko Points unclaimed in your Partiko account!
Partiko is a fast and beautiful mobile app for Steem, and it’s the most popular Steem mobile app out there! Download Partiko using the link below and login using SteemConnect to claim your 3000 Partiko points! You can easily convert them into Steem token!
https://partiko.app/referral/partiko
Congratulations @dawaj! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!