Fungible Assets vs Collectables - Part 2: Token creation and issuance
[NTF] [ÐApps] [Sidechains] [Lightning Network] [Smart Contracts] [ERC-721] [Rare Pepes] [Art] [Counterparty]
The subject of the second part of the series is to elaborate the different types of token creation and which features can be applied to. Part 1 pointed out why NFTs will go viral in 2018.
TABLE OF CONTENT
· INTRO Non-fungible tokens
· 1. Types of token creation
· 1.1 Coloured coins
· 1.2. Smart Contracts
· 1.3. Sidechains
· 1.4. Lightning Network
· 1.5. Softforks / Hardforks
· 2. Types of token features
· PREVIEW Fungible Assets vs Collectables - Part 3
INTRO: The Non-fungible tokens revolution has begun
NFT is real! The following hands-on advice is for all blockchain artists, FOMO investors and collectables supporters.

ASSET NAME: LORDKEK
AMOUNT ISSUED: 10
ESTIMATE VALUE: $2.5M
The Rare Pepe ecosystem is literally a NFT-masterpiece. A lot of artists created their own Pepe using the smart contract functionality of the counterparty protocol.
The unit of account is PepeCash. You can use the Rare Pepe Wallet to buy and collect the trading cards. Trades are fulfilled via XCP or PEPECASH and a little portion of BTC as fuel (like Gas for Ethereum).
PepeCash is meant to be the currency of the Pepesphere
Ironically, the most valuable card is a ‘fungible’ token (i.e. divisible). Hence, one of the cards is already broken into parts! The artist made a mistake during the token creation. He forgot to uncheck the ‘make divisible’ box. In total, there are currently 8 non-broken LORDKEKS’s in circulation because one of the owners lost the private key of the 10th card.
Counterparty is the easiest tool for token creation as there are no programming skills needed.
The service offers several custom fields such as Token Name, Quantity and Make divisible.
The creation of a new custom Counterparty token costs 0.5 XCP spam fee, and a BTC mining fee. The actual transaction is a little portion of BTC (DUST). A more technical explanation can be found here: P2SH data encoding.
Source: https://github.com/F483/counterparty-documentation/blob/master/Basics/FAQ.md
1. Types of token creation
Due to the lack of fungibility it is possible to use existing blockchains to track ownership of distinct tokens. Coloured coins (e.g. RMC) and meta coins (e.g. XCP, PEPECASH) are based on second-layer protocols. For instance, it allows you to build a customized ledger on top of the Bitcoin ledger.
If the existing token projects not suit the task you are looking for considering to start a new blockchain isn’t a bad idea in general. Sidechains (e.g. within the Lisk framework) are their own blockchains that are pegged into their main blockchain.
Bitcoin’s network software is open source, so it can be duplicated and modified. Best example is Litecoin. Their developers forked the Bitcoin source code and added new features like an alternate algorithm (script) and shorter block times.
Most altcoins are ERC-20 tokens (e.g. EOS) using Ethereum smart contracts. Ethereum was created because there wasn’t an easy way to build smart contracts into the Bitcoin protocol without major changes (hard fork). The first approach of the early Ethereum projects was ironically a coloured coin. But in 2014, they came up with a new contract-orientated programming language called Solidity which became the most common language for smart contracts. There are already several tutorials, so what you need is just a portion of Ether and copy-and-pasting some lines of code in Solidity. Before going life, testing it on the Rinkeby.io testnet and ask some developer to proofread and check all functions should be mandatory. You can also announce a bounty for bugfixes. Be careful with that steps: Once the contract is published, there is no drawback.
There are thousands of ways to create a new token. The main technical solutions are:
- create a coloured coin,
- create a meta coin,
- create a smart contract (that updates information of a distributed ledger),
- build a sidechain,
- fork an existing blockchain,
- fork the source code to build an entirely new blockchain,
- or start an entirely new token ecosystem from scratch.
1.1. Coloured coin + middleware layer = meta coin
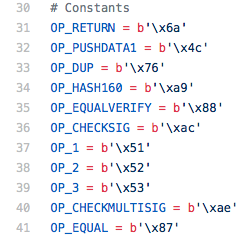
Coloured coins can be tied into Bitcoins' blockchain whilst adding new features such as digital assets, smart contracts or atomic swaps. It is also known as on-chain coins. Besides of just colouring Bitcoin, it is possible to create meta coins that are stored inside the Bitcoin, Monacoin and Bitcoin Cash blockchain using a middleware layer. There were software forks of the counterparty Github repo for Litecoin and Dogecoin, but development got stuck in 2015. Technically, most meta coin transactions utilize a data encoding method called OP_RETURN. By doing so, users need to run the Bitcoin client along with the meta coin client software to create and send tokens. Counterparty tokens can be viewed via xchain, several collectable cards via Book of Orbs.
As user issued assets ride on top of a certain blockchain it can be interpreted as a fractional reserve system. Beside of their individual color value it is backed with a fractional portion of the auxiliary blockchain (Bitcoin dust) which has obviously a more objective value.
Proof of ownership through coloured coins is a great way to redefine our monetary ecosystem. Imagine a coloured coin that uses a fractional reserve system using another coloured coin that is pegged to physical values on full reserve like DigixDAO.
Whilst meta coins are a coloured variant of the parenting coin with a middleware layer it needs to be run on dedicated servers or distributed file systems, which verify the transactions.
The native Counterparty project (XCP) is probably the most secure and adopted way for meta coins. There is a basic smart contract-alike functionality to create new assets and make them non-fungible.
BTC to XCP is like TCP/IP to HTTP
Counterparts tokens (XCP) working as fuel and were minted using Proof of Burn. In the burning period, investors could send BTC to a special non-spendable address (1CounterpartyXXXXXXXXXXXXXXXUWLpVr) to verify that they burn some value in exchange for the newly created XCP token. Peter Todd stated that Proof of Burn is probably safer than sidechains:
Now people can argue about the fairness of how Counterparty's token was created, but on a technical level using a token rather than a two-way-peg has the advantage of security: who owns what tokens is defined by the Bitcoin blockchain, and changing that record requires you to 51% attack Bitcoin as a whole.
There are plenty counterparty projects. My personal picks:
Other working meta coin systems are OmniLayer, Coinspark and NXT.
Source: Digital Assets on Public Blockchains - White Paper from Bitfury.com
1.2. Smart contracts
Similar to meta coins, but with more flexible contract features are projects like EOS, NEO and Ethereum. The main advantage is higher flexibility and potentially lower transaction fees. The main disadvantage is that programming skills are needed to write an smart contract. In Part 1 of this series, there is theoretical background about NFT creation through smart contracts. In part 3, there will be some hands-on knowledge for embedding the collectables' meta data into a smart contract.
There are some guides to create and deploy Ethereum smart contracts:
How to create a voting system Part 1, Part 2 and Part 3
How to create a decentralised eBay with IPFS (paid content: 75$)
How to deploy a smart contract on ethereum testnet
How to write your first DApp
NFT library on Github that was build for an ERC-721 token for pseudo-identities
working NFT based on Ethereum smart contracts are about to go wild:
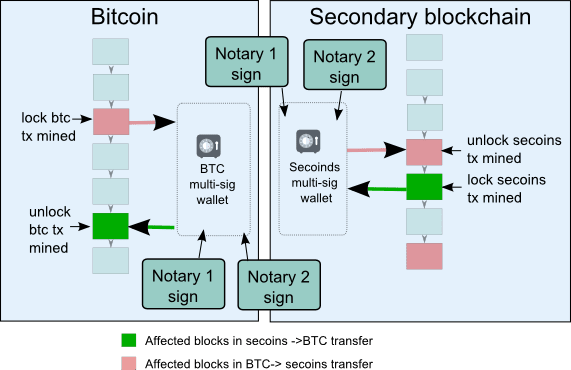
1.3. Sidechains - connecting digital ecosystems using an independent network and a primary blockchain as the underlying currency
A sidechain is just a separate blockchain. It is attached to the main chain / primary blockchain using a two-way peg which allows tokens to be interchangeable and moved across the chain at a fixed deterministic exchange rate.
It works like this: On the main chain, tokens will be sent to an address where they're completely immobilized by custody of an exchange, a multi-sig notary system(i.e. a federation), a voting system, SPV-proofs or a hybrid form of these. Once the immobilization transaction has been confirmed by the custody, a message to the sidechain protocol allows creating a certain amount of tokens on the sidechain. The advantage is that the sidechain protocol can have multiple features like smart contracts or lower transaction fees. Vice versa, after transactions are done on the sidechain, one can immobilize the tokens by sending them to a certain side chain address. Finally, it will be spendable again in the main chain, under the control of whoever last owned them on the sidechain. The lightning network is one of the most advanced sidechain technologies that are currently available.
However, there are some security issues with sidechains that could be distinguished by forking the Bitcoin blockchain:
The ability to use sidechains as an upgrade and experimentation mechanism has been heralded as a key enabler of scalability in the Bitcoin ecosystem; however, the sidechains proposal is incomplete, as it does not provide a protocol that satisfies a natural security definition, i.e., where attacks succeed with only negligible probability, even though several attempts were made. [...]
Our definition fills the gap in terms of security modelling and design that existed in previous proposals, e.g., the notion of cumulative “Dynamic Member Multisignature”
However, colouring coins is probably the method with the smallest effort because there is no need for a custom modification of the core software and no additional risk of a failing custody system.
Source: Non-Interactive Proofs of Proof-of-Work, White Paper.
There are numerable projects trying to enable the technology but so far no one had succeeded implementation to the Bitcoin main net:
- A Turing-complete virtual machine with hybrid custody is offered by Rootstock that is two-way pegged to Bitcoin. It is not working so far because it needs a soft-fork of Bitcoin for enabling an opcode that allows a decentralized communication with the sidechain or drivechain protocol.
- A promising development is The Elements project that can be operated on the Bitcoin testnet.
- Lisk is building a Delegated PoS system for the development of Dapps using sidechains.
When the role of the custodian is given to the miners it is called drivechain (i.e. a threshold voting system). Miners mark blocks with small data tags (a special reverse peg opcode) to publish that they acknowledge the immobility of the secondary blockchains' funds. If the number of acknowledging tags is over a pre-defined threshold the funds of the primary blockchain will be unlocked.
Even if secure sidechaining is possible, the main disadvantage is that there is no easy transfer functionality between several sidechains. With inter-chain transfers, there may occur two or more transactions instead of one because the sidechain funds need to be unlocked in the main chain to get locked into another sidechain again. Inter-chain transfers are extremely necessary for a lot of reasons like price discovery and liquidity. If the transaction fee of the main chain is too high, there is an undesirable barrier between multiple sidechains.
High fees of the main blockchain also causes problems with colored coins.
Most coloured and meta coins’ technology is using the Bitcoin protocol as its main layer. We saw that Bitcoin’s transaction fees are too high for micro payments. That makes it hard for coloured coins to be issued and sent within mainstream applications.
A popular proposal for solving the above problem is the implementation of the lightning network.
1.4. The Lightning Network: Off-chain micro payment network
Scalability is one of the key improvements for mainstream applications and the proper use of inter-chain transactions, atomic swaps and digital asset creation. With the creation of Bitcoin, the main goal was to design an ecosystem that works as much decentralized as possible. Therefore, the block size was adjusted per natural technological growth of storage capacities. 1 MB seemed to be a good trade-off between transaction speed and storage costs of the distributed ledger. In contrast to Bitcoin Cash, the Bitcoin core developers wanted a solution without bigger blocks but with second-layer multi signature contracts. This functionality was not supported in the Bitcoin protocol. There was an issue with calculation of transaction IDs. Second-layer protocols like the LN rely on the use of unconfirmed transaction by using a complex system of cryptographic signatures.
Hence, if someone changes the signature of a Bitcoin transaction (i.e. the authorization of a payment) the transaction ID changes. As the new transaction ID with the alternated signature would be invalid this is called the malleability bug.
The Bitcoin Lightning Network was introduced in the conference Scaling Bitcoin Montreal (Mid 2015). After discussions how to integrate the proposal as a soft fork it was finally detailed in a white paper by January 2016.
An initial channel Funding Transaction is created whereby one or both channel counterparties fund the inputs of this transaction. Both parties create the inputs and outputs for this transaction but do not sign the transaction.
After reaching out the broader Bitcoin industry to support the proposal BIP-141 and others, the consensus layer Segregated Witness (SegWit) has been activated via soft fork at block # 481,824 which was mined at 24 August, 2017.
The software upgrade enables off-chain solutions like the lightning network (LN) by solving the malleability issue.
Bitfinex and Coinbase, two major exchanges - already have implemented SegWit. However, this upgrade is not the lighting network itself - Just the compatibility for SegWit addresses has been updated.
LN is currently under the development by four independent dev teams:
- c-lightning and Lightning Charge, both part of the Elements Project developed by Blockstream
- lit, developed by the MIT Digital Currency Initiative
- The Lightning Network Daemon (lnd) and the corresponding wallet called lightning-app and the 3rd party wallet Zap (both Win/OSX/Linux)
- Éclair (French for Lightning) and the corresponding wallet (Android)
The idea of LN was to create a second layer payment protocol on top of a blockchain. It uses a mesh network of multiple bi-directional single payment channels. There are several steps to execute a payment between two parties:
- To open a payment channel, a smart contract needs to be signed by both parties before the funding transaction is sent out to the network. The channel can be closed manually or automatically, after a predefined nLockTime.
- To conduct a payment, the sender signs another smart contract to verify an off-chain transaction. The nLockTime needs to be before the time the initialized smart contract will be settled.
- The payment channel will be closed, as soon as the initial smart contract is over (nLockTime=present) or one of the both parties closes the channel manually by broadcasting a commitment.
In terms of scaling, the more connections are opened, the less on-chain capacities will be needed. The key innovation is set of multiple hashed timelocked contracts (HTLC).
Once there is a mesh network, the sender can process a payment by using multiple open channels that are already opened. In the following example the cost reduction is 25% or more (4 payments but only 3 channels). Instead of an on-chain payment, Alice can use her channel to Bob. Bob’s network finally leads to Dave.
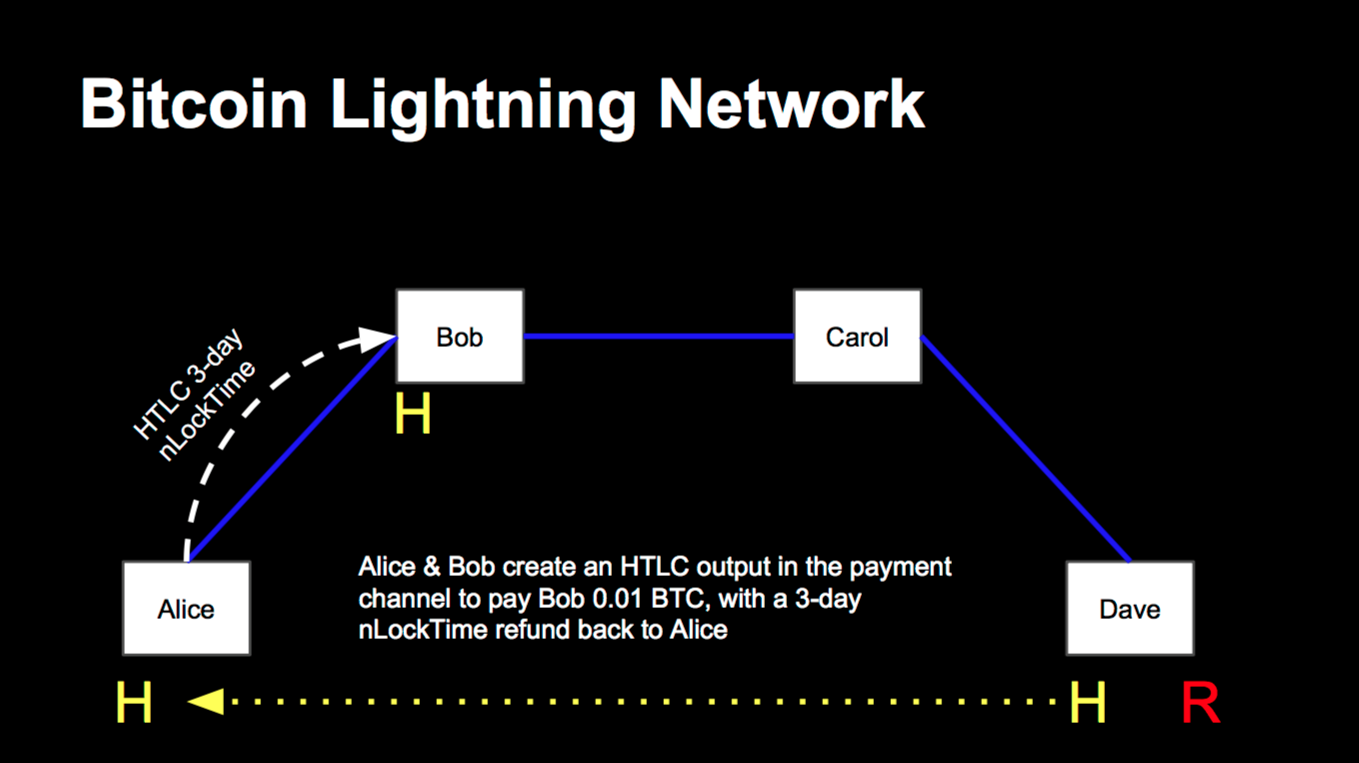
Technically spoken, Dave needs to disclosure the secret preimage R which produces the known cryptographic hash H. The payment is conditional upon knowledge of the secret key. If someone in the network can prove to have the preimage R the recent HTLC contract is obsolete. Dave can receive the payment from Carol after he disclosed R. The same process needs to be fulfilled with Bob and Alice. The chain of custody verifies that only liable channels can receive and forward payments.
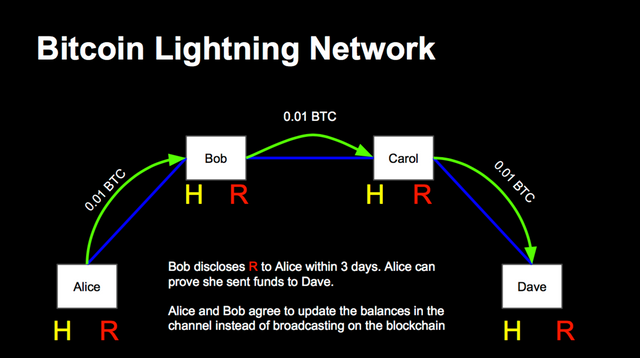
The following example shows how payments can be conducted by unilateral custodial ownership.
To open a single payment channel Alice and Bob sends 0,5 BTC each to a multi signature address where Alice and Bob have access. This initiating transaction happens on the public blockchain. Therefore, the multisig channel has 1.0 BTC funding. The channel is secured by a hashed time lock contract that can be endure for a specific time interval e.g. for 30 days. If something goes wrong Alice and Bob can manually stop ongoing payments by closing the channel; After commitment 1a or 1b is broadcasted, the channel will be closed and the initial funds of 0.5 BTC go back to each party.
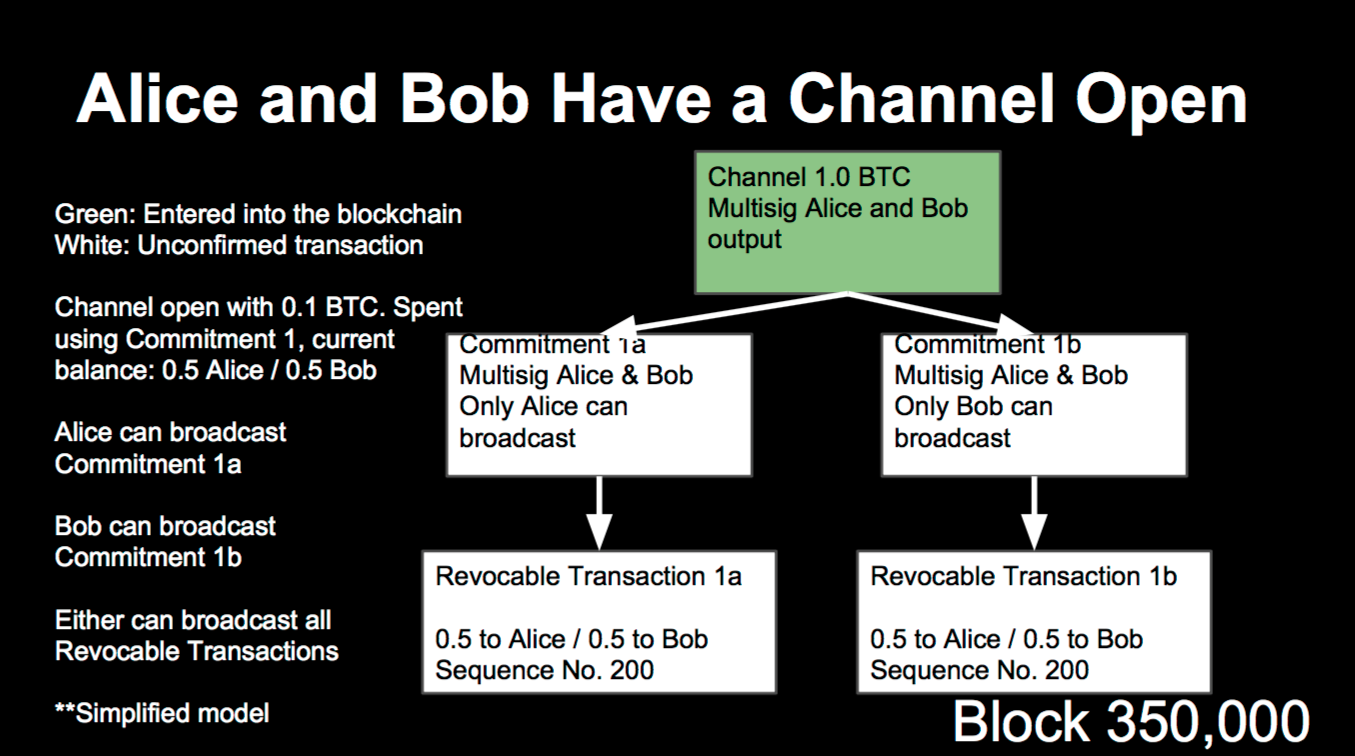
Source: http://super3.org/introduction-to-micropayment-channels/
https://lightning.network/lightning-network-presentation-time-2015-07-06.pdf
1.5 Forking the code, forking the chain or starting from scratch?
Newly developed software using a forked source code cause three scenarios:
the software does not alter the consensus rules: Peers will still agree with the existing network and ledger.
the software alters the consensus rules and recognizes previously mined blocks: it forks the chain.
the software alters the consensus rules and does not recognize previously minded blocks: it creates a new blockchain
Starting from scratch, as it happened with Ethereum, is also a possible way of creating a new blockchain. With sharing blockchain security like merged mining (AuxPoW) and ----blind anchoring (dPow), the risk of a 51%-attack is lower. Blind anchoring, known as delayed proof of work consensus mechanism (dPoW) can resolve the problem of the relatively low global hashing power of altcoin mining. AuxPoW can be activated when using the same algorithm than the dedicated parent blockchain (e.g. SHA265 or Script). The auxiliary blockchains's Merkle root will be added as a bogus transaction at the tip of the parent Merkle tree. By hashing that you will get a Merkle root that has the information of the transactions of both blocks. With this trick, miners can increase their rewards output with the same hashing power and the auxiliary blockchain can be maintained easily. Sidefact: Merged mining may also help to strengthen the security of sidechains. However, merged mining is not safe if less than 50% of parenting mining pools have merged mining activated.
2. Types of token features
In a broader sense, cryptocurrencies are deemed as a unit of value that an organization creates to self-govern its business model and distribute and share the rewards and benefits to all its stakeholders.
These are the most important parameters of a hypothetical token issuance:
- Currency: Issuance of pre-mined newly developed tokens, soft-forked or hard-forked cryptocurrencies
It empowers a frictionless transaction as a fungible payment unit. - Toll: (software) access token
Enables access from a limited user base, needed to run smart contracts or used as a security deposit, a penalty for misbehavior or an anti-spam fee. - Value exchange: Redeemable token for a product, service or membership(waitlist)
- Rights: Digital proof of purchase/ownership, linked to a share of a business
- Function: Distributed Collaborative Organisation (DAOs) or centralized entities
- Revenue: tipping, automated reallocation, security tokens (cashing out dividends)
- Properties: voting rights, non-transferable, locked, divisible, callable, burnable
A token for a token for a token: fractional ownership
A relevant characteristic of money is divisibility. Collectables could also represent divisible values. With smart contracts, you could arrange a setup where you create a second token and divide the rights of ownership of your collectable into parts and share it with somebody. It's impossible to break the collectable into fractional parts but a derived token using a sidechain or a coloured coin. Remember the infamous example of LORDKEK’s divisibility? There may be reasons why it is favorable to enable fractional ownership if the value increases.
Source: SWARM Working Paper, Distributed Networks and the Law
EXCURSUS: Security vs utility token
Both investors and issuing entities need to know if their project is considered as a regulated security token. If your token is linked to a share of a traditional business and it pays dividends it is very likely that SEC will conclude that those tokens were securities and therefore possible violations of U.S. securities laws.
As a token issuer, it is important to comply with the national law and additionally with the law of the investors’ territory.
FINMA published guidance for swiss ICOs
Many governments already have published guidance for ICOs. The most recent one is Switzerland:
- Utility tokens stay unregulated.
- Payment tokens needs to comply with anti-money laundering laws.
- Asset tokens (like derivatives and shares) are definitely securities & have to fully comply with regulation.
However, it is unclear how to predict if one token falls under the jurisdiction of utility, payment or asset token.
The most common way to proof if a given token needs to be regulated as a security is the howey test:
- It is an investment of money
- There is an expectation of profits from the investment
- The investment of money is in a common enterprise
- Any profit comes from the efforts of a promoter or third party
Examples:
Utility token: BitShares (BTS), Counterparty (XCP), Lisk (LSK) Security token: Envion (ENV), Aragon (ANT), Iconomi (ICN), Neo (NEO) [likely]
BAFIN published guidance for ICOs
Last week German finance regulator BAFIN stated that ICOs will be regulated on a case-by-case basis. Some tokens could be treated like financial instruments according to WpHG, MiFID II, VermAnlG and WpPG. They could even fall under banking regulation per KWG (Governance Banking Act). They could even fall under banking regulation per KWG (Governance Banking Act). The issuer needs to proof that he is not issuing a regulated security token.
Preview: Fungible Assets vs Collectables Part 3
With courtesy of Vaultoro, the first bitcoin gold exchange, I was able to provide the community with this overview.
The last publishing of this series will be Part 3: 11 Practical ways to create and issue your own Non-Fungible Token. There will be shown how to govern the issuance by introducing technical software and hardware solutions.
Great post & analysis!
Could not have said it better ourselves.
Check out https://opencollectors.network
We already have a proof-of-concept working, where you can create your own non-fungible collectibles :)
Disclaimer: Works with the Ropsten test network. We're currently in private sale, after which we're doing a full security audit for our contracts and deploying on mainnet.
Thank your for this article!
Age of Chains also is a blockchain video game being developed on Counterparty.
As a player, you find yourself in an intergalactic clash of cultures to defend our galaxy.
You can find more information about the game under www.AgeofChains.com
@gamestack
@ageofchains
Thank you very much for the positive feedback!
Here is Part 3: 14 ways to issue your own Non-Fungible Token. It covers more details about the Counterparty project and other useful blockchain solutions like Hyperledger and Ethereum ERC 721.