The Largest Theft in Human History: A Breakdown of the $1.46 Billion Bybit Heist
On the evening of February 21st, blockchain detective ZachXBT was the first to disclose that suspicious funds amounting to over $1.46 billion had been observed flowing out of Bybit, with mETH and stETH being exchanged for ETH on decentralized exchanges (DEXs). This has now become the largest theft in the history of cryptocurrency (based on the value at the time).
This incident not only exposed significant security risks in the crypto space but also sparked a global conversation on technical vulnerabilities, industry collaboration, and crisis response. Below is a detailed analysis of the incident’s timeline and the reactions from various stakeholders.

Timeline of the Incident: On-chain Anomalies and Market Turmoil
On the night of February 21, Beijing time, ZachXBT issued an alert via Telegram, revealing abnormal fund outflows from Bybit’s Ethereum cold wallet, totaling $1.46 billion. Blockchain analytics firm Arkham Intelligence confirmed this movement and reported that the stolen funds had started to be exchanged for ETH on decentralized exchanges (DEXs), with some being transferred to multiple new addresses.
Almost simultaneously, the cryptocurrency market reacted sharply. Bitcoin’s price plummeted from a high of $103,000 to $94,800, a drop of 3% within 24 hours. Ethereum also saw a decline from $2,700 to $2,615, a 5% drop. The market panic spread rapidly, with over 170,000 investors liquidated globally, totaling $572 million in losses.
Conor Grogan, a senior executive at Coinbase, stated that, based on the price of ETH at the time of the theft, this event will go down as the largest theft in human history, surpassing the $1 billion theft from the Central Bank of Iraq and approximately 10 times the losses caused by the 2016 DAO hack.
Attack Method: Forged Signature Interfaces and Contract Logic Manipulation
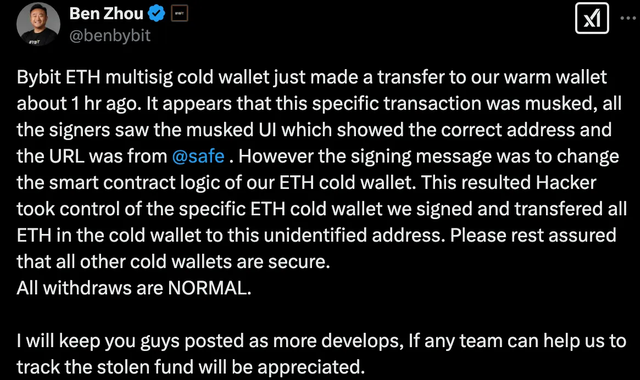
Bybit CEO Ben Zhou quickly went live after the incident was confirmed, revealing details of the attack. The hackers forged the user interface (UI) of a Safe (formerly Gnosis Safe) multi-signature wallet, tricking the signatories into approving the transaction. Under the guise of showing a “correct address” on the UI, the actual transaction payload was altered to include malicious commands that modified the logic of the cold wallet’s smart contract. The attackers used this method to gain control of the cold wallet and emptied it, stealing approximately 401,347 ETH and an equivalent amount of stETH, valued at about $1.46 billion.
Blockchain security company SlowMist added that the attackers deployed a malicious implementation of the contract and utilized backdoor functions like sweepETH and sweepERC20 to transfer the funds. The key vulnerability was a “social engineering attack” on the multi-signature approval process — convincing just one signer to approve a seemingly normal transaction would allow the attackers to use a delegatecall command to modify the contract storage slot (slot 0), replacing the cold wallet's implementation address with the attacker’s malicious contract.
Research from security firm Groom Lake suggested that the attackers might have exploited a vulnerability involving duplicate cross-chain transaction hashes. In 2019, Ethereum and Base chain’s Safe contract deployment transactions shared the same hash, which is mathematically nearly impossible, indicating a potential signature or data replay risk. However, the Safe team denied any flaws in their contracts, asserting that the issue was due to EIP-155 not being enabled (a standard to prevent cross-chain replay attacks). They also emphasized that, had the issue been in their protocol, Bybit would not have been the target.
Identifying the Culprits: North Korean Hacker Group Emerges
Within 24 hours of the incident, ZachXBT presented “concrete evidence” linking the hack to North Korean hacker group Lazarus Group. On-chain data revealed that the hacker’s test transaction patterns, wallet associations, and timelines closely matched those of previous attacks, including those on Radiant Capital (Dec 2023, $50 million loss) and WazirX (March 2024). Blockchain security company Blockaid pointed out that the “blind signing” technique (where users approve contracts without fully reviewing them) has become a trademark of North Korean hackers, with similar methods used in multiple attacks since 2023.
The motivation behind Lazarus Group’s actions is believed to be linked to the funding needs of the North Korean regime. Coinbase’s Conor Grogan commented that the stolen amount far surpasses the $1 billion theft from the Iraqi Central Bank in 2016, potentially making it “the largest financial crime outside the crypto space.”
Bybit’s Crisis Response: Transparency and Industry Support
In the face of this massive loss, Bybit displayed unprecedented transparency and decisive action. Ben Zhou made a public commitment during the livestream, stating that the platform would keep withdrawal channels open and fully compensate users for their losses. He revealed that Bybit manages over $20 billion in assets, and other cold wallet assets (such as BTC and USDT) had not been affected. If necessary, they would use bridge loans to fill the funding gap.
Industry collaboration played a critical role. On-chain data showed that Binance and Bitget transferred a total of 50,000 ETH (around $140 million) to Bybit’s cold wallet after the incident. Of this, Bitget’s transfer accounted for a quarter of its ETH reserves. Ben Zhou thanked Bitget for their emergency support but clarified that Binance’s transfer was “unofficial” and conducted voluntarily by their partnership. Other key figures, such as Tron founder Justin Sun and OKX CMO Haider Rafique, pledged assistance in tracing the funds, while exchanges like KuCoin and SuperEx called for industry-wide efforts to combat crypto crime.
Ben Zhou also posted an update on X (formerly Twitter), reassuring users:
“Please rest assured that all other cold wallets are secure. All withdrawals are NORMAL. We understand the current surge in withdrawal requests. Although the high volume may cause delays, all withdrawals are being processed normally. Bybit has enough assets to cover the losses, with an asset management scale exceeding $20 billion, and will use bridge loans if necessary to ensure the availability of user funds.”
The Aftermath: Hacker Holds 0.42% of Global ETH Supply
As of February 22, the hacker’s address held 0.42% of the global ETH supply, making it the 14th largest ETH holder, far surpassing holdings by the Ethereum Foundation and Vitalik Buterin. Bybit confirmed it was working with Chainalysis and other blockchain analytics firms to flag and block related addresses, preventing funds from being cashed out through compliant channels.
Legally, Bybit plans to report the case to Interpol and seek support from the U.S. Department of Justice to sanction North Korean hackers.
According to DeFiLlama data, Bybit’s total outflow in the past 24 hours, including the stolen funds, amounted to $2.4 billion. The platform’s on-chain verifiable assets now exceed $14 billion, with Bitcoin and USDT accounting for nearly 70% of the total. Bybit has reported the case to relevant authorities and will provide further updates once more information is available.
A Call for Industry and Global Action to Combat Crypto Crime
The Bybit theft serves as yet another wake-up call for the security of the crypto industry. The $1.46 billion loss is not just a technical flaw but a serious test of the industry’s trust framework. SuperEx has called on the entire crypto community to unite in the fight against crypto crime. Whether exchanges, project teams, tech developers, or everyday users, all must actively participate in this defense. Through technological upgrades, information sharing, and industry collaboration, we can build a stronger defense system, making it impossible for hackers to thrive.
At the same time, the global nature of crypto crime makes it clear that regulatory measures from any single country are insufficient. The Bybit incident underscores the need for international cooperation to effectively combat cross-border crypto crime. SuperEx calls on governments, law enforcement agencies, and industry organizations to strengthen collaboration and establish a global mechanism for fighting crypto crime.
Only through a combined effort of technology and regulation can we create a safer, more trustworthy environment for the crypto industry and defend its integrity and dignity.
Conclusion: A Battle with No Winners
The Bybit theft once again proves that the crypto industry is a space where prosperity and risk coexist. While the industry quickly mobilized and demonstrated unity, the loss of $1.46 billion has become a fait accompli. As SlowMist founder Yu Xian put it:
“Security is not about point defense; it is a global game of the entire ecosystem.”
