Introduction to Cryptography

Cryptography comes from the ancient greek meaning: "crypto" = secret, "graphy" = writing.
Let's say that Messi wants to send Pelé a message, but he doesn't want anyone else to see the content of the message. Messi must send the message to Pelé via a non secure way, like the Internet or via Radio. However, he is not sure that the message won't be seen by any other person. What if there is a middleman trying to read the secret message?
The solution for Messi is simple: use cryptography!
If he encrypts the message he won't have to worry if someone will get it. Pelé then needs to decrypt the message to read it.
Some terminology
Cryptography: method to send secret messages using a code
Crytanalysis: trying to break the code and read those messages
Plaintext: message in its original form. very easy to understand its contents
Ciphertext: message in coded form
Key: mathematical operations we can perform on a value
Encryption: transforming PT to CT
Decryption: transforming CT to PT
Cipher: the method used for encryption
Steganography: the practice of hiding information
How do we know if a cryptographic technique is "secure"?
We let lots of smart people try to break it (cryptanalysis).
If they can't, we assume it is secure.
Frequency analysis
Cryptanalysis technique described in the 9th century by Al-Kindi in Iraq.
Not all letters in a language occur with the same frequency.
Some languages have certain characteristics. For example, here are some patterns of the English language:
- E is most common letter
- vowels are about 40%
- vowels tend to be separated by consonants
- Q tends to be followed by U
- etc.
Caesar algorithm
Substitute letters by N letters away (e.g. N = 3. A is D, B is E, C is F...)
How do we break it? try all possible values for N.
Example:
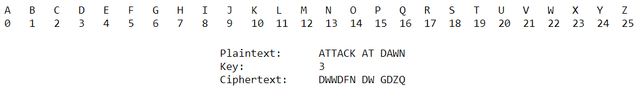
If we try here all the 26 letters we will easily get to the key 3.
Vigenére
It's a poly-alphabetic cipher where one plaintext letter can become different ciphertext letters. It uses a text based key and a modulo arithmetic to perform the encryption. Using frequency analysis is possible, but much more difficult.
Example:
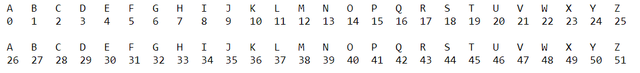
Let's chose a key: MONKEY
We now add the numbers of the letters and get the result letter:
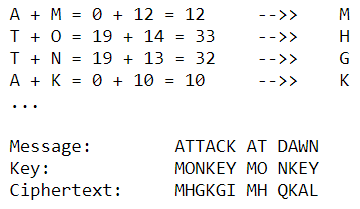
One-time pad
Vigénere cipher with a randomly chosen key as long as the message. The key needs to be shared between parties beeforehand and can NEVER be re-used. Provable unbreakable without the key.
This is the only perfect cryptography.
Example:


All of the previous techniques have two basic components:
- algorithm (what you do to the message)
- key (the secret that you need in order to encrypt/decrypt properly)
When using these algorithms, the key is the secret. The algorithm is public.
More details:
Cryptography (Wikipedia)

Check out my Blockchain website: Operation Blockchain
Hello @martins87! This is a friendly reminder that you have 3000 Partiko Points unclaimed in your Partiko account!
Partiko is a fast and beautiful mobile app for Steem, and it’s the most popular Steem mobile app out there! Download Partiko using the link below and login using SteemConnect to claim your 3000 Partiko points! You can easily convert them into Steem token!
https://partiko.app/referral/partiko
Congratulations @martins87! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!