Vault12 - Securing the Digital Fortune, Digitally!
Introduction
Each of us own assets that are dear to us and the asset could be hard cash, jewellery, legal documents and prized artefacts and so on. The assets and their value may vary according to each individual’s taste, sensibilities and of course affordability. Irrespective of the kind of asset we own, protecting our assets is equally important as the ownership. The more pricey the asset, the higher will be the need for safeguarding the asset. We use traditional means of storage, viz. safe deposit boxes at home or banks, which are not necessarily foolproof as they are open to a variety of threats, such as robbery, theft, natural disasters, and so on.
With the technology revolution that has impacted most aspects of human life, the rules of the economy are also being re-written. It is no wonder today we are looking at the onset of digital assets. Their increasing popularity has led to more and more individuals opting to own digital or crypto assets, including cryptocurrencies (example: Bitcoins). Cryptocurrency is a medium of exchange for secure financial transactions with the ability to create additional units and verify the transfer of assets. Cryptocurrencies are some of the most valuable assets one can own. As in the case of traditional assets, owners of crypto assets will want no less than reliable means to safeguard their precious assets.
Challenge: Safeguarding the Digital Assets
The USP of cryptocurrency assets is that the owner has full control of their access. While this is a huge plus for the owners, the mechanism also comes with its fair share of disadvantages and risks. The cryptocurrency assets are stored either in hardware/software wallets or centralised online accounts. The owners run the risk of forgetting the keys and the last resort back up provided by the wallet vendors in the form of 12/24 pass codes are generally stored on pieces of paper in bank safe deposit boxes. Such storage means are open to thefts, robbery or natural disasters, thereby rendering them highly untrustworthy.
The centralized online accounts are open to hacker threats, and the digital world has already experienced such threats having materialized in cases like MtGox (2014)1, Bitstamp (2015)2, Bitfinex (2016)3 and Coincheck (2018)4. Depending on third parties like Banks or online storage vendors is in direct contrast to the core principle of crypto assets that professes singular and direct ownership for owners. So, online account storage turns out to be as ineffective in providing security as the wallets.
Lack of reliable custody/access mechanism builds scepticism and does hinder wider adoption of digital assets (cryptocurrencies) in the global economy.
Need of the Hour
The biggest bane in the current security mechanism is that the keys and the passcodes are in a centralized environment.
Interestingly, the Winklevoss twins, Tyler and Cameron, tried to address this challenge uniquely. To safeguard their $1.3billion digital fortune, they cut up the bitcoin key and stored the different pieces in different bank vaults across America! While the idea is unique, it is extremely cumbersome and impractical to adopt as a general solution to the current challenge. The need of the hour is a decentralized storage system that is modern, digital and easy to use.
The Solution
Borrowing from the Winklevoss Twins’ logic, Vault12 has built a platform to address the digital custody problems using a decentralized storage system and a powerful cryptography algorithm, ‘Shamir’s Secret Sharing’5.
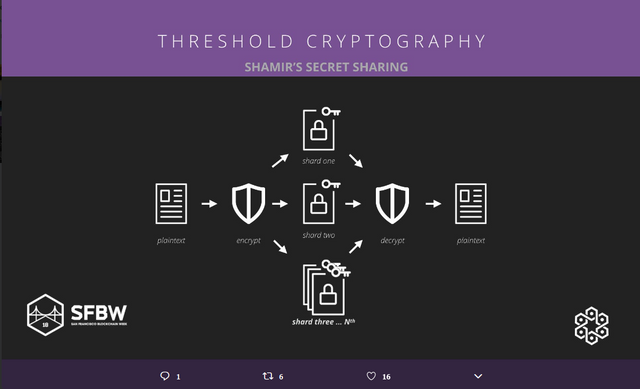
This platform enables the crypto owners to store and secure their crypto assets risk-free with complete control. In a smart approach, this system uses the mobile devices of an owner’s trusted circle of friends and family to form a meshed network for distributed storage of the keys. The cryptographic algorithm shards (divides) the keys, passcodes or documents into multiple pieces and distributes them across different trusted devices authorized by the owner.
For the owner to restore the keys or documents, a predetermined number of devices have to recall a certain amount of these shards or pieces. The most significant advantage is that these pieces individually do not carry any significant data that can be breached for malicious intent.
How does it work?
The mechanism involves three tiers of trust. The highest tier is, of course, the owner and his phone becomes the master device.
The next tier is made up of a group of close family and friends authorized by the owner. They are called the ‘Guardians’. The owner can add his personal mobile device/s as a guardian device/s.
The last tier consists of connections pertaining to the owner’s network of casual contacts. These may not be trustworthy but help in increasing the redundancy. Together, the guardian and the acquaintance devices are called the ‘Custodians’.
Once the above tiers are set up by the owner, he opens a vault of distributed storage on these storage nodes. The app on the master device converts the private keys or the critical data into encrypted shards which are in turn distributed to the custodians for permanent storage. Once the shards are transmitted, the app verifies the storage in a trusted group and is responsible for monitoring the health of the vault from time to time. An active vault generates new shards dynamically in the event of owner inviting new Guardians.
The owner can unlock the vault by requesting for a threshold number of shards from the custodian devices by using social verification. Upon collecting the threshold number of shards, the master device reconstructs the private crypto asset data and allows the owner access and use of the said data.
In the event of loss or compromise of the master device, the owner is safeguarded as there is no critical data stored on the master device. He can still access his crypto asset data by seeking the restoration shards from the guardian devices.
Key Features of Vault12 design:
Decentralization: Vault12 is a fully decentralized platform thereby eliminating the dependency on a centralized point.
Easy to Install and operate: Any user can download the app on a device, install and operate efficiently.
Redundancy: The platform offers a high redundancy by allowing the user to add more custodian devices. Thereby, the platform offers scalability and reliability.
Incremental Access: Access (easy to more complicated) is granted based on the importance of the information stored.
Privacy: The owner enjoys full privacy as the asset data is invisible even within the trusted circle.
Social Verification: Owner can unlock asset data only when one of the guardians approve his identity, thereby eliminating the risk of the breach at the access level.
Fool-proof: Vault12 does not allow the breach of data even if a group of custodians form collusion to access the data. The asset data is safeguarded even in the event of loss or compromise of the device, natural disasters and other threats.
These key features make Vault12 the best cryptographically secure system in business and one of its kind!

Co-founder of Vault12 - Max Skibinsky speaking at a conference.
Conclusion
It is shocking to note that the number of cryptocurrencies permanently lost owing to missing keys / forgotten keys are higher than those lost due to hacking and other reasons. Needless to say that the owners of crypto assets are in dire need of a sophisticated security system that safeguards their treasure from all variety of threats and most of all is simple to manage.
By introducing a distributed, decentralized and serverless digital custody solution, Vault12 has done just that! Designed to be used alongside traditional hardware, software and online wallets, the Vault12 solution is the first of its kind – just what the industry needed today and in future!
You can read more about Vault12 on their Website, Telegram & Twitter.
Follow us on Twitter and Steemit.
Note: This is not financial advice or a recommendation to invest in this or any other ICO. Investors must perform their own due diligence and not rely on external ratings to make their final investment decisions. ICOs are risky and 100% loss of capital is possible.
References:
1: https://medium.com/@jimmysong/mt-gox-hack-technical-explanation-37ea5549f715
2: https://arstechnica.com/information-technology/2015/01/bitcoin-exchange-bitstamp-claims-hacksiphoned-up-to-5-2-million
3: https://www.theguardian.com/technology/2016/aug/07/bitfinex-exchange-customers-receive-36percent-loss-tokens
4: http://time.com/money/5123018/coinchec-nem-hack-how-the-hackers-pulled-it-off
5: “Hierarchical Threshold Secret Sharing”
Congratulations @altcocollector! You have received a personal award!
Click on the badge to view your Board of Honor.
Do not miss the last post from @steemitboard:
Congratulations @altcocollector! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!