Global WannaCry Ransomware Attack Earned Distributors Only $26,000 in Bitcoin to Dat

Global WannaCry Ransomware Attack Earned Distributors Only $26,000 in Bitcoin to Date The WannaCry ransomware spread across the world in a short period of time and affected 100,000 computers across 99 countries in the first 24 hours of attack. It successfully breached into some the UK’s largest hospitals, healthcare providers, Russian government agencies and multi-billion dollar corporations. Yet, the masterminds behind the WannaCry ransomware attack have only profited $26,000 from the attack to date. On May 13, award-winning and best selling cyber security author and journalist Brian Krebs revealed in his blog KrebsonSecurity that the distributors of the WannaCry ransomware have only earned $26,000 worth of bitcoin so far. The total ransom payments received by the WannaCry distributors were significantly smaller than what analysts and experts expected, primarily due to the sheer magnitude of the attack. For each computer the WannaCry ransomware successfully encrypted, the malware demanded $300 in bitcoin. Considering that around 1,00,000 computers were affected by the ransomware attack, the distributors could have potentially earned upwards to $30 million from the global attack. Yet, according to Krebs, the developers of WannaCry have only earned $26,000 from the largest ransomware attack in history.
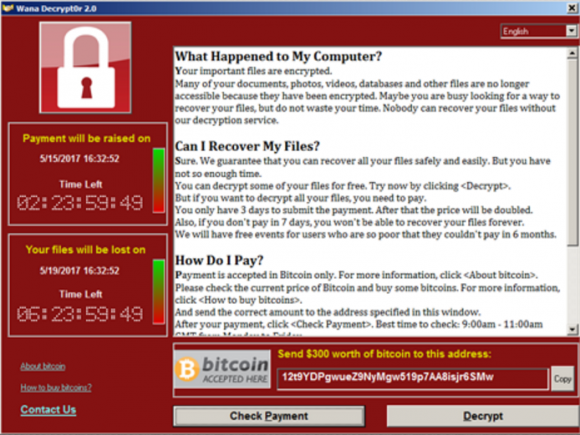
Companies including Elliptic and Redsocks were able to trace the ransomware payments to the actual bitcoin addresses of the WannaCry ransomware distributors using the three bitcoin addresses hard-coded onto the malware. Using those addresses as basis, Elliptic also implemented a bitcoin transaction untangling tool to trace other potential payments that were initiated by the three hard-coded bitcoin addresses. Relative to the impact the WannaCry ransomware had on the global economy and the financial damages corporations had to endure due to the attack, the reward for the ransomware distributors was significantly small. Hence, the distributors of the ransomware most likely did not foresee a $26,000 revenue. Although most major UK newspapers and mainstream media outlets featured more “How to Buy Bitcoin” articles on their front page than ever before, the lack of knowledge toward bitcoin of the general population likely led to an underwhelming amount of bitcoin ransom payments.
Law enforcement agencies including the FBI also previously warned victims not to pay the ransom when encrypted because there exists no guarantee that the distributors will provide decryption keys for the disabled files. Such warnings from law enforcement agencies may also have convinced victims not to pay the ransom when affected. “The FBI does not support paying a ransom to the adversary. Paying a ransom does not guarantee the victim will regain access to their data; in fact, some individuals or organizations are never provided with decryption keys after paying a ransom. Paying a ransom emboldens the adversary to target other victims for profit, and could provide incentive for other criminals to engage in similar illicit activities for financial gain,” the FBI said.