Multiple ERC20 Smart Contracts (CVE-2018-10299) Vulnerable To New BatchOverflow

A blockchain security company, PeckShield, has developed a system that automatically notifies suspicious transactions that take place (Ethereum-based token transfers) including transactions that involve unreasonably large tokens.
On 22nd April 2018, 03:28:52 a.m. UTC, the system sent a notification of a BEC token transaction that seemed unusual. In the transaction, it is reported that an individual transferred a large amount of the BEC token being 0x8000,0000,0000,0000,0000,0000(63 0’s).
Two transfers are reported as each of them involve a similar amount of tokens from a matching contract (BeautyChain), but two different addresses.
This anomaly forced blockchain security to look into their smart contract code whereupon they realized that the transfers came from an “in-the-wild” attack exploiting an unknown vulnerability that previously existed. The vulnerability is referred to as the batchOverflow.
The batchOverflow vulnerability in detail
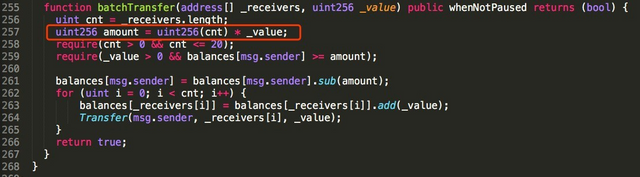
In the code is shown above, the vulnerability function is generally located in the ‘batchtransfer’. Line 257 indicates that the amount, the local variable, is basically calculated as the product of value (_value) and cent (cnt) whereby the value may be arbitrary 256 like 0x8000,0000,0000,0000,(63 0’s).
According to the blockchain security contractor, if two receivers (_receivers) make their way into batchtransfer, with the large value then the amount can be overflown and made zero. They proceed to explain that with the amount then an attacker can pass sanity checks in line 258 and 259, and then make irrelevant the subtraction that is in line 261.
Interestingly, lines 262-265 show that the two receivers’ balances would be added by the large value and cost not even a dime to the attacker.
PeckShield was forced to run their system further in an effort to scan other contracts and analyze them. The results were that several ERC20 contracts are also vulnerable to batchOverflow.
They went ahead to successfully demonstrate a transaction with one of the vulnerable contracts (not tradable) to prove the exploit concept.
Proof-of-concept-exploit
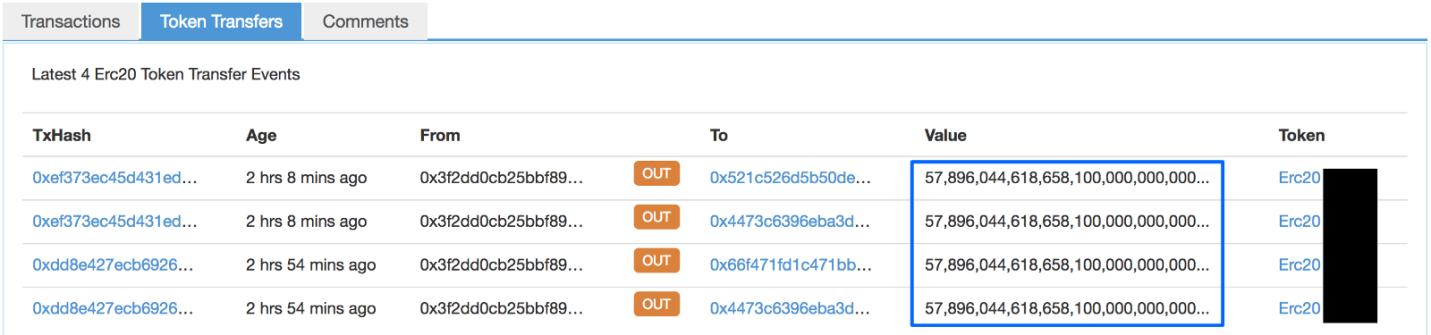
They made efforts to contact all the teams that own the vulnerable contracts by the time of writing but they noted that with the “code-is-law” principle, there is a security response mechanism known yet to remedy the vulnerable contracts.
In addition, they indicated that they are not in any position to react by suspending trade of the vulnerable tokens in the various exchanges as they are a third party security team that is independent and there are potential values that are associated with the tokens.
However, later at 16:12 GMT, a suspension was announced of withdrawals and the trading of BeautyChain (BEC) by OKEx. Other exchanges need to coordinate as there are existing tradable tokens that are vulnerable to batchOverflow.
The company explained additional complexities and specifically highlighted the possibility of an attacker possessing huge amounts of the tokens by simply exploiting the vulnerable contracts. The worrying point is that the attacker trades the tokens with cryptocurrencies, thereby manipulating the prices.
Consequently, this event reminds us of the recent Binance incident that happened early last month where a criminal crew controlled the accounts of the Binance customers and drove up Viacoin just to cash out the other side.
source: cryptocoin.news
This user is on the @buildawhale blacklist for one or more of the following reasons:
Resteemed your article. This article was resteemed because you are part of the New Steemians project. You can learn more about it here: https://steemit.com/introduceyourself/@gaman/new-steemians-project-launch