Lessons from the TREZOR Hack
TREZOR Hack
DEFCON 25 wrapped up a little over 2 weeks ago and we've known about this topic for a while, but it seems like people are just starting to realize that hardware wallets aren't as secure as you might think.
TREZOR is the main offender this time, but the TREZOR v2 and KeepKey may not be safe for long since the vulnerability supposedly exists in the STMicroelectronics chip they all use.
Without getting into the technicals of why and how this hack allegedly works, it ends up giving you access to the seed phrase, device label, and PIN. It doesn't seem like a difficult hack to perform if you don't mind opening the device, and there are supposedly methods that allow you to do it without opening it at all.

TREZOR's response seems to be a firmware upgrade for all devices running firmware versions lower than 1.5.2. More information on the hack is supposed to be released at a later date, after people have a chance to protect themselves by getting the update.
I've always had problems with the fact that hardware wallets aren't phishing resistant and are susceptible to shoulder surfing and evil maid attacks, but accepted these small imperfections since they are orders of magnitude more secure than an online wallet. Still, this is concerning news for those who use hardware wallets as cold storage.
How could TREZOR have avoided this hack?
The Ledger Nano S uses actual secure element chips that should be more resistant to fault injection than the ST32F05 chips in the TREZORs, which is one of the reasons I've defaulted to recommending them over the others. Still, there's that one flaw that all major hardware wallets have, the lack of good multi-factor authentication.
This is understandable. Hardware wallets have to prioritize convenience over security at a certain point, or else their devices will never compete with the devices that are much easier to use and only slightly less secure. Unfortunately, this means that this is likely an issue that isn't going away anytime soon.
What You Gain & Lose with Good MFA
Like most security measures, you lose convenience when you add security. Hardware wallets are the convenient way to store your cryptocurrencies with relative security. It's impossible to know exactly how much more or less secure one system is over another without data, and that's not something there's a lot of given that crypto is both so new and uncontrolled.
If you're using a TREZOR or Ledger Nano S for your daily driver to sign transactions, then you're more likely to notice if your device has gone missing or unsupervised - even for a short time. This means that you are reasonably safe from somebody tampering with your device and getting the sensitive information out. If you're storing it in a locked safe or some other secure location, you are also reasonably safe.
It's the people who own hardware wallets and keep them on their desk at work or in a drawer at home that need to reconsider what they're doing.
What's the Solution?
Locks can be picked and broken, safes can be cut through, and safety deposit boxes are only as trusted as the banks and government. So how do you increase your security when nothing is 100% guaranteed to work?
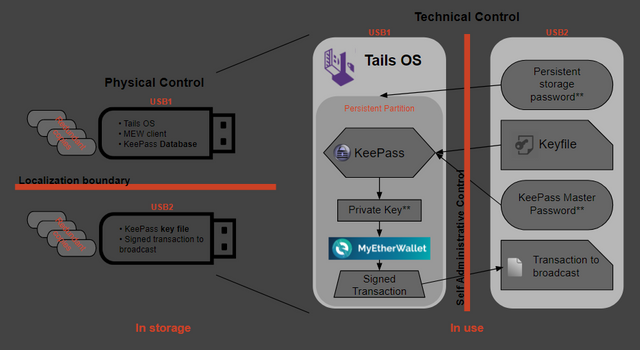
THIS is the one feature missing from mainstream hardware wallets - the ability to break up access control over multiple physical locations in addition to digital/memorized ones. Ideally, there should be an option to store a portion of sensitive information in one location and another portion in a different location. This ensures security even if one location is compromised, something that should already be difficult but also noticeable by the user before a second location is also compromised.
If you're interested in using a system that supports this, read part 3 of my security guide for creating a secure wallet. Not only does my guide show you how to set up a system that can utilize multiple secure physical locations, it also allows you to use multiple digital security measures. For more info, see the MyEtherWallet help docs on cold storage (where you'll also find my guide).
Until we see a mainstream device that supports physical keys (in the form of RFID, physical 2-factor like Yubikey, etc), I can't recommend hardware wallets over my own system for cold storage. For daily use, remember to keep your hardware wallet close.
Great post, thanks for sharing. Trezor has been making misstep after mistep. Slow to support Ethereum, giving Nano a crease to exploit, dopey about playing Bitcoin politics rather than remaining neutral with the whole "bcash" nonsense rather than just calling it "Bitcoin Cash" like it called itself, and now this is the worst of all. I believe their engineering team is very small (Emin says it's 2 people).
When you have such a small company, personal politics can easily make their way into the corporate message. It's definitely unfortunate. I just hope that this doesn't dissuade people from getting hardware wallets in general.
Strangely enough, I came to this article through Reddit. :-)
@tomshwom hasn't been getting the upvotes and attention that the quality of his posts warrant on Steem. It should fix itself in time.
That's some high praise @eeks. You're one of my biggest supporters, thank you.
I missed this so sorry for commenting late but I see you make great content. Even the picture linked to an earlier post, neat.
On to my main question:
Do you think you could have multiple private keys, one for big transactions which you'd keep secure in a hardware wallet and one for daily transactions?
Sort of like you would have daily spending limits on your credit or debit card but with private keys. The same way there are IRL keys which open multiple doors. One part has an entry to the hall of the building and one is more private and is for your apartment.
You certainly could, but I'd recommend first considering what you're gaining or losing by doing this.
In my opinion, the most important thing for people is to understand their own personal "system". If you have everything in a hardware wallet, and that's the only place you store your crypto, then you understand that protecting that one seed phrase is the only thing you have to be sure about in your system. It's very simple.
However, once you start splitting up funds across multiple types of storage, all with their own risks, you start to introduce a lot of complexity to your system. So, if you want to spit your funds (for organization, safety, convenience, or whatever reason), the most important thing is to plan, verify, and execute properly. Don't try to mush all the different wallets you've been using together and hope it all creates a cohesive system. Start fresh, and plan it all out first.
The last thing you want is to introduce complexity when you're not gaining any security of organizational benefits. If you have 300 addresses, but they are all stored in the same way, then you're only hurting yourself.
Right, well to make it more concrete, I think one should approach this as having a savings account which is on a hardware wallet or USB key with private keys split on multiple locations maybe. Then I'd have a few of those according to the funds or hide them using steganography in innocent pictures of my kids for example.
It's interesting that you mentioned steganography. I wrote a short paper in university about encoding images within other images and how this could be used for any arbitrary data. I uploaded it here if you want to check it out. I think I'll actually make a steemit post out of it and upload the code so that people can do it themselves.
That would be really cool
but unfortunately the link is not workingsorry I misread, downloaded it now! And who knows, maybe the future on how to effectively conceal your private keys!Also posted at https://steemit.com/cryptocurrency/@tomshwom/hiding-information-in-plain-sight if anybody else wants to read it without having to download anything.
Great, maybe this will be good seed for a project? Sort of to hide your keys?
Hey @tomshwom! Thank you for taking the time to write this post. Have you by any chance ever had a look at the Digital Bitbox? I would be very interested to hear what you think about this device, especially since I just wrote a review of it. From what I can see this device is very secure if 2FA is enabled, since physical touch is required.
Still, I completely agree with your point about splitting up control of a wallet. Shouldn't this theoretically be possible already with current cryptographic methods anyway?
Responded on your review post :)
Ledger has come out with a better response regarding concerns about the new 1.5.2 firmware that can be read here. I've also asked a TREZOR rep some questions on reddit, comment thread here.
nice post, check this mate https://steemit.com/bitcoin/@raphavongal/hardwallets-nop-nop-this-is-better
paper wallets with master key in cryptosteel mate!!! :-) maybe this is the better now!
I've never been a fan of beefed up paper wallets like this. It's pseudo-security, just makes you feel good without actually being worth much.
I see, and so ledger maybe is the better option yet?
Highly dependent on your use case. Having your private key on any kind of paper wallet becomes absolutely useless if you type it into an online system. If you're purely using it for cold storage and only plan on ever withdrawing form it one time, then paper wallet's are okay as long as the keys are generated offline and stored securely.
If you want to use your wallet, then something like the Ledger Nano S is very convenient since it is easy to use and very secure. The drawback is that it's pricey and you should be keeping additional backups (which also need to be secured) in the case that it breaks.
that's the idea, I just withdraw one time, keys generated off line and also when import to the wallet that I want I put the key off line before turns on the wifi and everything in a Macbook, never windows. ;-)
Then your security is 100% dependent on where you store your paper wallet. In my opinion, I think it's a better idea to split the key into separate, redundant locations. For example:
An encrypted form of the private key (memorized password) stored on cloud service. Doesn't matter if they see it because it's encrypted and I only know the password. The password is simple enough to remember, but not used anywhere else (or any similar password). This is what's called a "one time pad" and it's provably uncrackable.
Split the private key in half, storing one half in a safety deposit box (or other off-site secure location) and one half locally. Also, keep copies of both halves in other secure locations that you can check regularly to make sure they are okay. This allows for you to be robbed and not lose your whole key, and you have backups so you can recreate the full key.
wowoow tks a lot mate!!! will send some SBD later because your time spent explaining this to me!! :) really appreciated
Thanks for you post, these types of security updates are always so important, and usually don't gain that much attention. I will be looking over your past security posts, and looking forward to more posts from you in the future! Followed, thanks!