Work Test (PoW), Explained

What is the Work Test?
Proof of Work, or PoW (for its acronym in English), is the original consensus algorithm in a Blockchain network.
In Blockchain, this algorithm is used to confirm transactions and produce new blocks in the chain. With PoW, the miners compete among themselves to complete online transactions and obtain rewards.
In a network, users send each other digital tokens. A decentralized database gathers all transactions in blocks. However, care must be taken to confirm the transactions and organize the blocks.
This responsibility is based on special nodes called miners, and a process is called mining.
The fundamental working principles are a complicated mathematical conundrum and the possibility of easily testing the solution.
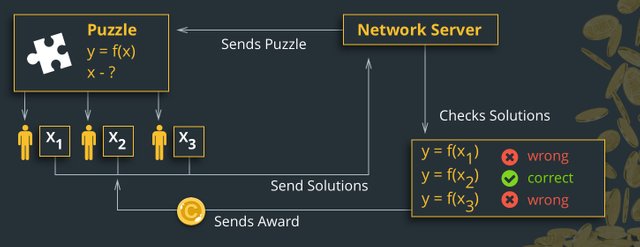
What do you mean by a "mathematical puzzle"?
It is a problem that requires a large amount of computing power to solve.
There are many of them, for example:
hash function, or how to find the entrance knowing the exit.
factorization of integers, in other words, how to present a number as a multiplication of two other numbers.
guided puzzle protocol. If the server suspects a DoS attack, a calculation of the hash functions is required for some nodes in a defined order. In this case, it is a problem of 'how to find a string of hash function values.'
The answer to the problem of PoW or mathematical equation is called hash.
As the network grows, it faces more and more difficulties. Algorithms need more and more hash power to resolve. Then, the complexity of the task is a sensitive issue.
How?
The precise work and speed of the Blockchain system depend on it.
But the problem should not be too complicated. If it is, block generation takes a long time. Transactions are blocked without execution and, as a result, the workflow is blocked for a while. If the problem can not be solved in a defined period of time, the generation of blocks will be a kind of miracle.
But if the problem is too easy, it is prone to vulnerabilities, DoS attacks and spam.
The solution needs to be reviewed easily. Otherwise, not all nodes are able to analyze if the calculations are correct.
Then you will have to trust other nodes and that would violate one of Blockchain's most important characteristics: transparency.
Four.
How is this algorithm implemented in the Blockchain?
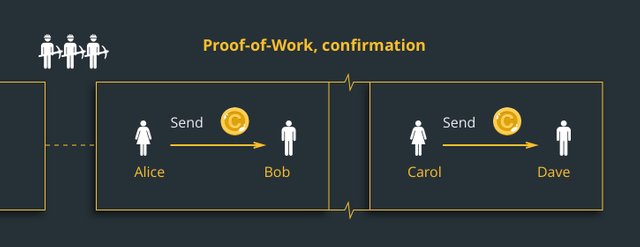
The miners solve the puzzle, form the new block and confirm the transactions.
The complexity of the puzzle depends on the number of users, the current power and the network load. The hash of each block contains the hash of the previous block, which increases security and avoids any block violation.
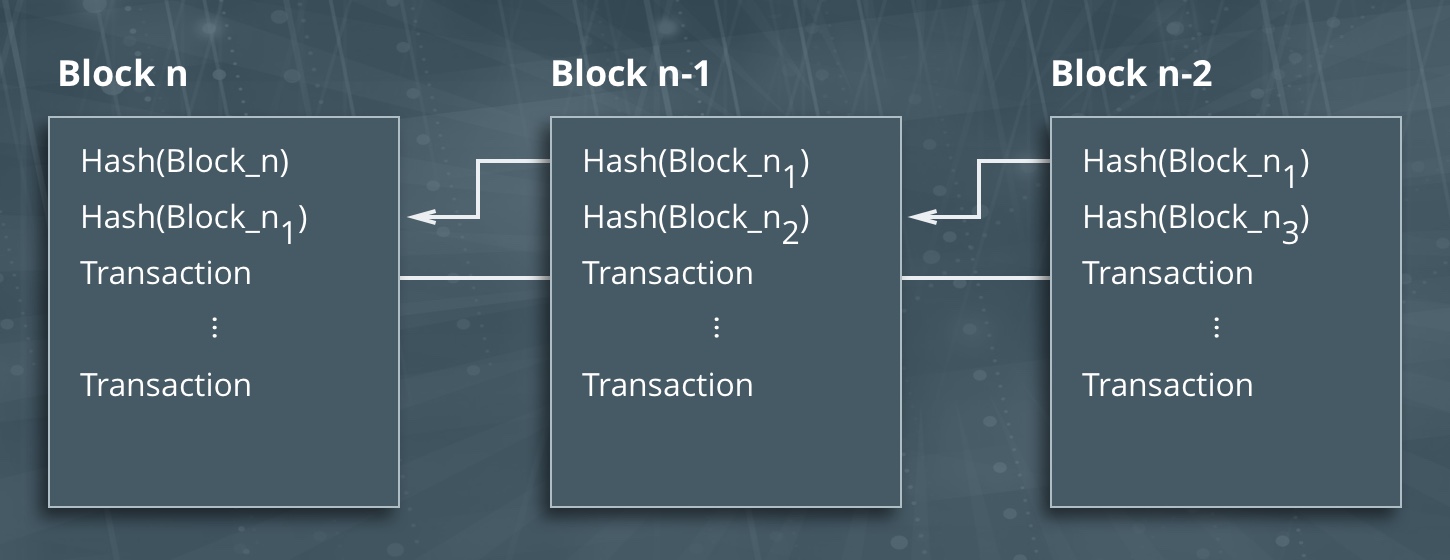
If a miner manages to solve the puzzle, the new block is formed. Transactions are placed in this block and are considered confirmed.
And where is the PoW generally implemented?
The work test is used in many cryptocurrencies.
The most famous application of the PoW is Bitcoin. It was Bitcoin that laid the foundation for this kind of consensus. The puzzle is Hashcash. This algorithm allows changing the complexity of a puzzle based on the total power of the network. The average formation time of the block is 10 minutes. Bitcoin-based cryptocurrencies, such as Litecoin, have a similar system.
Another great project with PoW is Ethereum. Given that almost three of the four projects are implemented on the Ethereum platform, it is safe to say that most Blockchain applications use the PoW consensus model.
6
Why use a PoW consensus algorithm in the first place?
The main benefits are the defense against DoS attacks and the low impact of the participation in the mining possibilities.
Defense of DoS attacks. The PoW imposes some limits on the actions in the network. They need a lot of effort to be executed. An efficient attack requires a large amount of computational power and a lot of time to do the calculations. Therefore, the attack is possible but useless since the costs are too high.
Mining possibilities. It does not matter how much money you have in your wallet. What matters is having a great computational power to solve the puzzles and form new blocks. Therefore, holders of large amounts of money are not in charge of making decisions for the entire network.
7
Any defect in the PoW consensus algorithm?
The main disadvantages are the large expenses, the "uselessness" of calculations and 51 percent of attacks.
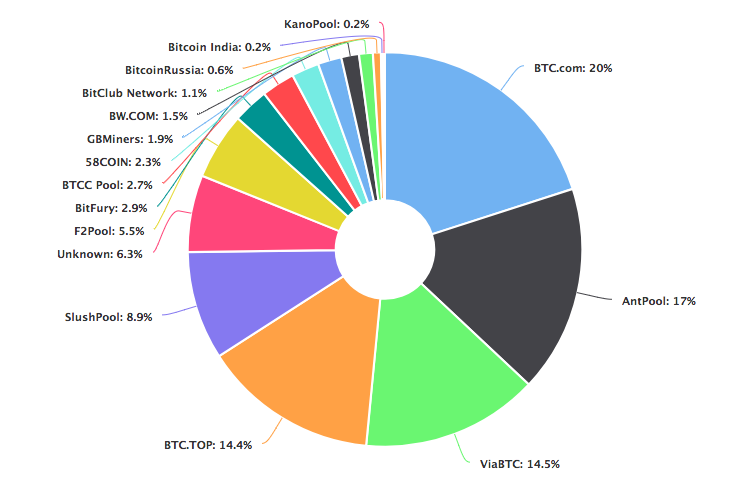
Big expenses Mining requires highly specialized computer hardware to execute complicated algorithms. The costs are unmanageable. Mining is available only for special mining groups. These specialized machines consume large amounts of energy to operate that increase costs. The large costs threaten the centralization of the system, since it benefits. It is easy to see in the case of Bitcoin.
"Uselessness" of the calculations. The miners do a great job to generate blocks and consume a lot of energy. However, their calculations are not applicable elsewhere. They guarantee the security of the network but they can not be applied to businesses, sciences or any other field.
8
51% attack, what are you talking about?
A 51 percent attack, or majority attack, is a case in which a user or group of users controls the majority of the mining power.
Attackers have enough power to control most events on the network.
They can monopolize the generation of new blocks and receive rewards, as they can prevent other miners from completing blocks.
They can reverse transactions.
Suppose Alice sent money to Bob using the Blockchain. Alice is involved in the 51 percent attack case, Bob does not. This transaction is placed in the block. But the attackers do not allow the money to be transferred. There is a bifurcation occurring in the chain.
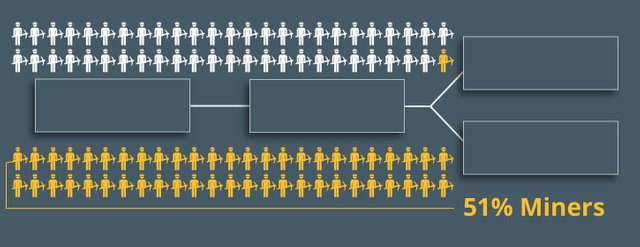
In addition, the miners join one of the branches. And since they have most of the computational power, their chain contains more blocks.
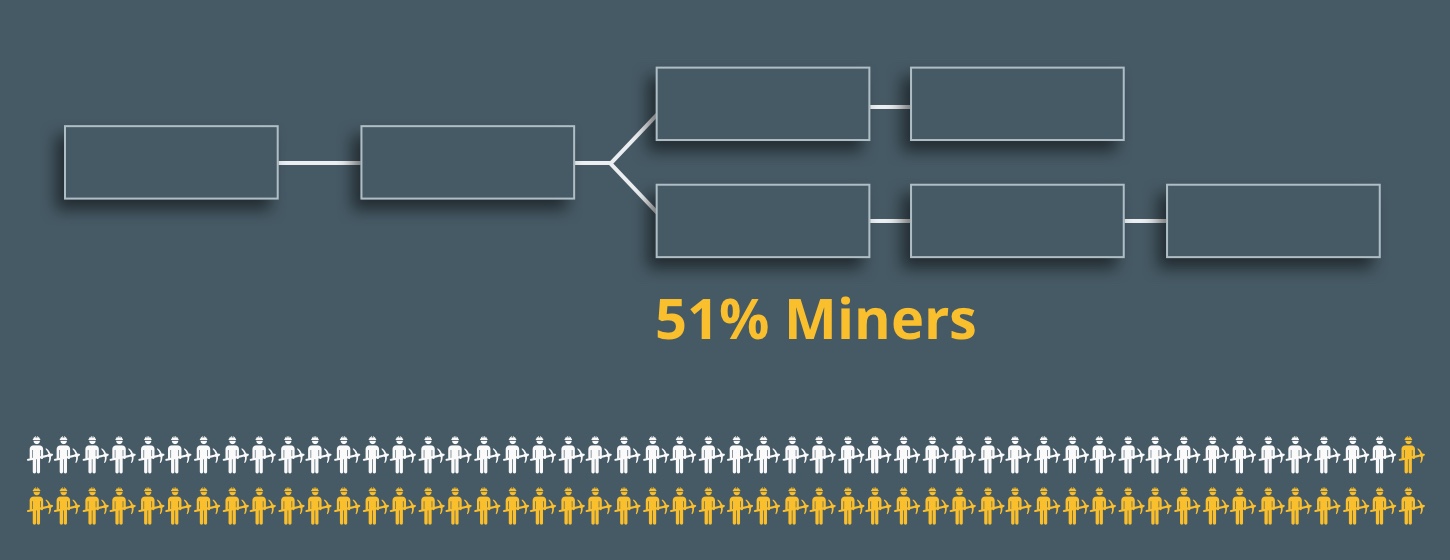
In the network, a branch that lasts longer remains, and the shorter one is rejected. So, the transaction between Alice and Bob does not take place. Bob does not receive the money.
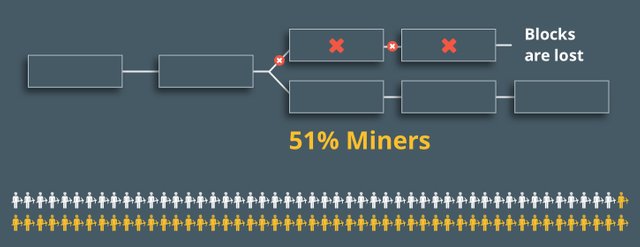
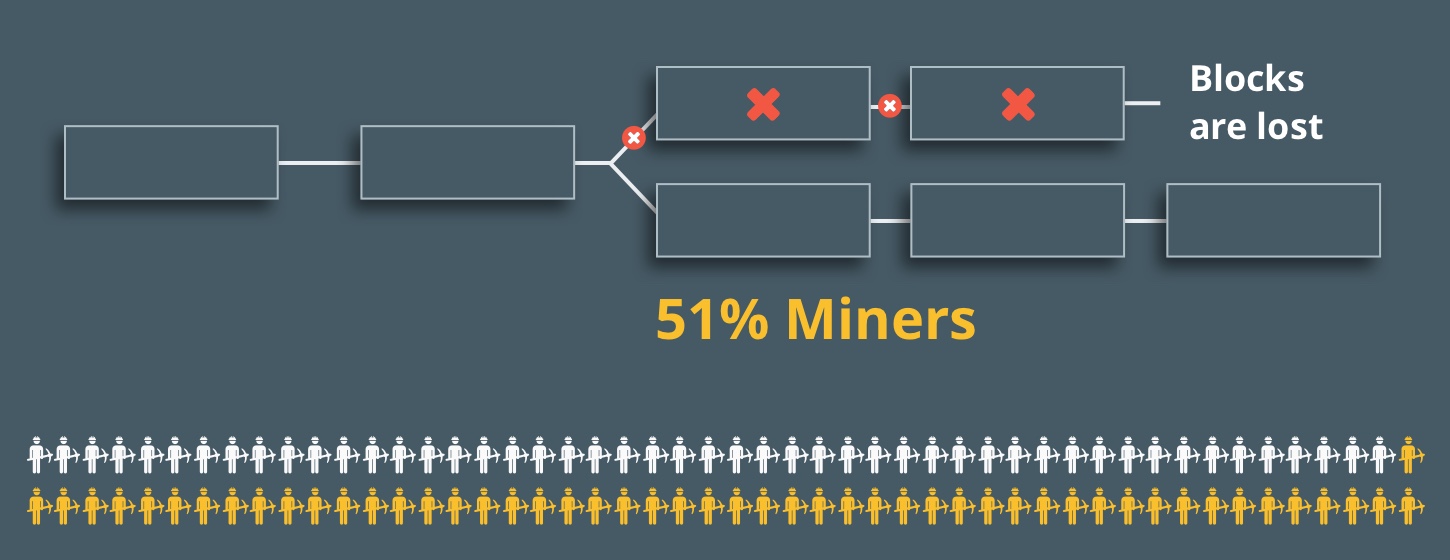
By following these steps, attackers can reverse transactions.
The attack of 51 percent is not a profitable option. It requires a huge amount of mining power. And once it is publicly exposed, the network is considered compromised, which leads to the exit of users. This will inevitably move the price of the cryptocurrency down. All in consequence, the funds lose their value.