8 Steps to Protecting Your Cryptocurrency
And why a bitcoin wallet just isn’t enough

After purchasing your first cryptocurrency and diversifying your investment into altcoins, protecting your investments should be your next priority.
Normal computers are not very secure. They can have viruses and other bugs which allow people to spy in on you and your information as well as make forced changes to your computer.
As mentioned in intro to crypto, cryptocurrencies distribute the responsibility of verifying and recording transactions to any number of computers. This system is known as the “blockchain”.
The distributed recording system is commonly described as “immutable” because once data is verified and recorded it becomes permanent and nearly impossible to edit by hackers or other destructive people.
Because the blockchain lets two people transact directly with each other, there is no need for middlemen such as banks and payment system companies like Paypal.
On the other hand, cryptocurrencies have none of the regulation and insurance found in traditional banking because banks and governments have no part in creating or maintaining crypto.
This organizational independence means you are responsible for safely storing your access keys. You are also responsible for the security of your email, phone, and computer. To protect against any single point of loss, you should also create secure backups of your access keys.

If your email, phone and/or computer is not secure and your bitcoin is stolen, there is nobody to call to get your money back.
The most famous and widespread theft of bitcoin was valued at $450,000,000. While there are other smaller and less-known thefts such as losing $8,000 in Coinbase and having $20,000 stolen from Bittrex the point I’m trying to make is, you are responsible for your crypto.
In this walkthrough, I’ll be showing you the different steps I’ve taken to protect my computers, accounts and cryptocurrency for the long term.
Please note, nothing published by me or Decryptionary constitutes an investment recommendation, nor should any data or content published by Decryptionary be relied upon for any investment activities. The following information provides only simple steps you can take to increase protection of your crypto. Decryptionary cannot accept responsibility for any loss or inconvenience caused by reliance on any material contained in this article.
8 Step Protection Overview
- Keep your information private, stay secure.
- Only use strong passwords for your email and crypto accounts and use a password manager like Lastpass.
- Create a new, secure email only for crypto at Protonmail. Make all crypto accounts use that email.
- Add 2 Factor Authentication (2FA) to all of your accounts using the Authy app.
- Use strong antivirus software with a good reputation.
- Avoid fake websites and emails, known as “phishing” that aim to steal your information.
- Spread your cryptocurrency among several wallets.
- Tell a trusted family member, someone who might inherit your wealth, about your crypto investments. Provide them with access in case anything unfortunate happens to you.
1. Keep your info private, stay secure.
Social Media
Believe it or not, if you mention on Facebook, Twitter or other social media that you trade cryptocurrencies on an exchange, you become a potential target for hackers.
Obviously, throughout Decryptionary and my articles, I’ve shared that I trade cryptocurrencies. To reduce my risk, all of my accounts were set up from a private email address that has never been exposed. More on this in #3.
Public WiFi
Public WiFi networks in hotels, coffee shops, airports, and stores are an easy target for hackers. Those networks provide a window to your private online data.
If you want to access your cryptocurrency accounts on a public network, using a Virtual Private Network (VPN) such as ExpressVPN or TunnelBear will prevent your information from being intercepted. A VPN will also hide your identity, location, and IP address which identifies your device.
2. Create strong passwords and use Lastpass.
Create Long Passwords
It turns out short, complex passwords are easier to hack than long ones. For example, if tested, “C0mpl3x!”, would be easier to guess than, “HeyThisIsMyPassword!”.
That’s because a hacker has to guess at 20 characters which is more than twice as long as the first password’s 8. The longer the password, the harder it is for a computer to discover it.
Ideally, your password should be 20 characters or longer.
Create Complex Passwords
- Don’t use common dictionary words like monkey, orange, mustang, and password.
- Don’t use letters or numbers in sequence like 12345 or abcdef.
- Don’t use repeated letters/numbers or keyboard patterns like 111, aaa, qwerty, and asdfgh.
- Don’t use personal information like family names, addresses, and birthdays.
- Don’t repeat the same password for any of your accounts.
- Consider using spaces, instead of “mypassword”, use “my password”.
- Consider capitalizing letters like, “My Password”.
- Consider using misspellings like “My Pas$word”.
Store Your Passwords in Lastpass
Lastpass is a password manager. Use it to store your passwords so you don’t have to remember them. Once you save a password, it will always be available for when you need it.
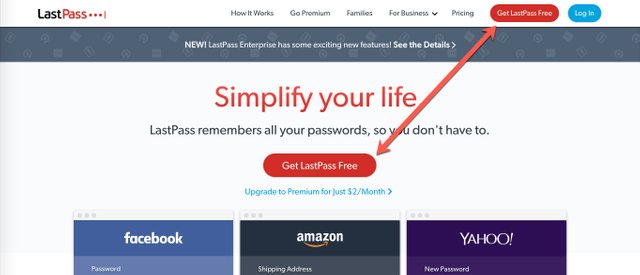
Lastpass uses security similar to cryptocurrencies to protect it from hackers. And all of your passwords and stored information are made unreadable so even if Lastpass was hacked, your information is safe.
Want to know more?
You can find the free PDF with all of the instructions and images at: https://decryptionary.com/what-is-cryptocurrency/8-steps-protecting-cryptocurrency/
About Decryptionary
My mission with Decryptionary is crypto made simple.
Decryptionary is a cryptocurrency and blockchain dictionary. It contains over 200 simple definitions, and awesome 4th-grade, stick-figure images to make this complex subject easy as pie.
Decryptionary is more than just a dictionary. It also has simple walkthroughs and word lists to make sure you really understand the basics of crypto and how to participate.
If you liked this story, and have comments or feedback, please reply below and I’ll get back to you.
You can find more of my articles by following me on my Steemit Blog.
Congratulations @decryptionary! You have received a personal award!
Click on the badge to view your Board of Honor.
Do not miss the last post from @steemitboard:
Congratulations @decryptionary! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Do not miss the last post from @steemitboard:
Vote for @Steemitboard as a witness to get one more award and increased upvotes!