Keeping your assets safe on the typical crypto-platform [MEMO: CRYPTO_NOOBS 101]-Basic Consumer Security No. 1
5-7 min read
Welcome to CloudConnect Studios!

There are a few things you can do which are conceptually and/or literally similar to any secret or valuable security measures.
Ex)
You are trying to use a web based crypto exchange. Let’s say Coinbase.
Password and Username/Email
Just like any internet site with a login, you will have a password and email. Coinbase asks for a lot of KnowYourClient (KYC) information like SSN. Better reason to secure yourself.
Some things work for people better than others based on what resources we have. If you have a physical safe, bolted to the foundation, great. If not, we can go down a short list of different concepts which help us have secure username/password combos.
The first concept
is a quality password. Use lots of unusual characters from different categories (#, letter, punc., accented letters). Brute force password solving (which for a lot of cases is also protected against by the website’s own security protocols like Cloudflare) works when there are not a lot of possible combinations, right?Every new added possible character adds exponential difficulty to the solution. Don’t get lazy. One possibility is to use a phrase like, “pie eating contest,” and distort the sh*t out of it, e.g. “Pi3_aighT1n}G#8#te~+.”
When you make unexpected moves it may increase your security. Change the order of words in the phrase. It only needs to contain characters within the accepted characters list on the platform.
The second concept
is decentralization. You can put your credentials in multiple secure places.Try putting them in an electronic document, like a .txt file (text file) and in a small notebook.
Put the .txt file on an offline storage device (i.e. flash drive or external HDD/SSD), put the notebook in your safe, and memorize your credentials.
You can go further by encrypting a word document
Or finding some other way to password protect your document, AND your storage drive. This depends on the type of drive and your OS. Consult google.
Third,
but surely not last, is LOPA (Layers of Protection Analysis).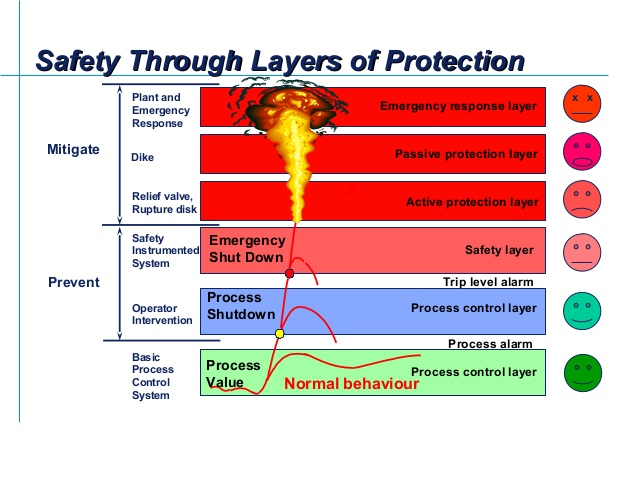
Think of a cold day, wear layers. Think of a sunny day, hat or sunscreen. Think of a rainy day, raincoat, umbrella, boots.
Think of flying in space, they use 14 layers of protection in a spacesuit!
The writer is a Chemical Engineer, and even in extractions or safety analysis, adding extra layers or stages takes things to another level! That way your protection is more robust, i.e. it can protect against more or stronger threat to stability.
Authenticator Apps
The seemingly most widely supported app is Google Authenticator for Android or IPhone. This is another layer of protection, called 2-Factor Authentication. 2-FA basically is a second password. Preferrably it is in a different place than your other passwords, but it is still pretty extreme to get two safes with different combinations at different locations with different books for 2-FA, but hey, sometimes what you’re securing is worth it.
It's pretty simple for most applications. Write down your secret key (string of letters and numbers). The secret key is given to you by the website. Then hit the plus sign:
then:
Google Auth uses magic Google encryption and a secret key to create a time-dependant, 6-digit number code. Every minute, the code changes, so if some dou*he is standing behind yo oblivious a$$ typing in your passwords, she/he would not be able to get through your security! Near foolproof, as nothing is truly foolproof ahahahh.
Coinbase uses Google Authenticator, like many sites. If you don’t have a smartphone that option is not possible.
There are many ways to implement 2-FA, like text or email, but with any security system, it is as weak as the weakest point of entry.
Imagine if Fort Knox had an unmonitored window in the back you could just smash and pass through. Well, it might work, if you can get past the various forms of visible and invisible electromagnetic spectrum imagery, radar, land, electric and razor fences, laser-triggered machine guns, battalion of police, 20+ ton multi-factor vault door, etc., etc.
They have many ways to slow people down and prevent access. One of the best security measures is to waste someone’s time unraveling a Gordian Knot. For that, use your imagination and your resources to confuse, bore, and complicate things. Think convoluted and redundant, then multiply by 256 for added overkill.
Physical Keys
The last one I will write about in this post is a physical key for securing digital assets. A prime example of this is a Yubikey.
Make sure what you’re using is compatible with the key, which looks like a USB drive. It is a USB drive but it’s sole purpose is to hold a keychain of secrets. Yubikeys can be custom made for a specific thing, or you can get a fancy Yubikey 4 or NEO for a variety of uses.
For example, a Yubikey NEO can use NFC (Near Field Communication) as a means to deliver a password. That means that you could even use it to open a real door (with NFC key readers), or anything that is compatible with NFC and Yubikeys. I know that many phones can use NFC, too, and they are frequently linked to bank or credit accounts to make payments with your phone.
If you use a difficult password (with multimedia backups), Google Auth behind a phone login key, and a Physical Key, someone would have to steal your password, your phone, your phone’s password, and a physical key from your cold dead bo-- I mean your hand, to get to your online assets.
That is based on the assumption that you have it on a website who has better security than you.
I will talk about some of the basic ins and outs of offline storage in another post, later.
I hope this post has gotten you further in your knowledge to protect your crypto assets. Post in the comment section for suggestions or questions.
Find us on Facebook or here on Steemit @cloudconnect
Peace

Thanks for the security guides articles this will help a lot of new online user . Cheers
NP @dylen, it's not super advanced but hopefully it will get people from zero to basic security! Thanks for reading!
To all traders out there seeking for a good trading strategy and have been going through difficulties in winning trades, I will like to share with you all a solution to your problems by introducing you to an amazing trading strategy and tool I was also introduced to, which has won me thousands of dollars lately.As an IPM investor I have made over $452000 in my first quarter, been the most secure trending investment .contact me and i will show you the secret and strategy also i will assist you for free contact me via my e mail ([email protected]).This is a top secret you need to learn for a good Payout. I guarantee you 98% ..Regards.
That is very nice of you...willing to share some of trading knowledge that might help other steemit user who do trading...Im sure some of them would interested with your offer Thanks..
thanks for sharing this valuable information with us and keep sharing like this buddy you are doing well @cloudconnect
asalam alejkum brother! Kyale? haha We are doing well, shug corea thank you for reading! I hope the little Urdu I learned in a Pakistani Kitchen and romanized into latin characters translates well :P
Health and Happiness to your family!
Hi, great post, have followed you. What do you think of the current state of the Bitcoin market?
It's very interesting, we have taken a short pause on our public TA, but I think it's gathering strength. Im overall bullish on it. Definitely another major correction below 9k is possible before more local ATHs and new ATH, but I'm feeling 20-40k before Fall
Thank you for reading, @cryptoissweet!
Thanks for the heads up on these security tips, keep it up i resteemed this
Thank you for reading and your encouragement, @youngjerv!
Fantastic article! I've followed and up-voted your post i look forward to your future content!
For info and technical and fundamental analysis of Crypto's, an insight into how the whales manipulate the market and how to get involved in an exciting 12 month millionaire challenge we've recently started, check out @cryptobroye :)
You got a 4.81% upvote from @buildawhale courtesy of @cloudconnect!
If you believe this post is spam or abuse, please report it to our Discord #abuse channel.
If you want to support our Curation Digest or our Spam & Abuse prevention efforts, please vote @themarkymark as witness.
You have received an upvote from @nicestbot. I am an automated curation bot trying to make minnows happy.
Good
Thank for sharing info
You the best
Thank you very much @sulaisteem! Thank you for reading
Yes you welcome
Thanks for sharing that valuable information...
Thanks so much, enough information to keep these hackers away