Choose your best two-factor authentication method

Security is always a big concern when it comes to protect individual's personal online credentials. The war between hackers and security experts remains endless. If security experts always explore new ideas to increase the protection by using various new security methods then hackers always find new ways to breach the security.
Earlier single factor authentication was most widely used to login with your emails, hardware devices, many website portals and still commonly used by many users. One big problem with passwords is the fact that users reuse them and hackers know this, so once they steal an authentication credential for one compromised account, they will attempt to use it to break into the victim's other services. Users also choose weak passwords, which leaves them open to hackers using readily available password cracking tools. Although it is the weakest method but still commonly used by non-tech savvy people.
Types of 2FA Authentication Methods
- SMS 2FA
- Authenticatior APP/TOTP 2FA
- Push Based 2FA
- Universal 2nd Factor (U2F) 2FA
SMS 2FA
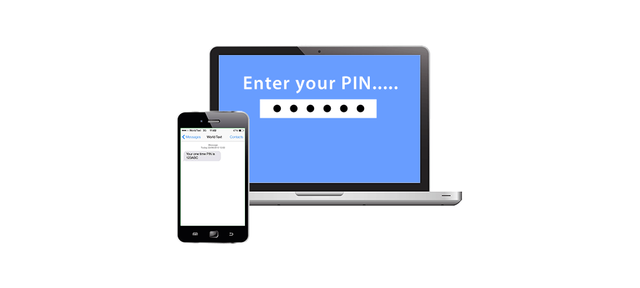
SMS 2fa is used to login to your portals through sms. Website asks users to put their mobile number with login credentials. After enabling user always has to put one time password (usually of 6 digit code) along with the username and password. It is a very popular option for sites to implement, since many people have an SMS capable phone numbers and it doesn’t require installing an app. It provides a significant step up in account security relative to user’s login credentials. This method have some limitations.
Limitations
- Phone Number can be shared by the portals
- Some websites can use client’s 2FA for others purposes like marketing, conversation tracking, and password resets.
- Can’t login if phone is dead or stolen or sometimes can’t connect to a mobile network while travelling.
- SIM Porting Attack
Time Based 2FA

Limitations
- Same copy of Shared Secret key kept with the service provider like crypto exchanges where users have registered . If attackers manages to attack on user’s exchange then he/she can completely compromises your authenticator 2FA.
- Shared secret key is not stored in the form of cryptographic hash.
- Phone lost or dies worries
- If your don’t have backup of your recovery codes or printed copy of QR code then you can loose your account permanently.
- Could be incovenient if user frequently use different computers, to unlock your phone, open an app, and type in the code each time.
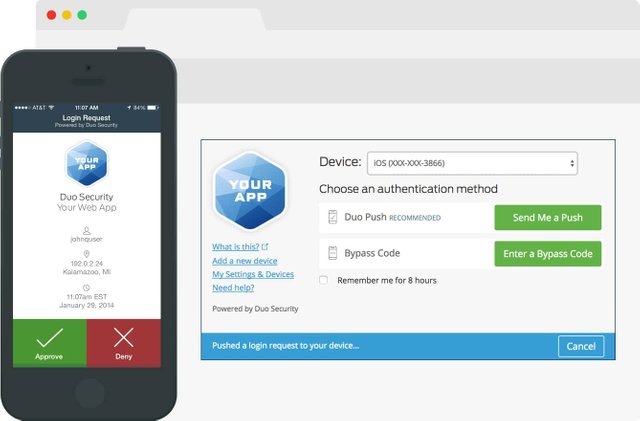
Push Based 2FA
Limitations
- Requires internet all the time while logging
- Not standardized by all.
- Device must support the installation of mobile application
Universal 2nd Factor (U2F)
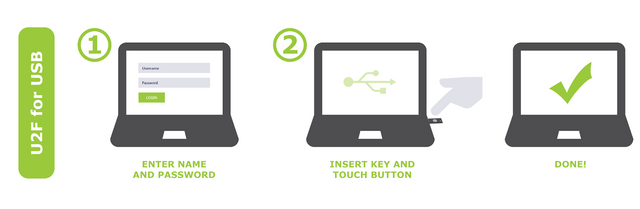
U2F over other 2FA
- Strong two-factor authentication using public key crypto that protects against phishing, session hijacking, man-in-the-middle, and malware attacks.
- Unlimited usage in that an unlimited number of accounts can be protected by one single device.
- Easy to use with all popular browsers with no codes to re-type and no drivers to install.
- Allows users to choose, own, and control their online identity. Each user can also opt to have multiple identities, including anonymous, with no personal information associated with the identity.
- A U2F Security Key generates a new pair of keys for every service, and only the service stores the public key. With this approach, no secrets are shared between service providers, and an affordable U2F Security Key can support any number of services.
- Open standards provide flexibility and product choice. Designed for existing phones and computers, for many authentication modalities, and with different communication methods (USB and NFC).
Limitations
- Not Widely available because of new technology
- Not completely supported by all the popular browsers except chrome
Top 3 U2F hardware devices
1 Yubico [Yubikey 4 Nano]
2 Thetis [Fido Universal]
3 Kensignton [VeriMark USB Fingerprint]
To listen to the audio version of this article click on the play image.

Brought to you by @tts. If you find it useful please consider upvoting this reply.
You got a 3.49% upvote from @postpromoter courtesy of @text2crypto!
Want to promote your posts too? Check out the Steem Bot Tracker website for more info. If you would like to support the development of @postpromoter and the bot tracker please vote for @yabapmatt for witness!
Congratulations @text2crypto! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Do not miss the last post from @steemitboard:
Vote for @Steemitboard as a witness to get one more award and increased upvotes!