Compartmentalized Conspiracies: Would Anyone Have Talked? (Parts 3-6)
Back to read Parts 1-2
Part 3: Examples of Unwitting Accomplices Who Find Out Later
This entire thought experiment includes conspiracy theories that are not recognized as accurate by mainstream reality. One would only consider people involved as unwittingly accomplices if there was indeed a conspiracy, and one saw enough evidence for its theory to prevail.
Throughout this essay, I do not describe these scenarios as formal accusations. I find most of these theories fairly compelling, but near-certainties are rare in my book. I’m just attempting to organize some patterns to help us categorize and deduce what strategies may be most attractive, effective, and likely for conspirators.
Out of the 130,000 people employed on the Manhattan Project, most would not have understood even a general sense of what they were helping build. This world wonder example of compartmentalization has the most patriotic motives aiding its silence. But the reveal came after only four years, and we learned a great deal more within decades. So I presume there are countless interesting stories about the realization process for unwitting accomplices in this chapter of history.
I also haven’t studied the “moon hoax” theories enough yet, and those projects are still more deeply locked down within the national security state. After all, I don’t even have limited certainty regarding what happened at The Pentagon, 15 miles away, 18 years ago, in broad daylight.
JFK’s assassination is another topic which I know is so vast that I have only skimmed the surface. You might be most likely to find someone who spoke out after realizing they were an unwitting participant in the cover-up for that coup. But it seems likely that Lee Harvey Oswald himself was an unwitting participant turned patsy, and he did publicly declare his innocence. Perhaps he began as a witting accomplice in some cover story he was given by his handlers, but then he was framed to look like the president’s lone assassin.
RFK’s assassination was likely a much thinner conspiracy pinned on Sirhan Sirhan, who claims he is innocent, with details which make him a patsy or unwitting accomplice. It appears that the available evidence proves that he is not guilty of murder, and this alternative history should no longer be considered a “theory”.
We now know the Gulf of Tonkin Incident that kicked off the Vietnam War was based on “skewed” intelligence from the National Security Agency (NSA). “Senior officials at the Agency, the Pentagon, and the White House were none the wiser about the gaps in the intelligence.” “President Johnson and Secretary of Defense McNamara treated Agency SIGINT reports as vital evidence of a second attack and used this claim to support retaliatory airstrikes and to buttress the administration’s request for a Congressional resolution that would give the White House freedom of action in Vietnam.” In the 2003 documentary, The Fog of War, McNamara “concedes that it now appears this attack didn’t happen but claims that he and Johnson honestly believed that it did at the time.” This skewed intelligence is not widely recognized as a conspiracy. But from my point of view, he admits to being an unwitting accomplice of starting to cruel war on false pretenses.
After the Waco siege in 1993, a “grand jury, in its five-count indictment against Johnston, alleged that he hid evidence about the FBI’s use of pyrotechnic tear gas during the 51-day standoff between federal agents and Branch Davidians, and lied to federal investigators and grand jurors during the investigation of the standoff, which ended with a fatal fire on April 19, 1993, killing some 80 Davidians.” Perhaps it’s worth searching related reports for any internal whistleblowing by unwitting accomplices involved in the siege or the cover-up.
A whistleblower did take the stand in the McVeigh trial for the OKC Bombing claiming “that the lab where the bombing evidence was examined was contaminated beforehand with explosives residue.” I think it is likely there would have to be some unwitting accomplices in this case related to the cover-up. (I’ve just found another rabbit hole that’s new to me, Cory Snodgres, “CIA Black Ops Whistleblower: The OKC Bombing was the FBI/ATF Destroying Files”.)
There are also many historical cases where massive corporations have conspired to damage the health of the public and/or the environment. Many of them include stories of unwitting accomplices who turn into whistleblowers.
I don’t know of any unwitting accomplice whistleblowers for the 9/11 attacks themselves. There were many unwitting accomplices within the White House, NORAD, the pilots running drills, etc. You should be able to find some accounts in the 9/11 Commission Report documents. There’s one famous close call in Michael Springmann, the former head of the American visa bureau in Jeddah, Saudi Arabia. It sounds like if the CIA had been more honest with him, he might have turned into an unwitting accomplice instead of getting fired and blowing the whistle.
Similarly, there must have been unwitting accomplices in the EPA cover-up of the extreme health hazard to first responders, and I don’t know if any have spoken out. But we know this because Cate Jenkins was too tough to be unwitting, and blew the whistle. “Beginning shortly after the attack, and continuing for years afterward, Dr. Jenkins attempted to bring the EPA’s faulty and fraudulent air quality testing practices to the attention of anyone who would listen.”
The two co-chairs of the 9/11 Commission, Thomas Kean, and Lee Hamilton, later said it was set up to fail, so they eventually became witting accomplices of the crime’s cover-up. Max Cleland also came out saying the investigation was compromised. Presuming these three were not knowing members of a cover-up before they joined the commission, then they fit this category.
Colin Powell’s “high-profile February 2003 prewar presentation to the U.N. Security Council included now-discredited claims…” “Powell said he relied on the CIA to help develop his U.N. presentation but that he was not aware at the time that “much of the evidence was wrong”.” FBI Director Robert Mueller also spread this “intelligence”, presumably another unwitting accomplice of starting multiple wars on false pretenses. Intelligence agents and department heads in all 17 agencies who rubber-stamped the “skewed” “intelligence” were accomplices. Members of Congress who approved or funded military engagements were presumably unwitting accomplices, but many organically aligned with the conspirators’ larger goals/objectives. The media also holds significant responsibility, as the conspiracy also requires their complicity to succeed, unwitting or not.Establishment think tanks prepare white papers to justify and execute wars, making them presumably unwitting accomplices too. Though some might be witting accomplices, like the Project for the New American Century (PNAC) — whose members had great influence at the time — and their famous pre-9/11 roadmap hypothetically mentioned how it would be easier to build their vision after something like a “new Pearl Harbor”. Their hands might not be as dirty, but they often play critical roles in convincing the public to accept and approve of the conspirators’ narratives. And perhaps some think tank employees have been unwitting accomplices by producing intelligence which insiders can actively take advantage of while profiting on foreknowledge of wisely targeted chaos.
And there’s another broad framing outside of any organizational chart. Voters are definitely witting on some levels and unwitting on others. But that doesn’t let them off the hook, because people should not consent to these unaccountable institutions at all if we have no idea what the intelligence agencies really do. Giving voters informed consent seems like it might contradict such agencies’ modus operandi.
But evidently, voters have not sent strong enough messages to end these wars. 62 million people voted to reelect Bush in 2004. So if someone believes that we have representative governance, then they might also consider those U.S. voters accomplices in these wars.
But millions of these unwitting accomplice voters over the years have spoken up and protested after realizing how the conspirators’ skewed intelligence and demands for patriotism (cover stories) had fooled them into endorsing and thereby enabling mass-murder. This set of whistleblowers has no privileged information up its sleeve.If any of the other major terror events and mass shootings did, in fact, involve patsies, then those would also be unwitting accomplices if they didn’t know they were involved with anything nefarious. Almost all in the known candidates in the past two decades were quickly killed or mentally neutralized.
Part 5: Questions About Tier 1
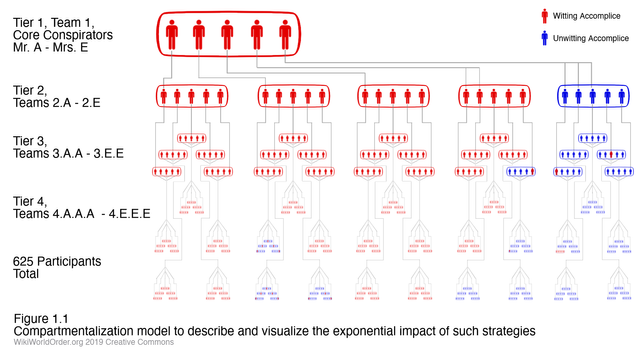

In this model, Tier 1 consists of a team of five core conspirators, Mr. A through Mrs. E, with full knowledge of “The Big Plan” they are orchestrating. Each of them will directly control or strongly influence five more accomplices/participants in a team. After Tier 1, each accomplice could really be either witting or unwitting, depending on what is needed and/or what is possible.
This might depend on the scale and diversity of the overall operation. For example, some small plots might not have any unwitting participants. Huge operations might need primarily witting accomplices filling the first few tiers, but varying ratios of witting and unwitting accomplices can work lower in the chart.
In this model, Mr. A controls Team 2.A on Tier 2, which has five members including at least one leader, to be held responsible for the team’s objectives. Each Tier 2 member, or their team as a whole, maybe witting or unwitting accomplices. Each of the other four core conspirators in Tier 1 manage similarly structured teams.
In reality, a plot’s organization would not be designed based on some magic team size. It would be influenced far more by the needs and available resources of the operation. Each team’s size would vary on a task-by-task basis, like with most organizations. Maybe two or three accomplices team up to take care of smaller tasks. Maybe other tasks simply cannot be done without 10 or 20 people in one place. Depending on the situational context, the team’s size might inform whether to use witting or unwitting accomplices and how to manage them.
The planning process would also include tough puzzles of how to further compartmentalize tasks until they are small enough to secure, or backed up with enough contingency plans.
In this model, each team/cell/compartment of five accomplices are all aware of each other, at least as much as needed to collaborate on their compartment’s tasks. So the Tier 1 team of core conspirators are all aware of the plot’s big picture, and any critical details they all need to know.
Lower tiers likely include teams of witting accomplices who would be aware of each other, and everything they need to about the team’s sub-plot, but not the bigger picture. Lower tiers likely also include teams with unwitting accomplices, who would ideally have a cover story that plausibly exists outside the context of the entire plot.
The division of labor among the Tier 1 core conspirators (Team 1) would always depend on a case by case basis. Every large organization faces challenges in completing complex projects. Dividing up tasks can be similar to most common business management strategies, where a hierarchy of participants are also expected to generally follow orders and be held accountable.
It seems that Team 1 must first clarify what their primary and secondary objectives are, and generally how they might securely pull it off. Only then would it be worth discussing roughly how to compartmentalize the various sub-projects. Once enough of that information is clear, then they would be more prepared to split up specific tasks, responsibilities, and entire sub-projects. Team 1 presumably delegates most of their deliverables to lower Tiers.
So operations would need to be well managed like any other business. Compartmentalization is just added on top as an additional strategy with its considerations. Maximum compartmentalization is not necessarily ideal to accomplish the mission and keep it secret, so it wouldn’t always overrule common operation designs. But the strategy might be used wherever specific risks exist to create an extra firewall, increase plausible deniability, and ensure that all witting accomplices feel secure and confident in success.
It seems like if it is done right, heavily using a strategy of compartmentalization would significantly increase the planning time in advance of the operations. It would also increase some communication times between the network of teams, checking in with different handlers, etc. For intelligence agencies used to it, this is just part of the delays and costs demanded by tradecraft used in their covert operations.
The basic organizing strategies which make sure things get done are shared by both businesses and compartmentalized conspiracies. But in business, everyone in the company — and the world — know the CEO, mission statement, growth plans, stock price, etc. And in the compartmentalized model in Figure 1.1, there are 620 accomplices organized by only five core conspirators who know the whole plan and only five more accomplices who can even identify them.
Part 6: Questions About Tier 2
I do imagine teams throughout the whole network as having one or two leaders. They are ultimately responsible and accountable for their team’s duties to other teams or handlers above and below them. I presume this because hierarchies are very common when people or businesses organize. Similar to other factors above, there are countless ways to design most organizations, so each team should be customized for each specific task.
In Figure 1.1 above, the intent is to show that Mr. A (Core Conspirator A) is managing/controlling one lead member of Team 2.A. This team leader would be in private contact with Mr. A, but the rest of the team would not be aware of Mr. A’s existence.
With this method, Mr. A of Tier 1 privately passes on key information, instructions, and commands to the leader(s) of Team 2.A. The team leader passed on instructions intended for the members of their team and completes any other commands ordered for them alone. If the team leader runs into any issues or successfully completes their tasks, only they would be able to reach out to Mr. A. (But Mr. A can reach out to Team 2.A in a contingency situation.)
Depending on the people and the job, some teams could have a couple of co-leaders. Or the team could have a primary leader who doesn’t realize there is a second/backup leader also being directly steered by the core conspirator above them.
Again there are countless variations possible. In a different plot, using “Variation #1”, Mr. A could be a known member of a few other heavily trusted teams. So instead of relaying instructions to Team 2.A through an intermediary, he might be the known leader of that team. He may be there under his real identity or a cover identity, as needed. But he would still presumably omit or downplay the core conspirators' bigger plans from Team 2.A.
I do think this Variation #1 an equally reasonable default model for laying out the entire structure of a hypothetical organization. This strategy definitely removes one layer of protection/firewall for the core conspirators. But it also gives them more direct control over the second tier. So a decision to use this strategy depends on the situation’s security needs, but also the core conspirator’s management style, or some strategic value of their identity (real and/or cover).
In this example, if Mr. A privately manages the leader of Team 2.A, then only five people can identify him. That’s the four other Tier 1 core conspirators, and the Tier 2 team leader. But if Mr. A actively leads the team himself, then 8 people can identify him. Jumping from 5 to 8 here is a 60% increase in direct exposure risk in that spot. So they might need to add extra contingency plans, quality control, and blackmail portfolios to counterbalance the overall risk for The Big Plan.
So once again, there are many design options to fine-tune different aspects of an operation.
But if Mr. A has duplicate roles, we would have to update the model’s math of calculating how many total unique participants are involved. And we could evolve it to become ever more complex, spending months classifying dozens of different general strategies, and making relatively arbitrary guesses to weigh the likelihood of their use in different categorized scenarios.
I think this direction would only take the model further from reality, without producing more statistical value, higher resolution, or actionable results. If my simplified model cannot help convince Skeptics that such organizations are plausible, then I doubt a more convoluted model would tip the scales for them. Because it will always just be a generalized, simplified model of an infinitely complex chaotic system of human relations.
With the catastrophic anthropogenic global warming models, I would prefer if society focused the collective resources towards implementing the applied science we already have, instead of pumping it into theoretic questions that we probably won’t be able to answer this century. It is my position that we would have saved almost two decades of fossil fuel use if the government had simply been buying and installing solar panels for the past three decades, using a majority of the environmental funds that appropriated to research the nested climate change theories.
This strategy preference is a result of my unique blend of bias, but given the evolution of this discussion, perhaps the model has far greater value in establishing consistent definitions for use in discussing specific conspiracies. Such frameworks can be useful to researchers, providing a more standardize layout to describe whatever they uncover. If these concepts become well-defined and accepted by most people, their use could generally improve communications across one of the most prominent and damaging reality-bubble-divides, which catalyzed an entire “alt-media” counterforce.
The most secure way to compartmentalize would be to ensure that most teams do not knowingly interact with each other, or are even aware of each other. Ideally, Team 2.A shouldn’t even know Teams 2.B through 2.E even exist. I think this rule is part of the default modus operandi for compartmentalization, and it is the intended rule for this model.
But Team 2.A would collectively know about the teams it managed, 2.A.A through 2.A.E. Depending on the security needs and divisions of labor, individual members of Team 2.A might be the only ones with full knowledge of a lower team they manage. Or the whole team might need or want to work more transparently to manage their collective responsibilities.
If a plan is highly compartmentalized, then there are likely many situations that would require separate teams to work in parallel — or even together. They can work together by carefully accepting a specific compromise of maximum security, allowing one member from each team to be in contact. Alternatively, a separate team in an entirely different branch of the operation could facilitate communications, creating an extra firewall.
For example, perhaps some of the Tier 3 teams managed by Mr. C are essentially liaison teams. These would be witting participants simply transferring [coded] information between the teams/cells/compartments. Picture the movies where the CIA agent calls some funny number, speaks some code phrases, and an intended message is passed to their handlers. The call center agent receiving the field agent’s call does not need any context about any operations to accurately and securely move the information through the fully compartmentalized organization.
The CIA does not have a monopoly on tradecraft. A plan without the full infrastructure of a government agency could have liaison teams with members who each a responsible for handling contacts between a few other teams. Those liaison accomplices might — or might not — need to know the contextual details about the other teams, depending on the situation.
So communication between compartmentalized teams increases the complexity of the operation, sometimes by creating extra teams to facilitate those logistics. Similarly, perhaps other teams under Mr. C’s management are responsible for quality control. Such quality control teams could collect independent intelligence on the progress of primary teams, so the core conspirators can verify the work being done throughout the operation, and maintain assurance that it will succeed. Perhaps such teams would also be primarily responsible for neutralizing any leaks, or cutting teams loose if needed.
There would also sometimes be a need for entire contingency teams. As with military operations — and football plays — most projects include steps which are not entirely controllable and predictable. For many sub-projects and individual tasks, a backup plan can be developed in parallel. If a team running Plan A fails, then the conspirators can quickly pivot to activate Plan B using the backup team’s completed work. So some steps might be prepared more than once, from different angles, with different teams. Such teams could be aware or unaware, as needed. The greater the risks to witting participants, the greater the need for redundancies.
All accomplices in Tier 2 and lower may be witting or unwitting participants. Unwitting assets would have an understanding that they are working on something else. That cover plan could be something completely different than what’s happening, or even the exact opposite. Some unwitting accomplices might just be doing their job, performing fairly vanilla transactions.
Witting accomplices come in different flavors too, but Tier 2 and lower would never know the entire plan. It’s possible for Mr. A to explain some aspects of the larger plan to the team leader below him, so they logistically accomplish their responsibilities. Alternatively, Mr. A might need to vaguely explain some long-term goals of The Big Plan in order to motivate and impassion their team leaders to effectively manage sub-projects.
Perhaps Ms. B manages some witting accomplices to whom she also feeds a cover story. These people know that they are involved with something nefarious, illegal, risky, or at least confidential. But their sub-project may be framed in a totally different way to avoid sharing any additional knowledge about The Big Plan.
This could be similar to a bank heist plot where a team risks everything inside a bank without even knowing they’re really there to get some politically motivated document out of a box. Or when officials help cover-up for a rogue faction “for the good of the institution”. They are knowingly part of a conspiracy (e.g. the cover-up), while unaware of any larger conspiracy (e.g. the war).
Part 7: Other Model Clarifications
The more you compartmentalize, the more secure an operation may be. That does not necessarily make it a better operation. For example, “infinite security” is not an ideal goal.
Core conspirators — and accomplices on any level — would only recruit and select team leaders they can trust to get the job done and keep any secrets necessary. This is definitely another assumption in my model, and think it is generally true of most human organizing. Accomplices would also only be recruited if conspirators had confidence they had the moral fortitude — or lack thereof — to complete all their specific tasks.
As with any large organization, those making decisions at the top can have a whole spectrum of involvement with the gritty details of operations. Some CEOs read every report in the company and like to micromanage everything. Others stick with just delegating tasks to people who they expect to get the job done right and inform them if anything unplanned happens. Such heavily trusted accomplices could be like Frank Underwood’s right-hand-man in the TV show, House of Cards. Doug Stamper is Frank’s old friend and ally who almost intuitively knows how the core conspirator would make decisions in their shoes. Other heavily trusted accomplices could have a proven record of meticulously following their given orders, which are skills developed throughout military training.
When additional reassurance is needed, Mr. A could delegate separate quality control teams with equally important responsibilities of double-checking the work. If this is too much work or exposure for Mr. A, then he might just find a more competent leader for Team 2.A who can run both the main operation and also it’s separate supporting teams. If nothing else changed, then the chart would be updated to show Team 2.A with only one member. The right-hand man would responsible for tasks he can do alone, plus managing whatever teams needed (and possible). But even with a “team” of one, this compartment still provides an extra layer of firewall and plausible deniability, which are the main advantages of compartmentalization.
No matter the flavor, most heavily trusted accomplices would be witting. But below them, the general lack of preferences for blending witting and unwitting applies once again.
Model Parameters
I can think of no logical restriction on how many tiers deep an operation can go. Similar to individual team sizes, the number of tiers might be one useful unit of analysis. But I do not think these variables would be where any real-world operation design process begins or gets stuck.
For the sake of this compartmentalization model, I used a fixed size for each team/cell/compartment. This is just because it is dramatically easier to calculate and visually illustrate the strategy’s exponential impact.
I used the team size of five for how many motivated accomplices could reasonably keep a secret. I wanted to choose a number low enough for others to believe, even if they have the opposite confirmation bias delivering assumptions that conspiracies are rare or impossible.
One of the goals of this thought experiment was to extrapolate the compartmentalization model from a believably small team size all the way to the largest known conspiracy, around the orders of magnitude above 100,000 accomplices.
Appendix A: Trickle-Down Omissions
Omissions (neglected or withheld information) can be observed to trickle downhill, or layered like a nesting doll. For this thought experiment, let’s use a cartoon-level simplified version example of the Manhattan Project conspiracy. (This is not an attempt to make an accurate or even realistic organizational chart.)
Imagine if Mr. A was one of two core conspirators managing the top-level scientists. He would likely omit the fact that these weapons could effectively hold the world hostage. This means he would neglect to mention it when instructing his heavily trusted leader of Team 2.A — at least so it is not prominent in their mind.
Even if the Team 2.A Leader implicitly knows this, or figures it out, it’s definitely not part of his team’s mission. Leader 2.A would, in turn, omit any inkling they had about these risks when working with their team and all others.
So let’s presume Team 2.A knows that they are building nuclear weapons. But they never bring up nuclear weapons when collaborating with the Tier 3 Teams (3.A.A — 3.A.E). Instead, the Tier 3 Teams believe they are just building cool new conventional offensive weapons that are top secret. There might also be teams focused on allegedly defensive weapons research. But The Big Plan is now already inconceivable to most minds in Tier 3, because conventional weapons are very unlikely to alter the world order.
Then below them, there could be Tier 4 Teams (4.A.A.A — 4.A.E.E) who only work on the pure physical, chemical, and biological research. They would have no idea what types of technologies were being actively developed or deployed but might have inklings. They would rarely have any reason or ability to suspect a shift in the world order.
Then we could generalize the Tier 5 Teams (5.A.A.A.A — 5.A.E.E.E) as perhaps grounds maintenance staff, chefs, guards, etc. They would have even less reason or ability to suspect a shift in the world order.
But the big-picture cover story which everybody shared, was that they were developing classified military science aiming for peace. When a society’s language and logic are so inherently self-contradictory and Orwellian, then many cover stories that can mean anything to anyone.
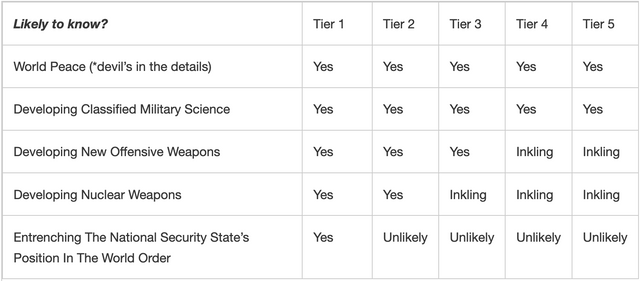

Of course, U.S. citizens did not need to know, so they are not included in this table.
Appendix B: Book Recommendations
To dive deeper, you should definitely look for any public documents that intelligence agencies use to teach about compartmentalization, need to know, whatever they call it. Also, dive into first-hand accounts from participants in Manhattan Project. It’s been over a decade since I’ve read such books focused on the topics of compartmentalized organizations. But here are two suggestions with some gold:
National Security and Double Government, by Michael Glennon
“Why has U.S. security policy scarcely changed from the Bush to the Obama administration? National Security and Double Government offers a disquieting answer. Michael J. Glennon challenges the myth that U.S. security policy is still forged by America’s visible, “Madisonian institutions” — the President, Congress, and the courts. Their roles, he argues, have become largely illusory. Presidential control is now nominal, congressional oversight is dysfunctional, and judicial review is negligible. The book details the dramatic shift in power that has occurred from the Madisonian institutions to a concealed “Trumanite network” — the several hundred managers of the military, intelligence, diplomatic, and law enforcement agencies who are responsible for protecting the nation and who have come to operate largely immune from constitutional and electoral restraints. Reform efforts face daunting obstacles. Remedies within this new system of “double government” require the hollowed-out Madisonian institutions to exercise the very power that they lack. Meanwhile, reform initiatives from without confront the same pervasive political ignorance within the polity that has given rise to this duality. The book sounds a powerful warning about the need to resolve this dilemma-and the mortal threat posed to accountability, democracy, and personal freedom if double government persists. This paperback version features an Afterword that addresses the emerging danger posed by populist authoritarianism rejecting the notion that the security bureaucracy can or should be relied upon to block it.”
The Great Train Robbery, by Michael Crichton — classic tale of a meticulously planned conspiracy
Appendix C: Movie Recommendations
Here are some of my favorite movies and shows which dramatize some strategies which logically work for conspiracies. They might help you better visualize how such strategies are employed.
Secrecy (2008) — only documentary on this list
Executive Action (1973) — the most compelling visual illustration of how the JFK conspiracy might have occurred, YOU MUST SEE
Rubicon (2010) — best illustration ever of five powerful men with a national security conspiracy
Nick of Time (1995) — unwitting turned forced-witting
Shooter (2007) — unwitting accomplice turned patsy
The Parallax View (1974) — quasi-witting accomplice
The Manchurian Candidate (1962 and 2004) – Project MKUltra research-related, mind-control level unwitting accomplices
The East (2013) — a private intelligence operative infiltrating anarchist group
The Good Shepherd (2006) — insightful dramatization surrounding birth of CIA
Wag The Dog (1997) — “Shortly before an election, a spin-doctor and a Hollywood producer join efforts to fabricate a war in order to cover-up a Presidential sex scandal.”
The Americans (2013) — TV series with tons of examples of older intelligence tradecraft
The Great Train Robbery (1978 or 2013) — lovely film adaptations
Eyes Wide Shut (1999) — example of an esoteric recruiting process into a deeper layer of society