Osueta – A Script for OpenSSH Server Side Attacks

So what is this Osueta script all about?
Osueta is a powerful python script used for exploiting the OpenSSH vulnerabilities through User-Enumeration Time based attack methodology. With a User-Enumerated Time based attack, the attacker searches for usernames on a target server. The attack is unique in the sense it makes the brute force attack more effective by utilizing efforts on finding just the passwords for the identified usernames.
OpenSSH is a network level security suite that uses Secure Shell (SSH) protocol to secure the network communication through different encryption techniques. The SSH protocol was introduced to secure networks from Man in the middle (MITM) and Eavesdropping cyber-attacks. Since OpenSSH server uses username and a password based authentication protocols, Osueta becomes handy in exploiting OpenSSH server vulnerabilities and finding the usernames on the target server.
Installing Osueta
In Linux, Osueta can be installed through the following commands.
apt-get install python-ipy python-nmap pip install paramiko git clone https://github.com/c0r3dump3d/osueta.git
Once Osueta is installed, change the directory to osueta either by following the osueta directory path or by copying the Osueta folder to the Desktop and redirecting to osueta using the following commands.cd Desktop cd osuetaLet's see Osueta in Action!
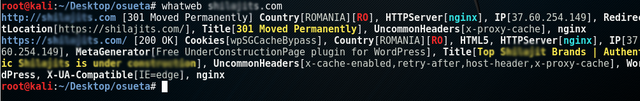
To see Osueta into action, we need to find out the target IP address. This can be done by using the following command. The <url> in the following command is the target service url hosted on the target server.
whatweb <url>The above command helps in finding the server IP address along with other useful information as depicted in the following screenshot.
After successfully finding the server IP address, use the following command to find out the username on the target server.
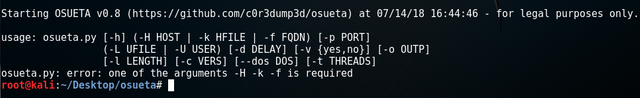
python osueta.py –H <IP Address Here> –U pp –p 22Here the H <IP Address> is the server IP address. The U represents random username. The p is the port number used in the attack. In the given case, it is 22. When the command is run, Osueta checks if the port is open or closed. If the port is open, it detects the service banner to know the SSH version. Afterwards, Osueta tests random usernames by analyzing time delays. A list of usernames can also be fed into Osueta to check if the username exists at the server. If there is a time delay, it means the username exists because the server is busy in generating and comparing the hash of a very long password provided by Osueta.So what else can it do?
Osueta can also be used to launch a Denial of Service (DoS) attack using the following command../osueta.py –H <IP Address Here> –p 22 –U pp –v no –dos yesThe syntax “dos” represents the Denial of Service attack.What Bunny rating does it get?
The tool is pretty useful for red teaming exercises, however is only useful for OpenSSH servers that support such time delay vulnerabilities. As a result we have decided to give this tool a very respectable rating of 3.5 bunnies.
If you would like to learn more about ethical hacking and such techniques, we have an exclusive course with a 95% discount HERE
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.
Posted from my blog with SteemPress : https://latesthackingnews.com/2018/07/15/osueta-a-script-for-openssh-server-side-attacks/